AssetSonar integrates with the SCIM protocol so you can manage the identity data of your employees on the cloud and seamlessly provision them access and user rights into the AssetSonar application from any identity provider.
1. What is SCIM?
SCIM, or System for Cross-domain Identity Management, is an open standard that automates user provisioning for your organization. It communicates user identity data of your employees from identity providers to service providers.
An identity provider (IdP) is a system that contains a robust directory of user identities and single, consistent login credentials for each of your employees. Okta is an example. A service provider (SP) is an enterprise SaaS application that requires these user identities so your employees can log into the application.
The SCIM protocol ensures that any changes made to user identities in the IdP, such as Okta are automatically synced in the SP i.e. AssetSonar.
2. Why use SCIM?
Managing the user lifecycle is crucial for businesses. As companies grow or experience turnover, their employee count keeps changing. They need a quick and easy way to add or delete user accounts in their company directories and simultaneously authorize or revoke employees’ access to various business applications.
Our integration with SCIM simplifies the user experience by automating your user provisioning processes. It automatically creates, updates, and deletes users in your AssetSonar account as you create, update, and delete them in IdP tools like Okta. Since data is communicated automatically, it saves your IT team valuable time and reduces the risk of error stemming from manual data entry.
Note: Our SCIM integration currently supports Okta only. Other IdP systems like OneLogin shall be supported soon.
AssetSonar’s SCIM integration with Okta offers various benefits. These include:
- Streamlined User Management: Integrating AssetSonar with Okta via SCIM simplifies the process of managing user accounts. When a new employee joins, their account can be automatically created in AssetSonar through Okta. This integration ensures that there’s no need for manual entry, reducing the likelihood of errors and saving time.
- Enhanced Security: By using SCIM with Okta, you can enforce consistent security policies across your organization. This setup allows for the centralized management of access rights, ensuring that employees only have access to the AssetSonar resources they need for their role. This minimizes the risk of unauthorized access.
- Improved Efficiency: With automated user provisioning, the time spent on administrative tasks is significantly reduced. IT teams no longer need to spend hours managing user access manually, contributing to overall operational efficiency through more focus on strategic tasks.
- Scalability: As your organization grows, managing users’ access to AssetSonar manually becomes increasingly challenging. SCIM integration with Okta makes it easier to scale your user management processes, accommodating growth without additional administrative burden.
- Consistency in User Data: SCIM ensures that user data is consistent across different systems. When a user’s information is updated in Okta, it automatically updates in AssetSonar too. This consistency is crucial for maintaining accurate records and efficient operations.
- Reduced IT Overhead: Automating user provisioning and de-provisioning through SCIM reduces the workload on your IT team. When an employee leaves the company, their access to AssetSonar can be automatically revoked, enhancing security and reducing administrative tasks.
- Compliance and Auditing: With automated and centralized user management, it becomes easier to comply with various regulatory requirements. You can easily track who has access to what in AssetSonar, which is essential for audits and compliance checks.
- Better User Experience: Employees benefit from a smoother onboarding and offboarding experience as their access to necessary tools like AssetSonar is automatically set up as soon as their account is created in Okta.
3. Use cases of SCIM-based user provisioning
There are four common use cases of user provisioning via SCIM in AssetSonar. Okta helps with them in the following way:
- Creating: New employees are automatically provisioned with their respective AssetSonar accounts when created in Okta.
- Reading: Data regarding employees and team resources can be queried from AssetSonar to match it against existing Okta resources.
- Updating: Any changes in the profile attributes of an employee in Okta can automatically be updated in AssetSonar.
- Deleting: An employee’s access to AssetSonar is de-provisioned when the employee is deleted in Okta. This is typically done when the employee is on leave or has left the organization.
4. [How-to] implement SCIM user provisioning with AssetSonar
Let’s walk you through some basic steps on how to implement SCIM-based user provisioning in AssetSonar!
Step 1: Add the AssetSonar application in Okta
Before you go ahead and enable the integration, you must first add the AssetSonar application to your Okta account.
The process is very simple.
- In your Okta account, go to Applications → Add Application → Type ‘AssetSonar’ in the search bar.

