Shadow IT exists in various shapes and sizes. It continues to proliferate in our digital spaces, slowly impacting our online experience. But did you know that your browser is one of the most overlooked contributors to Shadow IT? Your browser activity is a blind spot that often goes unnoticed when it comes to the use of unauthorized and unsanctioned software.
Consider Tom, a project coordinator at an IT firm, who works under tight deadlines. To meet the deadlines quickly, he installs a free AI-powered writing assistant using Chrome extensions. While the extension helps him improve his writing, it doesn’t get registered in the IT asset repository. Tom continues to install other assistants for project management that sync with Google Docs and his browser. However, they remain hidden from the company’s IT department.
What Tom doesn’t know is that these tools are auto-saving his sensitive company data (including internal project timelines and client names) to third-party servers, a major compliance policy breach that disrupts IT operations.
This way, Tom’s credentials are stored in tools that don’t require multi-factor authentication, and the applications run while bypassing his device’s firewall and security because they are cloud-based. They are also nowhere to be found in the company’s records.
Result: A month later, Tom’s sensitive company data is compromised as the AI assistant faces a security breach. Internal reports stored in the browser cache, which are synced to the tool’s servers, are now potentially exposed. Tom finds himself in a pickle, and his job is at stake!
Such are the risks associated with Shadow IT sitting in our browsers. Let’s help you understand how to identify them on time and mitigate their usage to remain worry-free!
Before we dive into the findings, check out our latest podcast on the top ways to tackle Shadow IT hiding in your browsers. Click below!

What does Shadow IT look like in browsers?
Shadow IT can impact your browser activity in subtle and unforeseen ways. Here’s how:
1. Access to SaaS products
SaaS tools often bypass traditional security layers installed on devices. Since they are accessed through online browsers, they store users’ data in the cloud, allowing access from anywhere. These apps can serve as communication tools, such as Slack or WhatsApp Web, or file-sharing services, like Google Docs or Dropbox.
Their access is entirely internet-based so that employees may use these tools without their IT teams’ knowledge. Imagine thousands of employees, each using five to ten different tools for their jobs without the knowledge of the IT team. That adds to the problem of Shadow IT, making it more like an IT sprawl.
The AssetSonar team interviewed Tony Mendez, a Lead Technology Specialist at Cannon Business Process Services. He had the following experience to share with regard to Shadow IT:
“People want to go outside of the process. They have meetings in their departments, identify a need, find a solution, and just go ahead and buy software to be successful in front of their managers. And the first moment they have a problem, they call IT to try to fix it.”
This kind of unsanctioned SaaS adoption directly impacts browser activity and security.
Capture browser-based activity, flag unsanctioned tools, and stop data beach.
2. Browser extensions and add-ons
Modern-day browsers often feature a wide variety of extensions and add-ons to enhance their functionality. These extensions may be purchased by users later, but they remain invisible to personnel protecting company data online. Such extensions can violate GDPR compliance regulations through broad permissions like:
- Reading and changing all your data on the websites you visit
- Accessing your clipboard
- Viewing and managing your downloads
If an extension sends user data to servers outside the EU (e.g., in the U.S. or China) without adequate safeguards, it can also violate GDPR’s cross-border data transfer rules.
Extensions like ad blockers and password managers can collect personal information without user consent. They then track your browsing behavior and even auto-sync data to third-party servers, which makes your device more prone to cyberattacks.
Tony described this risk in his own environment:
“We can’t stop people from installing applications, installing software. I would love to, because it makes my life easier. But other people above me, maybe not. Right now, I can see if someone installed something, but only if I go and look. Otherwise, it doesn’t get caught.”
This highlights why browser extensions can be a serious blind spot in even well-run IT environments.
3. Signing up for free trials
Employees often sign up for free trials of various applications, which come with their drawbacks. This low barrier to entry encourages users to use applications without any hesitation, leading to unmanaged data. Once a team or individual becomes reliant on such a tool, it can be challenging to roll back, even if security or compliance issues are later identified.
