Suppose, one of the hard disk drives in the data center has malfunctioned and can result in data loss. At the same time, one of the office laptops has raised anti-malware threats that can disrupt the entire network. These situations are high-risk and require immediate attention. How can IT administrators resolve these hardware asset management challenges at once?
Let’s look at hardware asset management definitions, importance, challenges, and solutions.
What are Hardware Assets?
Hardware assets are any tangible, physical, or company-owned technology assets currently in use or in stock. Hardware assets play a crucial role in supporting various organizational tasks and processes. They provide the necessary computing power, storage capacity, and connectivity required to store and process data and facilitate communication. It can be divided into four categories:
- End-user devices: Hardware devices directly used by employees in their day-to-day operation, such as computers, tablets, and smartphones.
- Network devices: Support hardware equipment that facilitates digital and analog communication, such as telephone and video conferencing systems.
- Data-center devices: These assets help data centers function effectively and include servers and security devices.
- Peripheral devices: These are significant support hardware devices that are used within the organization, such as scanners, printers, keyboards, etc.
Challenges like lost devices, budget overruns, and missed maintenance don’t have to drain your IT team.
What is Hardware Asset Management (HAM)
Hardware assets are valuable investments, acting as a backbone for organizations to run their operations smoothly. Since these assets play a crucial role for organizations to operate, it is also essential to efficiently manage these assets.
This is where managers focus on hardware asset management. It helps IT managers define processes, integrate tools, and implement strategies important for managing hardware assets.
Why is Hardware Asset Management (HAM) important to the organization?
Different types of hardware devices can be at different lifecycle stages. Following a step-by-step hardware asset management process can help IT managers focus on where assets are located, and how well they are utilized in the current lifecycle stage.
With processes defined, IT teams have clear visibility on the steps to follow for asset maintenance. They ensure each step on the checklist is completed before the asset moves from the maintenance phase to being available.
For example, a laptop was checked out by an employee. As the employee is exiting the organization, the computer needs to be returned as part of the offboarding process. IT managers can follow an offboarding process checklist so that each step is thoroughly performed and completed.
Hardware asset management is one of the branches of ITAM as a whole. This makes it crucial that HAM processes also consider the overall IT asset management strategies and focus on saving costs, maintaining accurate inventory, and maximizing returns.
Key Hardware Asset Management Challenges Faced by IT Managers
Managing thousands of hardware assets can be difficult for managers, especially when they rely on outdated information and inefficient tracking methods. Here are some of the challenges that they can face:
1. Lack of visibility on hardware assets
It is difficult to keep track of asset activities especially when there are frequent updates, maintenance, or installations. What’s even more challenging is using manual methods to maintain asset inventory, leading to human errors and siloed data. As per an article:

IT managers relying on inaccurate inventory data lack crucial information on which hardware assets are present in the organization, who owns these assets, and how these assets are maintained.
Since the data is not reflected in real-time, IT managers might make incorrect decisions based on outdated information. For example, an employee hasn’t updated hardware asset procurement for the current date. On the same date, the IT asset manager extracted inventory data, realized they were low in stock, and decided to reorder inventory. As a result, the inventory count has been doubled due to the manual update system.
All hardware assets follow a lifecycle that ends when it expires, either the asset can go kaput due to usage over time, or there’s an upgraded version that must replace the incumbent one. When there’s a lack of visibility and it is difficult to keep track of changes in assets, their timely maintenance and replacement almost become impossible.
2. Poor resource allocation and budget planning
Another challenge of mismanaged hardware asset tracking is poor resource allocation. Each hardware asset, including its peripherals, must be assigned and provisioned timely.
Let’s say an organization follows the practice of maintaining spreadsheets, shared with every department to update on resource allocation. In the supply chain department, one employee resigned and another joined at the same time. The department manager only updated the onboarding in the spreadsheet.
They requested a laptop and peripherals for the new employee. The IT manager received the request and ordered new inventory instead of reallocating existing IT assets. Data silos in this organization have led to poor management and unnecessary purchases of hardware assets.
Unnecessary hardware purchases pose financial risks to organizations. When the organization purchases the same or equivalent asset that it already owns even though they don’t need it, it leads to poor financial decisions and inefficient budgeting.
3. Ghost, stolen, or lost assets
IT admins lose a lot of their valuable time on manually discovering and counting asset stock. As their network and user base grows, it is difficult to keep track of hardware assets on a one-to-one basis. It is also likely that assets are being ghosted, stolen, or lost if not accurately tracked.