2. This leads you to the AssetSonar application page. Click on ‘Add’.

3. Configure the General settings. Add the name of your business as shown in the subdomain URL of your AssetSonar account. Hit ‘Done’.

The AssetSonar application has now been added to your Okta account.

You are now ready to enable the integration and deploy SCIM-based user provisioning.
Step 2: Enable the integration in AssetSonar
To enable the integration in your AssetSonar account, follow the pathway: Settings → Add Ons → User Provisioning via SCIM and select ‘Enabled’. Hit ‘Update’.

This action reveals additional information shown below.
- SCIM Connector Base URL
- Connector Key
You will need to enter the two values in Step 3.
Step 3: Configure the integration in Okta
Navigate to your Okta account.
- Open the ‘Provisioning’ tab on the AssetSonar App page. Select ‘Integration’ from the sidebar and click ‘Edit’.

2. Select ‘Enable API integration’. Copy the SCIM Connector Base URL and Connector Key from step 2 and paste it onto the Base URL and API Token fields respectively. Click on ‘Save’.

This shall enable the integration on Okta’s end.
3. Now, in the Provisioning tab, select the ‘To App’ option in the sidebar and click ‘Edit’.

4. Select the relevant attributes and changes you wish to sync and click ‘Save’.

Provision settings are saved. You are now ready to create users in Okta and provide them access to AssetSonar.
5. Importing users to Custom Roles
If you want to map your users and their respective roles in a way that their hierarchy is reflected in AssetSonar, then you can do so by checking the ‘Import Users to Custom Roles’ option.

Once you have checked the setting, the following options would appear on the attribute and column mapping table:

Note: If the data values for Roles and Teams are not already specified in AssetSonar, the users belonging to these Roles and Teams will not get provisioned into AssetSonar. You will receive an email listing the users that could not be provisioned.
If a custom role imported from Okta via SCIM does not exist in AssetSonar, users belonging to that custom role can be provisioned to a default role in AssetSonar. You can set the Default Role using the option highlighted below:

Let’s say, you imported users belonging to the custom role Customer Success team from Okta via SCIM and this custom role is not present in AssetSonar, users belonging to this role will be provisioned as Administrators.
If you do not wish to provision these users as Administrators, you can also select the option ‘Provision to some role’ and provision these users to a custom role that already exists in AssetSonar.
6. Provisioning user(s)
In your Okta account, follow this pathway to provision users in AssetSonar via SCIM: AssetSonar → Assignments → Assign → Assign to People.

Click on ‘Assign’ for the user(s) you wish to provision for AssetSonar.

The following overlay appears. Select ‘Save and Go Back’.

Your users have been assigned. Click on ‘Done’.

If you traverse to the ‘Members’ tab in AssetSonar, you can see that the two users you assigned have been added in your AssetSonar account.

7. Updating user information
SCIM also updates any changes you make to the user profiles in Okta. Let’s say, you just changed the default email address of an employee, Michael Kelso, in Okta.
To edit the user profile in Okta, go to Directory → People → Username → Profile → Edit. Edit the username and primary email address of Michael Kelso and click on ‘Save’.

Notice that the default email address for Micheal Kelso has been changed in your AssetSonar account simultaneously.

8. Setting up Alerts for user syncs and updates
AssetSonar allows you to set up and receive alerts whenever users imported from Okta via SCIM are synced or updated. You can set these up from both “my Alerts” and “ServiceDesk Alerts”. Alerts that were previously sent through email are now grouped and can be managed through the Alerts section. Select the email alerts of your preference as shown:

Moreover, the content of the email alerts can be switched to pre-generated templates that can be easily renamed or edited. The default template for email alerts is shown below.

9. De-provisioning user(s)
You can also de-provision the access of your employees to AssetSonar. This may happen when an employee either leaves the IT team or the organization or is on a leave.
To de-provision a user, go to AssetSonar → Assignments in your Okta account. Click on the ‘x’ button next to the concerned user’s details.

Click on ‘OK’.

This shall unassign or de-provision the user from your AssetSonar account.
You can see that Jackie Burkhart no longer exists in the Member logs of your AssetSonar account.