It usually starts with the thought, “I will use this tool for only one project.” Once the tools start delivering results, they encourage employees to continue using them, adding to the list of unsanctioned software.
Tony sees this happen all the time:
“People buy software outside of IT and put it into some other budget bucket. The problem is that when it’s deployed and they have a problem, they call IT to fix it. That’s where we have a big problem.”
It also leads to data proliferation as employees use corporate data to generate reports or deliver results; this is a serious company code violation. This way, critical corporate data exists in data silos and remains unmanaged, making it unusable for other teams. Not only that, but free trial versions often lack advanced security features, such as data encryption and multi-factor authentication, which puts data at risk of cyberattacks.

4. Buying paid trials
Employees often end up buying advanced versions of SaaS tools that they received free trials for. If employees become too reliant on a particular tool, they push the IT teams to purchase the software. This adds to unnecessary SaaS spending, and the software often remains unused after purchase.
Tony noted the ripple effect of Shadow IT on software costs:
“I get questions all the time when the same software gets purchased by different departments individually. As opposed to buying for the company as a whole and getting a better price.”
Without central visibility, browser-driven purchases spiral into budget waste. This leads to SaaS license waste.
Breaking this cycle becomes difficult because organizations struggle to stop employees from using deeply embedded Shadow IT. Free trials often turn into “Trojan horses” that secretly reside within an employee’s device and are hard to control when needed. They bypass a device’s defenses and remain undetected.
How a Shadow IT tool can help monitor browser activity
Avoiding Shadow IT is not impossible! All it needs is proactive SaaS governance and visibility into your overall asset landscape. Taking robust security measures can help you avoid high costs in the long run while overcoming IT-based obstacles that can slow down operations.
Tony underscored this need:
“Asset management is not a big issue until it becomes a big issue. It’s easy for an asset or a piece of software to get lost, especially in a remote world.”
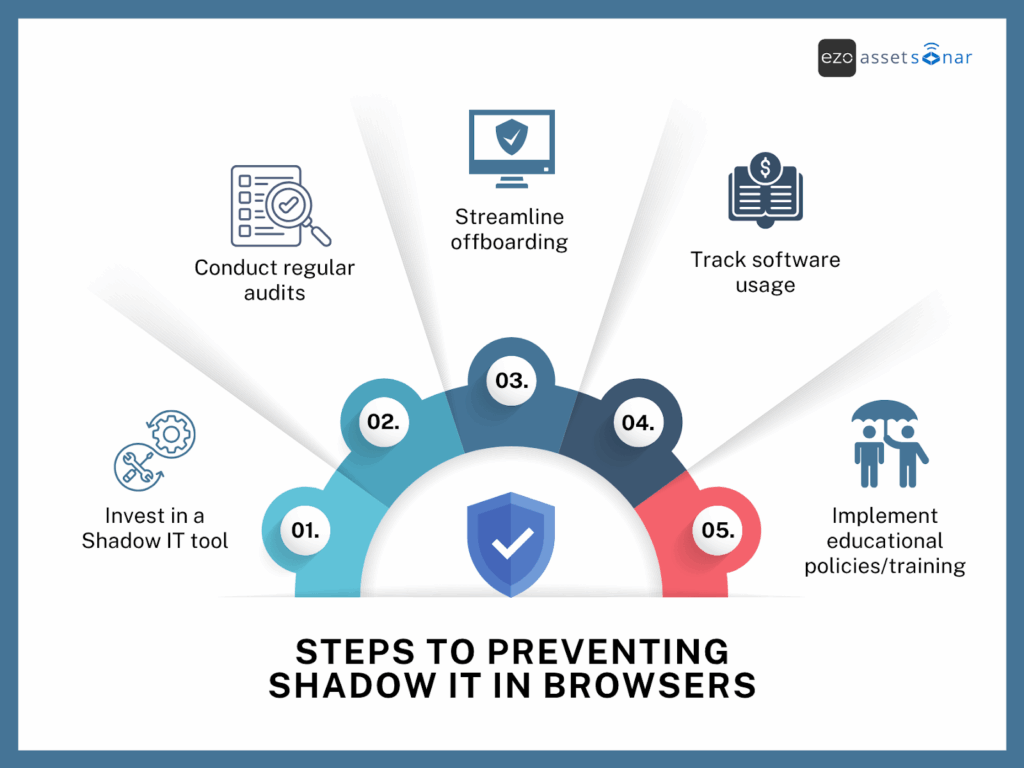
Detecting Shadow IT is an integral part of an ITAM plan or roadmap to help streamline IT operations. Let’s walk you through some ways you can overcome Shadow IT in browsers:
Fix #1: Invest in a Shadow IT tool
Using an IT asset management system to identify unauthorized software is a viable plan. Such software not only enables you to track your browser activity but also helps you manage your IT assets simultaneously.
