The growing reliance of operational processes on IT demands a greater understanding and control of your organization’s digital assets. This is especially critical when organizations heavily rely on IT and consider digital assets to be the most critical resources for an organization. The rapid adoption of emerging technology, combined with the increasing reliance on modern IT tools results in several IT-related issues that can result in failed IT audits.
What is an IT audit?
An IT audit is a review of your standard IT operational procedures, practices, and policies and an in-depth analysis of your digital assets. An IT audit also helps you determine whether your cybersecurity measures are up to the mark.
With IT infrastructure being so complex nowadays, organizations can expect any sort of IT audit that focuses on specific aspects of your IT environment. From general IT audits that review the entire IT landscape to risk profile audits that highlight the vulnerabilities in your IT system, there can be a number of reasons you can be audited.
The role of the IT asset manager is crucial in this context, as they maintain accurate records of IT assets and ensure the organization’s digital resources are properly tracked, controlled, and prepared for audits.
Manage Your IT Assets While Saving Money
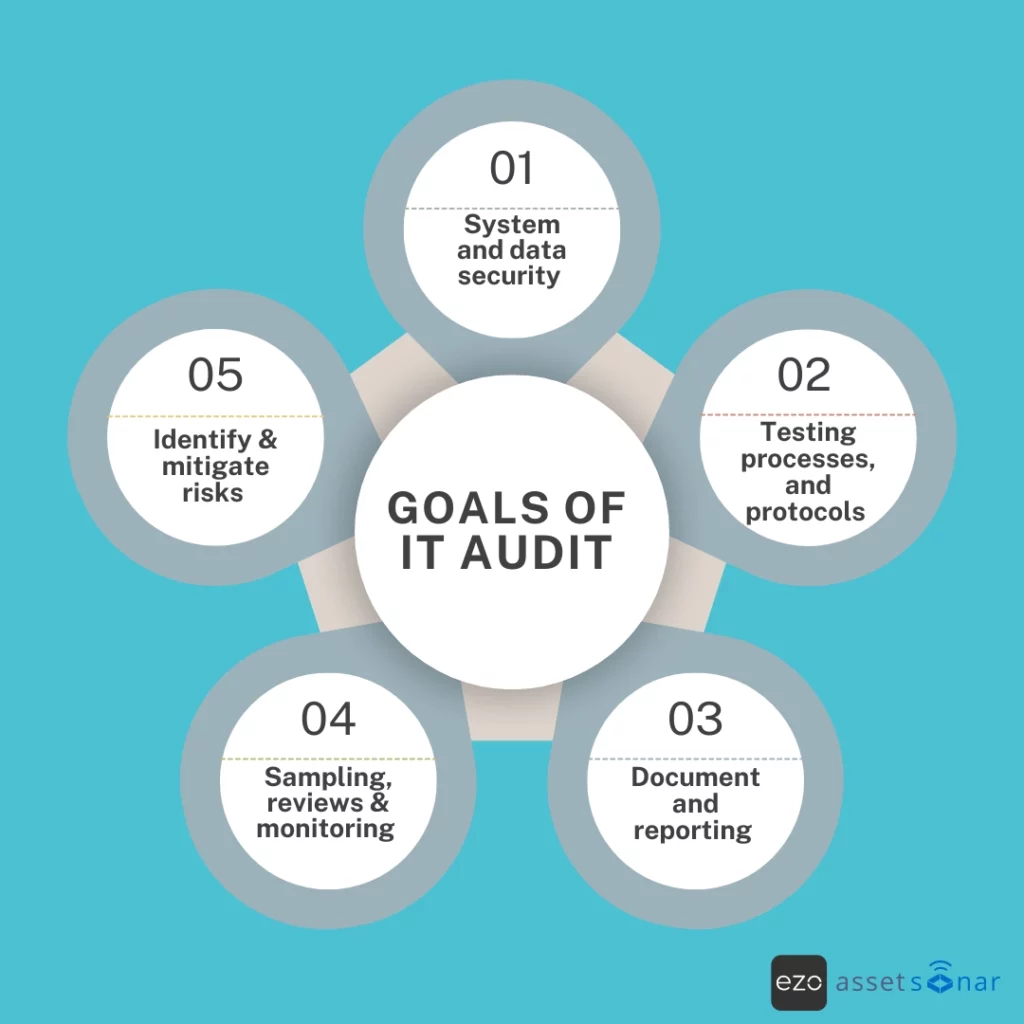
Goals of IT audit
An IT audit ensures IT assets are managed within the set controls. These controls are implemented to protect IT systems from security breaches, comply with regulatory requirements, and align with the organization’s core objectives.