AssetSonar’s SCIM integration streamlines identity management and user provisioning of your employees with Okta.
We will soon be supporting other identity management platforms like One Login etc.
10. Custom attribute mapping for User Listings
AssetSonar detects basic attributes in Okta as they are. However, to map custom attributes and provision users based on these attributes, you need to perform some additional steps.
Step 1: Create a custom attribute
In your Okta account, go to Applications → AssetSonar → Provisioning → To App and then click on the ‘Go to Profile Editor’ button.

On the Profile Editor page, click the ‘+Add Attribute’ button.

Create a custom attribute for every field you want to map in Okta. For example, if you’d like to map the userlisting field:
External Name: userlisting
External Namespace: urn:ietf:params:scim:schemas:extension:enterprise:2.0:User

Then click ‘Save’. The attribute will now be available in Okta.

Step 2: Map the custom attribute in AssetSonar
In your AssetSonar account, go to Settings → Add Ons → User Provisioning via SCIM. Select ‘Enable Custom Field Mappings in SCIM’ and update the setting.

Scroll below. In the User Listing field, paste the values of External namespace and External name from Step 1.

Note: You must paste the custom attribute value in the following format :
External namespace.External name
In this case, the value should look like: urn:ietf:params:scim:schemas:extension:enterprise:2.0:User.userlisting
Hit ‘Update’ once done.
Step 3: Specify the custom attribute and provision user(s)
Return to Okta → Profile Editor → Mappings.
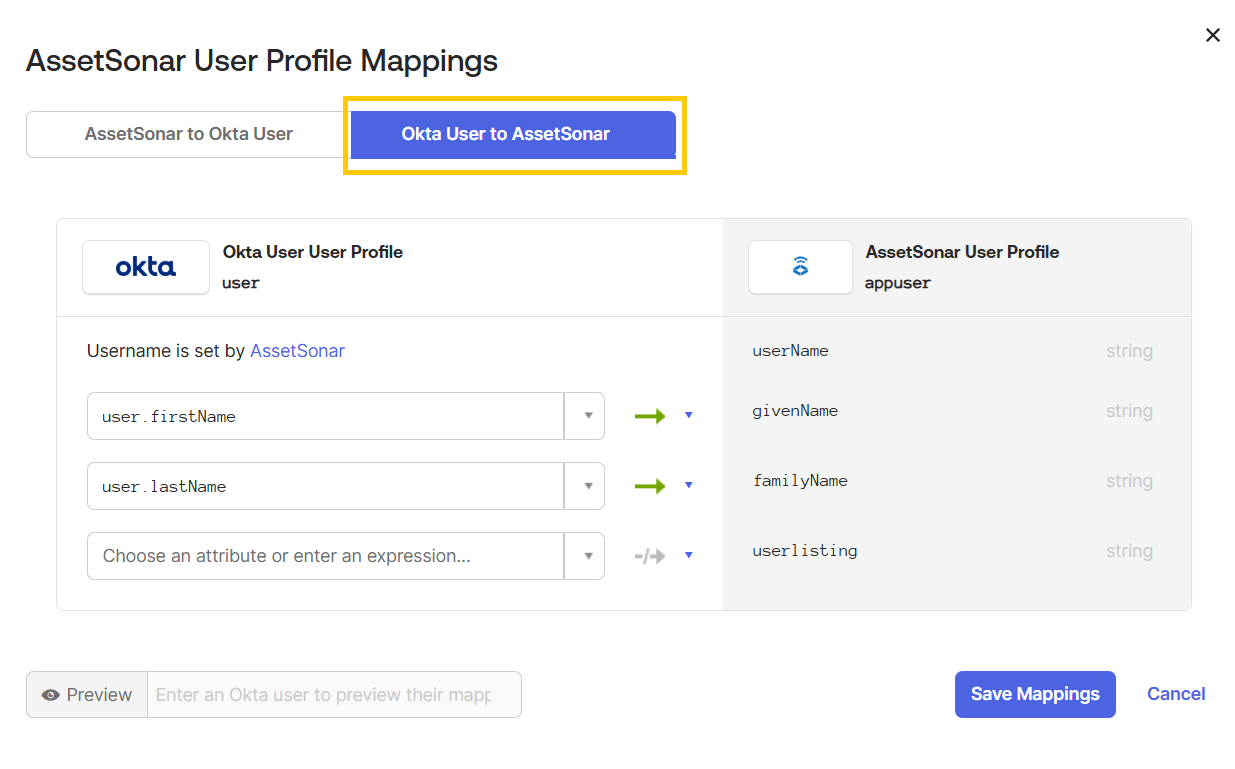
Select ‘Okta User to AssetSonar’.
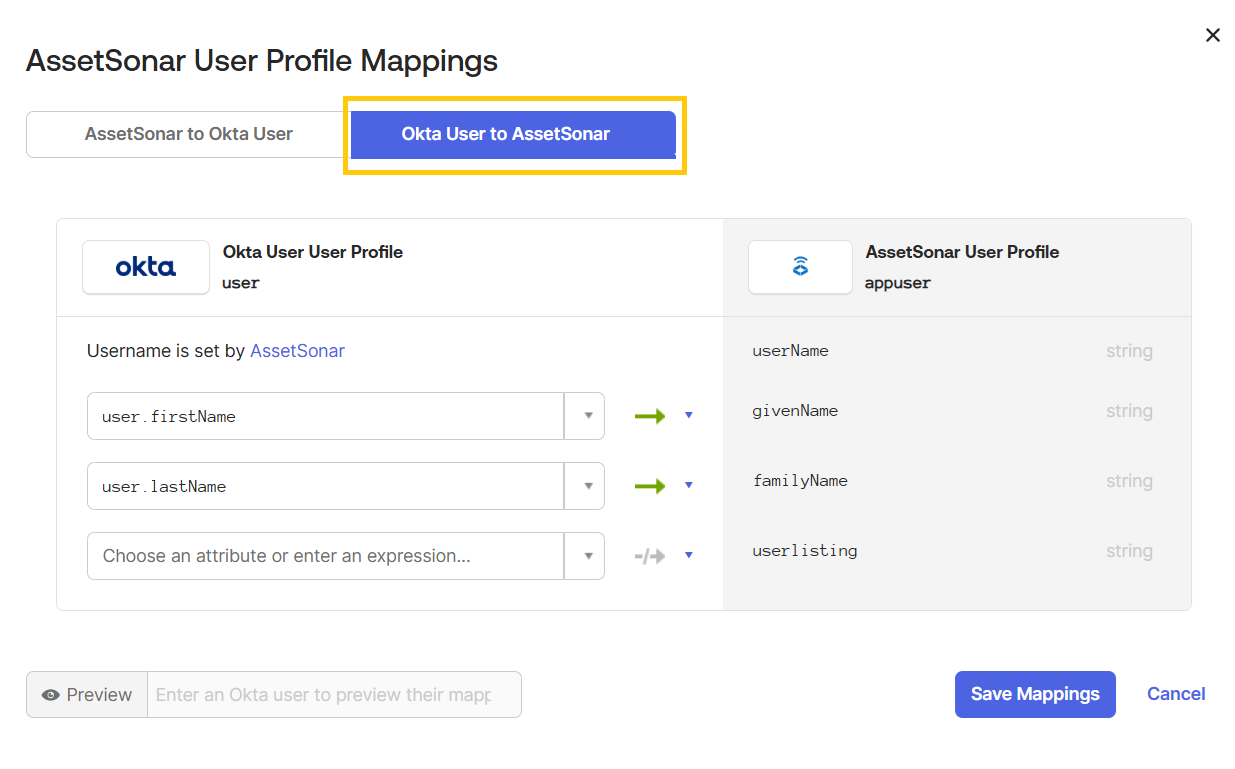
Map the newly created attribute to the field from which it will pull the data.
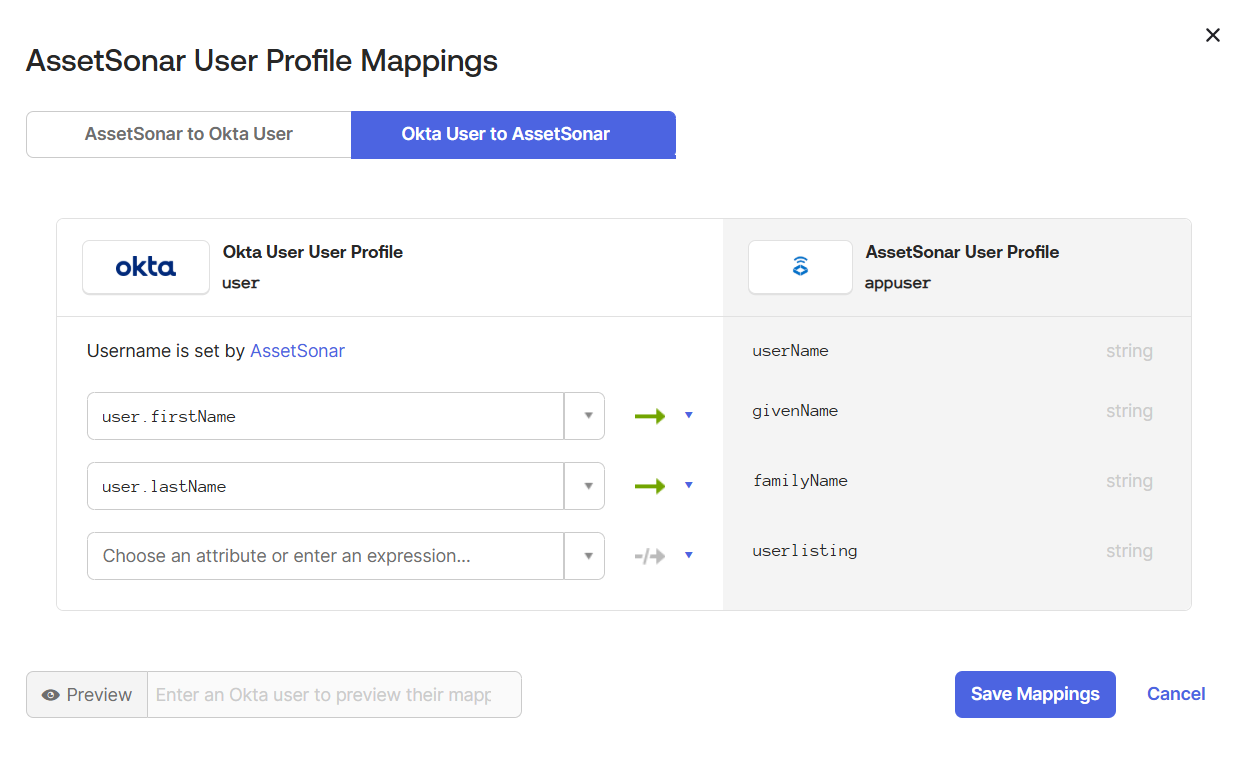
Click ‘Save Mappings’.
Now, go to Applications → AssetSonar → Assignments → Assign → Assign to People in your Okta account.
Assign the relevant users to the AssetSonar application.