Ghost assets are hardware assets that are purchased and recorded, but they are either lost, stolen, or unusable while showing active in records. These assets are mentioned in the records but are not available physically.
In the employee offboarding process, the company must retrieve the assets that the employee used. If the company hasn’t discovered that the assets are not returned and the data is not updated accordingly, it will fall into ghost assets. Since the organization still views these assets as available in its stock sheet, managers can’t make an informed decision regarding the allocation or disposal of these assets.
Most educational institutes provide school-owned laptops to students. What if these assets are not returned to the school IT admin after their use?
If these computers are not tracked, they may disappear or even be stolen within a few days. Assets stolen or lost can pose serious risks for organizations – the loss of one hardware asset can be low cost at first, but as tracking becomes inefficient, the cost of lost assets can tremendously increase and the organization would incur additional expenses on replacing these assets.
4. Irregular maintenance and delayed service tickets
When an unexpected breakdown occurs, it decreases productivity – workers are rendered idle if the laptop is not working properly. IT teams that do not keep tabs on regular maintenance can face unexpected downtime resulting in higher repair costs.
Asset maintenance can be daunting if the managers are unaware of which assets are under maintenance. Most service tickets are related to hardware assets. Without sufficient information on the history of assets, their configuration, and previous IT issues, more time would be spent figuring out these issues, delaying service resolution time and making the helpdesk management process challenging.
Outdated spreadsheets and missed updates don’t just slow you down, they cost you money.
Hardware asset lifecycle stages
Organizations are focused on managing hardware assets throughout their entire lifecycle. The hardware asset lifecycle involves several stages from planning to retirement, all of which ensure effective operations.
Solution: Utilize Hardware asset management system
Adopting a hardware asset management system can help organizations streamline their hardware asset management. Here’s how it can solve challenges at each step of the lifecycle:
1. Planning
Organizations planning to purchase hardware assets focus on various procurement factors. These include employee and business preferences, compliance, and budget allotted.
Once all factors are considered, the IT team must collaborate with different departments to note down the exact requirements and purpose of the purchase. Through this, they ascertain if there’s an actual need for purchase or if existing hardware can fulfill the requirements. Once finalized, they also need to ensure how well the asset will be utilized.
With the help of a hardware management system, the IT admin can look into the availability of the hardware assets requested. They can also run reports on asset status and utilization and analyze if the asset is under use, maintenance, or available. If it’s under use, they can also track how long it is being used, when its next service is due, and what steps can be taken to increase operational efficiency.
For example, the headphones requested are shown as available in the system. Upon checking, theable on the system. Upon checking, these headphones require quick service before checking out. After service, the peripheral is provisioned, saving money on additional purchases.
2. Procurement
The next step is to procure hardware assets. As the IT team selects the hardware assets to procure, they also look into which vendors are available, what warranty and technical support they offer, and whether their provided hardware is compatible with other IT hardware assets in the company.

A purchase order request is raised in the hardware asset management system with item, price, and vendor details. The request goes into approval – the organization can set a specific set of approvers to view all related information, verify details, and approve requests in the system.
Managers and directors can thoroughly scrutinize and verify requests as per vendor information, inventory checks, and budget controls. The requester is informed of the approved request and can move forward to procure hardware assets.
The order is placed with the vendor and the purchase order status on the system provides complete visibility into items received or pending. Once payments are processed, the purchase order is marked complete. The system automatically updates inventory after procurement and also saves vendor details, saving time and providing accurate information when needed.
3. Configuration and deployment
As the IT team receives the goods, they check whether the right version is delivered or not. Then the assets are tested for defects and compatibility with the system. Once checked, the next step is to configure and deploy the assets to relevant end users.
Once the assets are tested, they can set up barcode labels in the hardware asset management system, for example, laptops can have LAP-001 added as barcode labels, which also serve as an identification number in the system. When scanning the new hardware assets, the IT team simply scans this barcode and these assets will be categorized under Laptops.
When they have added assets to the system, they can easily be scanned for their configuration and usage. The IT team can create and configure discovery agents in the system to be deployed on all assets. This will provide real-time hardware details at any time, from anywhere.
After successful configuration, these assets are deployed. The end user must ‘sign out’ the device and accept any use policies. The hardware asset management system allows IT admins to assign assets to users and maintain records on the system. This streamlines the onboarding and offboarding process, where they can easily view which devices are used by which user, and when to remove user details to complete offboarding.