IT audit mainly focuses on:
- Secure data and systems from unauthorized access and threats.
- Test processes and protocols to verify strong control measures are in place.
- Sampling, reviews, and monitoring of current IT processes and their effectiveness.
- Document and report for stakeholders to assess the reliability of the organization’s IT systems.
- Identify and mitigate risks for improved and enhanced IT processes and system controls.
Lack of preparation before an IT audit can result in settlements, true-ups, and most importantly, a lack of productivity and distressed operations. According to the IBM data breach report, the average cost of a data breach was $4.88 million.
Fortunately, there are steps you can take to ensure that you are fully prepared for a potential audit.
Importance of IT audit in the organization
IT audits are important for organizations to keep their IT infrastructure safe, up-to-date, and reliable. Organizations spend thousands of dollars on IT audits to know which IT systems and processes require changes so that they function smoothly and are market-competitive.
A thorough audit helps organizations know exactly the potential risks and their likelihood to occur for any specific IT workflow. Additionally, they also receive audit reports with suggestions included to rectify these risks and implement secure solutions.
For example, while performing an IT assets audit, the auditors identify that the security protocol for one of the servers is weak enough to be attacked easily. They suggest implementing WPA3 as the strongest security protocol for network servers.
Why do organizations need the information technology audit process?
Implementing a regular and extensive IT audit process will help organizations examine their current IT systems and processes.
Through the process, they can identify, resolve, and upgrade to better ITAM software and solutions, resulting in improved governance and control over IT assets. Additionally, they can ensure their digital assets are fully protected from potential cyber-attacks and other security threats.
5 key steps of the IT audit process:
Understanding these steps is crucial to ensure organizations plan, execute, and implement the audit process in an efficient manner. Let’s take a look at:
1. Audit plan
This is the initial stage where the organization plans on the scope, objectives, and methodology of the audit.
Firstly, the audit teams should communicate with employees to establish an audit plan after understanding IT workflows. It is also important to set audit timelines that do not contradict other major business processes.
The next step is to decide who will perform the audit. Large corporations having complex IT systems can opt for external audits. For small businesses, an internal audit is sufficient and a reasonable option.
Lastly, they decide on the type of audits to perform based on the organization’s IT systems and processes. Most audits are divided into compliance and controls assessment.
The compliance audit mainly focuses on whether regulatory requirements are completely met whereas control audits test the processes in place and assess if high-risk activities are prevented or not.

2. Outline steps and timelines
Before the audit begins, penning down important points helps to define the audit scope. This includes areas that need to be audited and the depth to which the auditors will perform the audit.
Sometimes, the organizations decide to run step-by-step audits where the auditor audits one IT process and then moves to the next, and so on. However, organizations can also choose to execute audits for all processes at once depending on their bandwidth and scope.
Auditors also provide detailed timelines for departments so employees can have a clear idea of when their departments will be audited.
3. Perform IT audit
After the plan is finalized, the auditors execute the audit process. They start with testing the controls of IT systems and processes. They can request demos of a process on the system, or select samples to test automated processes such as access controls and transaction processing. They can note down their findings after analyzing the processes.
They also collect evidence to support their findings. They can request interviews with employees within the organization to collect information regarding specific IT processes or request user interface screenshots.
Additionally, they can collect previous audit reports, strategy documents, receipt copies, etc., to fully understand the process and evaluate controls.
4. Audit report
After carefully reviewing IT infrastructure, the auditors compile their findings and suggestions in an audit report.
The IT audit report is a public document that states the auditor’s assessment of the organization’s IT infrastructure.
To begin with, auditors state the efficient processes that the organization follows. Then, they highlight the systems and processes that do not require any changes and are functioning well. The last part outlines the risks identified and suggestions on how to mitigate them.
Potential risks can be due to non-compliance or carelessness of departments. This requires immediate action by correcting specific IT workflow or disciplinary actions if the employee has intentionally breached protocol. Sometimes there’s a high security risk associated with using previous versions or unlicensed software applications.
5. Implementation and follow-up
The auditors also keep track of how well their recommendations are implemented. This is why it is a good practice for department managers to implement their suggested solutions.
8 key points of an ultimate IT audit checklist
1. Notify the stakeholders
Once you have been informed about the audit, let your business partners and all the other stakeholders know about it so no one is caught off guard. All the parties involved should be well-prepared and on the same page.