Tony shared how his organization moved toward better visibility:
“About four years ago, we introduced Azure into our environment. We didn’t have an Azure expert, so we trained someone in-house. Now, if someone installs something, they either get an error prompt, or we get flagged.”
Yet browser-based tools remain challenging:
“We’re moving to browser-based systems. But the director comes from the old days, when everything was on the computer. It’s been a painful process to change that mindset.”
You can leverage the auto-discovery features of the software to detect activity on an IT device and software on the cloud or device.
The software provides complete visibility into your IT environment, including applications on endpoints, networks, and browsers. You can detect both unauthorized and authorized software and even blacklist the software that you no longer want your employees to have access to. The ability to discover SaaS applications gives your IT team a competitive edge in managing these applications and enhancing network security.
Effective ways to implement an ITAM solution include:
- Browser-level visibility: Modern-day IT management tools provide real-time visibility into the domains and websites accessed through your browsers, enabling early detection of Shadow IT. This data is fed into the software you use and broken down into actionable insights that can guide you toward bypassing security risks that break corporate policies.
- Integration with IT ecosystem: ITAM tools typically integrate with platforms such as SSO, MDM, and CMDB to correlate user activity, access points, and assets, making it easier to detect when an unauthorized tool is in use and by whom. The IT team can also flag employees who regularly use unsanctioned tools in the browser.
- Alerts and reporting for unauthorized apps: You can configure the software to flag any application that’s not on the approved list. This enables the IT team to take immediate action—whether it’s blocking access, guiding users toward secure alternatives, or investigating potential security gaps.
- Supports software normalization: The tool not only helps detect Shadow IT, it also helps eliminate redundancy by showing usage trends and license status of different versions of the same app. This helps prevent the unnecessary proliferation of tool versions that might initially start as “free” but become a long-term burden.
- Track user behavior: The browser extension will be able to track the domain/website accessed, the time when it was accessed, and the duration of usage, so the IT team has complete visibility into apps accessed through browsers. Any harmful activity can be flagged immediately in the system, which may be challenging to do manually.
For instance, if your organization has officially blacklisted access of a SaaS tool to its employees, but an employee continues to use the same software independently through a browser, the system will flag the tool.
Reasons for organizations to adopt an ITAM tool: Discover and categorize all types of software, protect your system against cyberattacks resulting from browser activity, and track connected devices for unauthorized software use to take immediate action.
Fix #2: Conduct regular audits
Conducting audits is one of the most effective ways to evaluate an organization’s use of third-party software, including their location, condition, and the number of tools in use.
Tony vividly recalled the consequences of not auditing:
“Years went by, and nobody looked at our numbers. Then one day, Microsoft came knocking and we got hit with about a $180,000 fine. The director got fired, and all hell broke loose. Now, we’re kind of always auditing.”