4. Tracking and monitoring
IT managers ensure effective hardware asset management through ongoing monitoring and accurate tracking throughout the hardware asset lifecycle.
A hardware asset management system provides IT teams with complete visibility into all company-owned assets. They can view custody, location, and discovery source in a snapshot on the listings page. The system also provides quick action buttons to sync assets with different agents, add and assign to different users, or check in and check out based on verification requests.
Having real-time information allows accurate asset monitoring. Safeguarding high-value IT assets is crucial to prevent thefts and misuse. Since these assets are expensive, they are mostly shared among departments.
HAM system provides user login activity specifying login ID and time of login. As the asset goes through different users, the login activity is updated. IT managers can keep track of who used the asset and can trail records at the time of unauthorized access.
5. Vendor management
Organizations have different vendors for different types of assets. When it comes to hardware assets, the vendors and contracts could be unique for servers, operating systems, user access, etc. A robust system helps IT teams consolidate and manage vendors on a single platform to stay compliant and strengthen vendor relationships.
The system allows IT teams to add vendor details to the system. Once added, they can easily map corresponding assets for the contract and mention its validity. They can enable alerts to notify them of timely renewals of these contracts. They can also view items requested from a specific vendor and view related purchase orders to keep track of incoming stock.
6. Regular maintenance
Constant use of hardware assets can lead to unexpected failures and breakdowns. Regular maintenance ensures optimal performance and extends the working life of assets. This step monitors the performance of hardware assets to maintain peak productivity and mitigate issues that might crop up while in use, such as regular patching and updates, servicing, or aging of assets.
A hardware asset management system helps manage and schedule regular maintenance. IT teams can pre-set dates for maintenance so they can be notified of when service is due. They can also keep track of previous issues to stay informed on the asset’s service history.
Integrations with helpdesk tools can further streamline service requests. Users can create maintenance requests on the helpdesk which are timely reflected on the system for IT teams to see which asset services are pending, in progress, or completed.
7. Retirement and Disposal
The value of hardware assets depreciates over their lifespan. As assets reach the end of their service life, the final step is to ensure the removal of old assets, reuse their software license, and decommission from their active use. Data on retired or disposed hardware assets should be securely wiped to prevent data breaches.
IT managers can enable asset depreciation calculations to track the lowest value of assets in the hardware asset management system. When the asset reaches the lowest value, they can mark the asset as expired or disposed of. The license can be reused on new assets. For example, in the case of BYOD devices, the hardware assets need to be retired from service when the employee who owns the device leaves the company.
Ready to transform your hardware asset management? Download our guide now
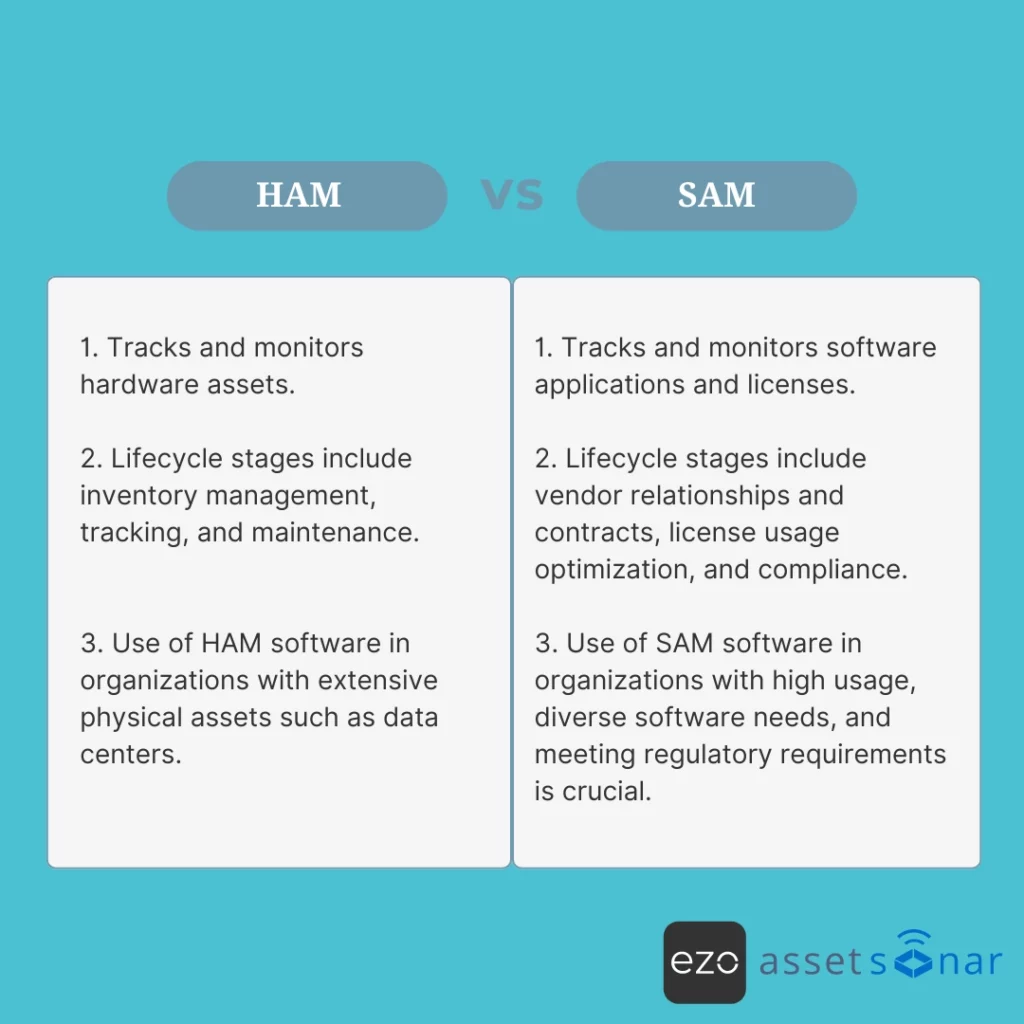
HAM vs SAM
ITAM is divided into various components, two of which are hardware (HAM) and software asset management (SAM). The table below explains their difference:
