Introduction
For years, patching was dismissed as “back-office IT work” quietly handled by system admins. But in 2025, that mindset is dangerously outdated. A single missed software update can spiral into a board-level crisis, damaging reputation, inviting regulatory scrutiny, and even slamming stock prices.
One need only recall Equifax’s massive 2017 breach (caused by a known, unpatched flaw) that exposed 147 million records and led to a $425 million settlement. Such incidents proved that an unpatched vulnerability isn’t just a technical oversight; it’s a business risk of the highest order. Today, every vulnerability left unpatched represents a ticking time bomb for the C-suite and boardroom, not just the IT basement.
Patch Smarter. Stay Secure.
Why did patching escape the IT basement
Cyber risk equals business risk
High-profile exploits like the MOVEit Transfer vulnerability and the SolarWinds hack made clear that cyber incidents carry steep business consequences. The MOVEit breach in 2023 saw attackers exploit a software flaw to launch widespread ransomware attacks across the education, finance, and insurance sectors. And after the SolarWinds supply-chain attack, shareholders even sued SolarWinds’ board for allegedly failing to oversee cybersecurity risk. These examples underscore that unchecked vulnerabilities can trigger lawsuits, regulatory fines, customer exodus – far beyond an “IT headache.”
Regulatory scrutiny is rising
Frameworks like NIST and ISO 27001 now treat prompt patch management as a compliance requirement, subject to audits. In the U.S., new SEC cyber-disclosure rules force companies to report on their cyber risk management and board oversight, meaning a lax patch process can even put you out of compliance. Timely patching is no longer optional – it supports audit and regulatory requirements across industries
Investor and board pressure
Cyber resilience has become a boardroom priority. Gartner analysts predict that by 2026, 70% of company boards will have at least one cybersecurity expert as a director. This reflects how investors now demand assurance that cyber risks (including unpatched vulns) are being actively managed. Boards increasingly expect regular updates on cyber-resilience KPIs, just as they would expect financial reports. In short, cybersecurity has jumped from the server room to the boardroom, and patch management metrics are a key part of that conversation.
The patch compliance KPI
It’s not surprising that patch compliance is emerging as a key performance indicator. Executives now routinely ask for metrics that were once buried in IT reports, for example:
- What percentage of critical vulnerabilities are patched within our SLA?
- What is our mean time to remediate (MTTR) high-severity vulnerabilities?
- How do our patch timelines compare against industry benchmarks?
These numbers are becoming as visible as uptime or revenue growth on quarterly reports. Boards want to know if the organization is lagging or leading in closing security holes. Patch management success is being quantified in dashboards and scorecards, making vulnerability remediation a measurable component of operational excellence.
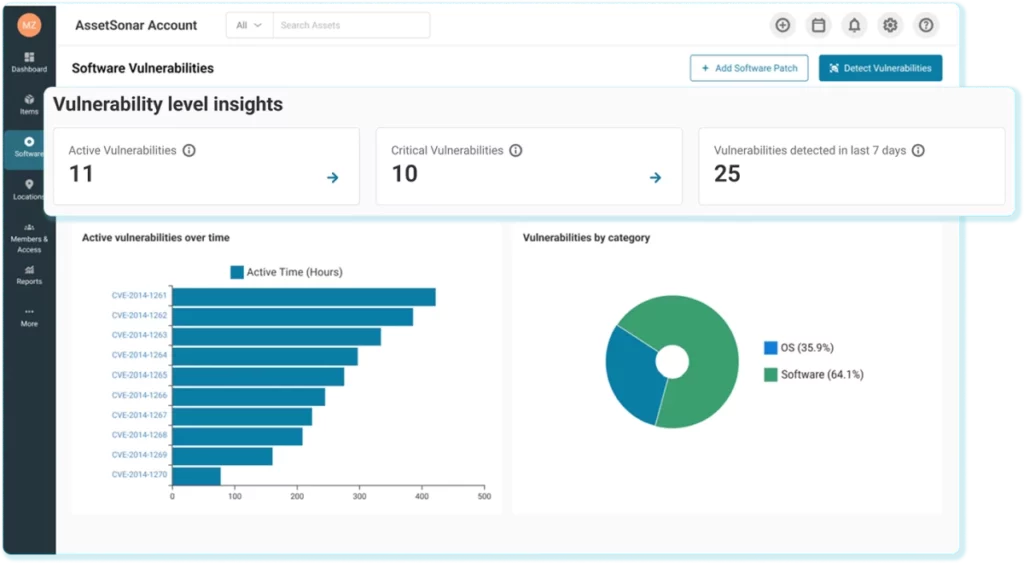
Modern tools now offer executive-friendly views of patch status. The image above illustrates a dashboard of vulnerabilities by severity and affected software – exactly the kind of board-level snapshot that turns patch management into an actionable KPI.
Contemporary patch platforms provide at-a-glance KPIs (e.g., the percentage of systems fully patched vs. overdue) for leadership visibility. This transparency means CIOs and CISOs can confidently report, “We patched X% of critical flaws within 7 days this quarter,” and back it up with data.