Audits should go beyond the basics. They should involve identifying unlicensed software and other tools across an organization. They must also include scanning endpoints and networks to detect online suspicious activity. Other aspects they should help identify include:
- Devices not enrolled in your IT asset management system
- Unapproved SaaS applications
Audits should be scheduled regularly to prevent anomalies in online data management. You can use an IT asset management system to start these audits and thoroughly assess your hardware and software. This method helps create complete visibility into your asset ecosystem.
By identifying which Shadow IT tools are most frequently used by employees, IT teams can suggest alternative tools to maintain operations and ensure continuity of corporate projects. Additionally, you can create a list of unsanctioned or blacklisted software and conduct regular audits to ensure it is not used again.
Effective ways to conduct regular audits include:
- Inventory all assets: Use IT asset management tools to keep a real-time record of all hardware and software assets, and cloud services.
- Monitor network traffic: Analyze logs and DNS queries to identify unauthorized access to unapproved applications and services.
- Audit browser activity: Use browser monitoring tools to track unauthorized SaaS logins.
- Compare against approved lists: Regularly cross-reference discovered tools with your list of sanctioned applications.
- Engage departments: Enable other departments to uncover unofficial tools in use and understand the business needs behind them.
For instance, an IT enterprise conducts quarterly audits to assess the frequency of unauthorized software use. After a detailed analysis, the IT team discovers external file sharing without encryption, posing a serious threat to the organizational network. Audits also reveal the amount of resources and money at risk associated with suspicious browser activity.
Reasons for organizations conducting regular audits: Regular audits help organizations avoid security risks associated with data breaches and unauthorized software utilization resulting from uncontrolled browser use. It enables IT teams to replace existing tools with secure and IT-approved alternatives.

Fix #3: Streamline offboarding workflows
Shadow IT on the browser persists even after former employees continue to use third-party tools through organizational logins. This typically occurs when employees have not been fully offboarded and still retain access to their organizational credentials. In some instances, even after revoking access to installed software, IT teams may still be unable to entirely revoke browser access due to their lack of awareness of the external tools used by employees.
Similarly, employees may have signed up for software applications using their personal IDs and uploaded critical company data onto them. So, when they leave, it’s nearly impossible for IT teams to identify the exact tools they used for operational purposes. So, even if the employees’ access to the company account and associated apps is revoked, the IT team will not be able to make changes to the company accounts registered on their private IDs.
Many browser-based services keep users logged in for extended periods or rely on persistent tokens, meaning that even if the user’s corporate network access is cut, their browser may still have active sessions with these unauthorized cloud tools.
Tony explained the gaps he faces:
“We can’t stop people from installing applications. And we can’t always know what they signed up for outside IT. That’s why Shadow IT becomes a real problem during offboarding.”
To cater to this, strategic offboarding workflows need to be implemented to ensure that a former employee’s data is completely wiped from their device and access to all company accounts is revoked, including those operational on their browsers. Automating the monitoring of their browser activity is one key way to achieve this.
Effective ways to streamline offboarding workflows:
- Automate revocation for identified tools: For SaaS applications that have been recognized and possibly approved, the offboarding process can include automated steps to revoke user access. A former employee’s access to a system must be revoked automatically as soon as they leave the organization.
- Manually intervene for unknowns: For newly identified or highly sensitive unapproved tools, you can initiate manual action. This may involve contacting the former employee (if within a short window) or the relevant department head to understand the tool’s purpose, the extent of data stored, and taking steps to revoke access or migrate data.
- Centralize license management: Implement active browser monitoring and restrict software use and license purchases to the IT department. This way, access to new tools can only be granted if employees obtain approval from the IT team.
For example, someone in the marketing department leaves your organization but still has access to Canva Pro. They continue to use the software on a browser without the organization’s consent. If you have an ITAM tool in place to detect Canva Pro’s usage, you can easily identify the software’s use and revoke its access to the employee immediately.