| HAM | SAM |
| Tracks and monitors hardware assets. | Tracks and monitors software applications and licenses. |
| Lifecycle stages include inventory management, tracking and maintenance. | Lifecycle stages include inventory management, tracking, and maintenance. |
| Use of HAM software in organizations with extensive physical assets such as data centers. | Use of SAM software in organizations with high usage, diverse software needs, and meeting regulatory requirements is crucial. |
Benefits of Hardware Asset Management
When IT managers track each lifecycle stage of an asset through a streamlined process and HAM software, the organizations benefit from:
1. Cost reduction
Hardware assets managed and maintained throughout their lifecycle have a higher likelihood of extended lifespan. Assets in optimal conditions can keep on operating for a longer period with minimal downtime. This results in improved productivity and lower maintenance costs.
When existing assets are performing well, the need to reorder or purchase new assets reduces. On inquiry at the maintenance stage, hardware assets with minimal service can perform longer resulting in increased utilization and cost savings to the organization.
2. Increased security and audit-ready
Having complete hardware details helps IT managers to make timely decisions. When they know an outdated operating system is more likely to increase threats or breaches, they can quickly take action to update the operating system and secure hardware assets.
Following the step-by-step lifecycle process ensures that compliance requirements are met and the organization is audit-ready. Out-of-support assets are disposed of, outdated ones are upgraded or maintained and new inventory properly accounted for are all one step closer to a clean audit process.
3. Decrease in asset theft or loss
Proper asset identification via barcode labels and unique identifiers makes it easier to track and monitor hardware inventory. Knowing the exact asset location and ownership details at all times makes it less likely to be stolen or lost.
Building an effective hardware asset management system is important, but assuring that it operates optimally requires following a set of best practices.
3 Best Practices for IT Hardware Asset Management
1. Establish, Strategize and Plan the Process
Every organization needs planning to set objectives and work towards these objectives to achieve long-term results. Implementing any process without planning can cause confusion and errors. This is also true when implementing the hardware asset management process.

IT managers must plan on how to maximize the benefits of using an asset management system. Strategic planning can help managers create a process that can easily manage hardware assets at each asset lifecycle stage.
Planning a process can include which asset management tasks need to be managed physically and which ones to be automated via the asset management tool. It is also important to ensure clarity on who will own and perform actions for each asset lifecycle stage. This can streamline operations.
Also, establish a chain of requesters, approvers, and owners to keep asset details within authorized access and notify these specific persons in case of any changes in assets at each stage or for any purchase requests.
2. Integrate hardware asset management into all functions and departments
Every function, department, and process in an organization is technology-dependent. They use hardware assets to perform operational tasks, different for each group. To complete certain tasks, they are also interdependent on other teams to assist and contribute towards achieving organizational goals.