The cost of delay
Speed kills – and lack of speed can kill your security. The unfortunate reality is that attackers are now racing ahead of defenders. A recent threat intel shows that the average time from a vulnerability’s disclosure to it being exploited in the wild has shrunk to just 5 days as of 2023, down from 32 days only a couple of years prior. In other words, cybercriminals are weaponizing new CVEs almost immediately, leaving only a razor-thin window for organizations to respond.
Meanwhile, how fast do organizations actually patch? Historically, not fast enough. Industry data indicates many enterprises still take weeks – often months – to fully remediate critical vulnerabilities. One study found the typical company takes nearly 60 days (about two months) as the average MTTR for critical flaws.
Some organizations have an even larger patch lag: earlier research by the Ponemon Institute revealed 60% of breach victims were compromised via a known vulnerability that hadn’t been patched in time. This “patch delay” gives attackers a huge head start. When exploits emerge within 5 days, but patches take 50–60+ days to deploy, there’s a dangerous gap during which attackers can strike at will.
The financial impact of these delays is sobering. Breaches that result from unpatched software tend to be more damaging and costlier to contain than those from, say, human error. For example, IBM’s data shows that lengthy breach lifecycles (often a consequence of undetected, unpatched vulns) add a hefty premium to cost – breaches taking over 200 days to identify/contain cost 33% more than those resolved faster.
The lesson: every day a critical patch lingers undone is extra time for attackers to inflict damage, which translates directly into higher incident costs. IBM’s 2024 report pegged the average breach cost at $4.88M, so adding ~30% more due to patch delays means potentially ~$1–1.5M in avoidable losses. In short, the slow patcher pays a steep price.
Close Vulnerabilities, Automatically
Shifting patch management to the boardroom
How can organizations adapt? Below are key strategies for elevating patch management from an IT task to a true board-level resilience metric:
Elevate reporting
CIOs/CISOs should present patch compliance metrics alongside financial and operational KPIs at board meetings. This means regular reports highlighting patch rates, remediation times, and notable vulnerabilities. Cyber-risk is business risk, so reporting on patch status is now as critical as reporting on cash flow.
In fact, the World Economic Forum recommends that boards receive regular updates on cyber risks and trends, which inherently includes vulnerability management progress. By treating patch management reports with the same gravity as uptime or revenue metrics, leadership signals that security is woven into the company’s success criteria.
Prioritize by business impact
Not all vulnerabilities pose equal risk to the business, and board-level discussions should reflect that. Rather than raw counts of open vulns, focus on which systems are exposed and the potential impact if exploited. For example, a missing patch on an internet-facing customer database should outrank dozens of low-risk internal bugs.
Framing patch priorities in terms of business-critical assets and processes ensures resources are focused on what could truly hurt the organization. Board members don’t need the technical minutiae – they need to know that your patch strategy is laser-focused on preventing outcomes like IP theft, customer data loss, or operational downtime in revenue-generating systems.
Invest in visibility and automation
A common refrain is “you can’t patch what you can’t see.” An accurate, up-to-date asset inventory and vulnerability scanner are foundational. Boards are increasingly asking management, “Do we have visibility into all our software and devices, and are we continuously scanning for missing patches?” If the answer is no, that’s a governance red flag. Leading organizations are investing in automation to keep pace: auto-discovery of new assets, real-time vuln scanning, and even automated patch deployment tools.
Manual, ad-hoc patch processes simply can’t scale to modern speeds. By automating wherever feasible, companies shrink the window of exposure. This also frees up IT staff to focus on tricky exceptions and strategic improvements rather than routine patch push-outs. The board’s role here is to ensure the company is resourcing these capabilities adequately – because the cost of not doing so is far greater.
Conclusion
Patch management today is far more than “keeping Windows up-to-date.” It has evolved into a core resilience metric that belongs on the agenda of executive risk committees and board meetings. Organizations that treat patching as a strategic, measurable program – not a tedious afterthought – will dramatically reduce their cyber risk. They’ll also send a powerful signal to customers, partners, regulators, and investors that security and trust matter in every facet of operations.
Fortunately, new technologies are making this easier. For instance, IT Asset Management (ITAM) solutions like EZO AssetSonar have introduced unified platforms that bring together asset visibility, real-time vulnerability detection, and one-click patch workflows. This enables turning patch compliance into a board-ready KPI that is both measurable and actionable at scale.
This ITAM solution’s dashboard, for example, provides executives with a consolidated view of total vulnerabilities, their severity breakdown, and patch status across the environment – including KPIs such as the percentage of assets fully patched vs. awaiting updates. By leveraging such tools, enterprises can continuously monitor their patch management performance and address gaps before adversaries or auditors do.
In summary, patch management is no longer just an IT operations issue; it’s a business continuity and risk management imperative. Treating it as a boardroom KPI ensures that the organization stays one step ahead of threats, protects its reputation, and demonstrates a proactive security posture in an era when trust is everything.


![[How-to] Automate Vulnerability Monitoring and Patching in EZO AssetSonar](https://cdn.ezo.io/wp-content/uploads/2025/09/05101658/AS-Blog-scaled.jpg)