Your teams and partners should set their affairs in order and be able to provide any documentation upon the auditor’s request. Most of the conducted IT audits are either software audits or risk evaluation audits. For such audits, you can derive relevant information from your ITAM and ITSM tools.
Before the external audit is performed, you should conduct a survey across the organization to find out the common IT-related issues that are likely to arise during the audit. Some common issues that surface include:
- Remote access to the company’s network without two-factor authentication
- Outdated policies
- Lack of a business continuity plan
- Lack of centralized data management
- Insufficient data loss prevention systems
- Legacy operating systems
- Lack of network architecture
2. Prepare your documents
Make sure that all your documents are in a centralized location to save yourself time and inconvenience. This is easily possible if you keep track of all your software licensing and hardware asset details in an IT asset management software. By providing the auditors with all the essential information in one place, your IT audit will be conducted more smoothly.
Along with the software and hardware details, you should also create lists of all your third-party providers and external vendors. You can import these details from your ITAM solution. Other information that should be made available to the auditors is the hardware asset lifecycle information and software usage details, etc.
3. Inventory analysis
Be armed with an in-depth knowledge of your software and hardware inventory. You should also have detailed information about their usage, retirement protocols, and so on.
If you don’t have a proper asset retirement protocol in place, then worn-out or depreciated hardware can become a serious liability for you. You will also have to provide the access list to those assets. You can easily derive this information from your ITAM tool.
4. Written policies and procedures
In order to avoid scrambling during IT audits, your team should have detailed documentation of all the administrative policies and procedures that are practiced in the organization.
Make sure that all the information regarding these policies is clearly documented and is placed at a centralized location for easy access.
5. Information security plan
In order to avoid unexpected downtime or incidents due to cybersecurity concerns, you should always have an information security plan in place. Any organization registered with the Security Exchange Commission is required to have a written information security plan available.
If you have this written plan, then you can regulate standards for your organization to help prepare yourself for cyber risks.
6. Technical controls and safeguards
In order to keep your organization safe in the future, you need to implement proper controls and safeguards at checkpoints and make sure that there are no loopholes in your implemented controls.

This enables the security and protection of your application software and services. Therefore, before an IT audit takes place, make sure that you have a list of all the information on technical controls and safeguards so they can carry out their auditing tasks more efficiently.
7. Self-assessment
In order to remediate the findings of an upcoming IT audit, you should run a dry self-assessment beforehand. You should let the auditors in your own organization i.e. internal auditors conduct a trial run beforehand so you don’t face any surprises later.
Running a self-audit will boost your confidence in the performance of your organization. Furthermore, if there are any loopholes in your IT infrastructure, self-assessment will highlight them for you.
8. Mitigations from previous findings
If your organization has gone through an IT audit in the past, then go through its findings and mitigate the previous risks before your upcoming one. Take remedial steps and resolve any serious issues that were found before.
If you think that you are short on time and cannot implement the changes/enhancements, you should have a concrete actionable plan in place so the external auditors can realize that you are sincere with your results and will take the necessary steps to eliminate the issues.
Benefits of Information Systems Audit
Here are some of the benefits of IT audit to the organization:
1. Regulatory compliance
Every organization competes in an environment restricted by laws and regulations to use and maintain IT assets for commercial purposes. Regularly performing IT audits provide a stringent check on whether the organization is complying with regulatory requirements or not. This helps organizations strictly follow laws related to IT assets and avoid legal repercussions
2. Enhanced IT assets performance
IT audits help identify and rectify system vulnerabilities. Once the right processes and protocols are in place, IT assets perform well and are utilized effectively. This results in cost savings and improved business operations.
3. Mitigate risks and secure IT assets
Assessing security protocols as part of IT audit helps organizations implement stronger security measures where necessary. This results in mitigating unauthorized access, cyber threats, and other malware attacks.
4. Adopt evolving IT needs
Auditors identify outdated IT systems and provide recommendations on updating to the latest versions in their audit reports. This helps organizations keep up with the latest technological developments and benefit from operational efficiencies.
5. Increased trust among stakeholders
The audit report is a public document that is open for employees and stakeholders to view how reliable the IT infrastructure of an organization is. A robust and secure IT asset management system builds trust among stakeholders and a good reputation for the organization.
Having an ITAM tool in place makes it easier for organizations to conduct internal audits so you can take proactive steps before an external IT audit. Here is how an internal IT audit can benefit your organization:
- You can put measures in place to ensure that you always meet the compliance requirements for software and hardware usage. This helps guarantee that your business won’t face any fines or penalties during an external audit.