This action leads you to the following dialog box. Specify the User Listing and save changes.

This shall provision the user and add them to the IT Support user listing in AssetSonar as illustrated.


Note: Before mapping user(s) to a User Listing, make sure that the latter has been created in AssetSonar.
11. Troubleshooting errors
Error 1: Member could not be updated
“Let’s say you had manually added a Member in AssetSonar. The same Member is also added to your IdP, Okta. You update details for the said Member in Okta. However, the Member information is not simultaneously updated in your AssetSonar account. ”
Solution: This usually happens when the Member has been added into the AssetSonar account manually, without SCIM-based user provisioning. To fix this, delete the manually added Member from your AssetSonar account. Provision the user using Okta as mentioned in Section 5. Now, all the changes made to the Member profile in Okta will simultaneously be updated in your AssetSonar account.
Note: Suppose, you had initially provisioned a Member from another IdP that uses SCIM protocol e.g. OneLogin and the Member’s details were later updated in Okta. In this case, the Member information will be automatically updated in AssetSonar because the Member has been provisioned using the SCIM protocol, no matter the IdP platform.
Read more: Guide to configuring secure LDAP for Azure AD Domain Services
About AssetSonar
AssetSonar is a powerful IT Asset Management solution supporting SCIM-based user provisioning. It is used by IT-intensive organizations and businesses all over the globe. Sign up today for a free 15-day trial.
For more assistance, drop us an email at support@ezo.io. You can also visit our blog for detailed support posts.
Join the Conversation: Twitter | Facebook