These assets facilitate cross-departmental teams to communicate, develop strategies, and work together which is why all assets for every function must be tracked and managed thoroughly:
1. Create a dedicated team responsible for overseeing and managing hardware assets across all departments
2. Document and communicate procedures for acquiring and retiring assets to departments.
3. Conduct training sessions across departments on hardware asset management best practices so that everyone understands their role in managing hardware assets within their specific function.
3. Manage hardware assets in a hybrid IT environment
As organizations grow and evolve, tracking hardware assets and user access is becoming more difficult, especially in a hybrid IT environment. Hardware assets are constantly received or retired in the IT ecosystem to cater to the organization’s growing needs.
To keep pace with tracking these asset changes, real-time insights, reporting, and analysis can help managers understand changing asset custody, tighten security on user access, and remain compliant with evolving processes and regulatory requirements.
A comprehensive hardware management strategy implemented via a robust system helps organizations ensure optimal utilization of their hardware assets, minimize downtime, and reduce unnecessary costs. These combined benefits result in improved productivity and overall operational success.
Frequently asked questions for hardware asset management
What is Hardware Asset Management (HAM), and why is it important?
HAM is the process of tracking, monitoring, and maintaining hardware devices and equipment throughout their period of use, known as the asset lifecycle. It helps organizations reduce costs, ensure compliance, and improve operational efficiency.
What are the key stages in the hardware asset lifecycle?
The lifecycle includes asset discovery, procurement, deployment, maintenance, inventory management, asset tracking, and retirement and disposal.
How can HAM help in reducing hardware costs?
By optimizing asset utilization, preventing unnecessary purchases, and ensuring timely maintenance, HAM can significantly reduce hardware-related expenses.
What tools are commonly used for effective HAM?
Tools like ServiceNow, ManageEngine AssetExplorer, and AssetSonar are popular for automating and streamlining HAM processes.
How to choose the right hardware asset management software?
Choosing the right hardware asset management software requires careful consideration, such as partnering with the right vendors, finalizing features that best suit your business needs, and optimizing technology investment in the long run.
What is a hardware asset management strategy?
It is a set of rules and guidelines that define how you manage your hardware assets from acquisition to disposal.
Why do managers need to manage hardware assets?
Effectively managing hardware assets can help managers reduce unexpected costs, improve decision-making, and boost overall performance.
How does HAM ensure compliance with hardware-related regulations?
HAM tracks hardware usage and ensures adherence to regulatory standards, helping organizations avoid potential legal issues.
Can HAM be integrated with other IT management systems?
Yes, HAM solutions often integrate with IT service management (ITSM) and configuration management databases (CMDBs) for holistic asset management.
What challenges are commonly faced in implementing HAM?
Challenges include maintaining accurate inventories, managing complex hardware environments, and ensuring organizational buy-in.
How does HAM contribute to cybersecurity?
By ensuring only authorized hardware is used and keeping hardware up-to-date, HAM reduces vulnerabilities and enhances security.
Is HAM applicable to cloud-based and virtual hardware assets?
Yes, modern HAM practices encompass cloud and virtual hardware assets, ensuring their efficient and compliant use.
What key performance indicators (KPIs) should be tracked in HAM?
KPIs such as asset utilization rate, compliance rate, asset recovery value, incident resolution time, and inventory accuracy are essential for measuring the effectiveness of HAM processes.
What are the key stages in the lifecycle of hardware assets?
The main stages typically include:
- Planning & Procurement: Assessing needs, budgeting, purchasing, and receiving new hardware.
- Deployment: Installing, configuring, and assigning hardware to users or locations.
- Maintenance & Support: Monitoring, servicing, repairs, and upgrades to ensure performance and longevity.
- Retirement & Disposal: Decommissioning, data wiping, and environmentally responsible disposal or recycling of hardware assets.
What are the primary benefits of implementing a HAM strategy?
Key benefits include significant cost savings by avoiding unnecessary purchases and optimizing asset utilization, improved security through better tracking and secure disposal, enhanced compliance with regulations, increased operational efficiency, and better decision-making with accurate asset data.
How does HAM help with maintenance and service ticket management?
HAM systems track maintenance schedules, automate reminders for servicing, and link assets to service tickets, ensuring timely repairs and minimizing downtime.
How does HAM differ from software asset management (SAM)?
HAM manages physical IT assets, while SAM manages software licenses, installations, and usage. Both are subsets of IT Asset Management (ITAM), which provides a unified approach to managing all IT assets.