- Based on your hardware usage data, you can set up depreciation management protocols. You can track the usage of your devices, calculate depreciation over time, and anticipate their value before external audits.
- If there are lost or stolen assets that are still registered in your system, you can identify those ghost assets through internal audits. You can then eliminate these assets and take measures to minimize this trend.
- Internal audits help you track and update the locations of your assets so you can be prepared with the updated information ahead of an external audit
Try EZO AssetSonar For Streamlined IT Operations
Frequently Asked Questions For IT Audits
What is an IT audit, and why is it important?
An IT audit is a comprehensive review of an organization’s IT systems, operations, and policies to ensure data integrity, security, and compliance with regulatory standards. It is crucial for identifying vulnerabilities, ensuring efficient IT operations, and maintaining stakeholder trust.
What are the key objectives of an IT audit?
The primary goals include:
- Securing data and systems from unauthorized access and threats.
- Testing processes and protocols to verify strong control measures are in place.
- Sampling, reviewing, and monitoring current IT processes and their effectiveness.
- Documenting and reporting for stakeholders to assess the reliability of the organization’s IT systems.
Identifying and mitigating risks for improved and enhanced IT processes and system controls.
What are the essential components of an IT audit checklist?
An effective IT audit checklist includes:
- Notifying stakeholders.
- Preparing necessary documents.
- Conducting inventory analysis.
- Reviewing written policies and procedures.
- Evaluating the information security plan.
- Assessing technical controls and safeguards.
- Performing self-assessment.
- Implementing mitigations from previous findings.
How can organizations prepare for an IT audit?
Preparation involves:
- Developing a comprehensive audit plan.
- Outlining steps and timelines.
- Performing the IT audit systematically.
- Compiling an audit report.
- Implementing recommendations and conducting follow-ups.
What are the benefits of conducting regular IT audits?
Regular IT audits help in:
- Ensuring regulatory compliance.
- Enhancing IT asset performance.
- Mitigating risks and securing IT assets.
- Adopting evolving IT needs.
Increasing trust among stakeholders.
How does IT Asset Management (ITAM) software assist in IT audits?
ITAM software aids by:
- Providing real-time inventory analysis.
- Ensuring accurate documentation of IT assets.
- Facilitating compliance tracking.
Streamlining audit processes through automation.
What challenges might organizations face during IT audits?
Common challenges include:
- Lack of preparation leading to settlements and productivity loss.
- Inadequate documentation and outdated policies.
- Insufficient technical controls and safeguards.
- Failure to implement previous audit recommendations.
How does an IT audit help with regulatory compliance and risk management?
IT audits verify that IT practices align with legal and industry standards, identify gaps that could lead to non-compliance, and assess risks to data and systems, enabling organizations to take corrective actions proactively.
How can an organization prepare for an upcoming IT Audit?
Preparation includes notifying relevant stakeholders, gathering all necessary documentation (policies, procedures, network diagrams, asset inventories), conducting a self-assessment, identifying and addressing any known issues beforehand, and ensuring all systems are up-to-date.
What are the most common issues found during IT audits?
Common issues include outdated software patches, weak password policies, unauthorized access points, incomplete asset inventories, non-compliance with regulations, and insufficient documentation.
What are the consequences of failing an IT audit?
Failing an audit can lead to regulatory fines, increased risk of cyberattacks, operational disruptions, loss of customer trust, and costly remediation efforts.
How can organizations address and mitigate findings from previous audits?
By implementing recommended controls, updating policies, patching vulnerabilities, training staff, and continuously monitoring IT systems to prevent recurrence of issues.
What happens after an IT Audit is completed?
After an IT audit, an audit report is generated detailing findings, identified risks, and recommendations for improvement. The organization is then expected to implement these recommendations, and a follow-up audit or review might be conducted to ensure corrective actions have been effectively implemented.
What is the role of an IT auditor?
IT auditors assess and analyze organizations’ IT infrastructure and identify operational, financial, or compliance risks related to IT assets.
How often organizations should conduct IT audits?
Normally, organizations choose to conduct IT audits annually. However, it is recommended to conduct cybersecurity audits twice a year.
What is the difference between internal and external IT audits?
Internal IT audit is performed by the organization to find areas for improvement in the current IT systems. It is also a preparatory step before an external audit happens. External audits are performed by third-party, independent IT auditors to ensure the effectiveness, reliability, and security of the IT infrastructure of an organization.