Reasons for organizations to use offboarding workflows: Prevent access to company software to minimize the risk of data leaks and avoid wasting licenses by restricting access to former employees.
Fix #4: Implement software asset management
An ITAM tool will enable you to track your software and gain visibility into software-based usage. Manual or legacy systems do not provide in-depth visibility into your browser, making it difficult to monitor how the browser functions.
Tony’s organization had to build some of this themselves:
“Management didn’t want to spend money on an asset management system. So we had to hire our application development team to build one. It works wonderfully, but we still can’t tie everything together because our ticketing system is separate.”
With a SAM tool, you can track apps accessed through a browser that may not appear on your endpoints. All it requires is integration with SSO providers (like Azure, Okta, and OneLogin), and the system will automatically fetch data to map who accessed which software using their company logins at what time.
You can also install a safe browser extension linked to your ITAM tool to track each URL that your employees visit, including when they access the SaaS tools they use. Accessing the browser gives IT teams complete access to not only the applications accessed by the employees but also how they are being used to ensure SaaS compliance.
A SaaS management tool provides a comprehensive suite of features that extends beyond software tracking, enabling IT teams to promote the safe use of browsers. According to Gartner, a well-implemented SaaS program can help businesses reduce their overall spending by 30%. This includes costs saved by preventing the use of unauthorized software.
Effective ways to implement software asset management for browser tracking include:
- Enable SaaS app discovery: Use an ITAM tool that supports checking unauthorized software, identifying cloud apps accessed via browsers without endpoint installations, and highlighting browser-supported plug-ins.
- Build a software repository: Centralize software management by recording all software on a single platform. Generate a list of unsanctioned software and cross-check it with the repository to initiate the revocation of their access.
- Track license utilization: Identify unused licenses by conducting license audits to encourage employees to utilize the already available software instead of relying on browser-based apps. This helps avoid hidden spending on untracked browser-based subscriptions, allowing for better control of SaaS spending.
- Identifying redundancies: Quickly pinpoint if multiple unsanctioned browser-based tools are serving the same purpose, allowing IT to consolidate and offer a single, approved alternative.
- Automated license management: Automating license renewals, assignments, and payments for platforms regularly used by employees. This helps tackle SaaS sprawl and cost optimization challenges that often arise from uncontrolled browser access.
For example, an enterprise lacked data on the number and type of software being used across the organization. Adopting a SAM tool helped them track the tools that individual teams were using via their browsers, including Slack, Trello, and ChatGPT. After the initial setup, the IT team discovered access to 10 unsanctioned software applications that posed a risk to the company’s data.
Reasons for organizations to invest in SAM: Streamline software license usage, ensure full SaaS compliance, and detect Shadow IT on time to maintain cybersecurity.
Fix #5: Implement educational policies/training
Educating employees and making them aware of the concept of Shadow IT is critical to preventing it in the first place. You cannot eliminate Shadow IT completely without fully taking the employees on board. Well-informed employees are expected to show informed and responsible behavior when using technology.
Run campaigns to inform them of the implications of using apps on the browser without careful consideration. Organization-wide webinars, internal newsletters, and workshops are some ways to encourage users to refrain from using unapproved software.
Effective ways to implement Shadow IT policies:
- Centralized request form or portal: Integrate it with your ITSM or ITAM tool, enabling employees to request browser-based or SaaS tools easily. Shadow IT incidents typically occur when employees lack a proper channel to request tools, prompting them to resort to unauthorized alternatives.
- Interactive workshops or webinars: Invite team leads to learn how to spot Shadow IT and work with IT to find safer alternatives.
- Gamify compliance: Reward teams who follow protocols for requesting new tools instead of adopting them independently.
- Spread awareness verbally: Inform teams of the consequences of using unapproved tools, such as data leaks and compliance issues that can put an employee’s job at risk.
For example, the legal team can hold a company-wide meeting to educate employees on how uncontrolled browser use can make their system more vulnerable to online attacks while also putting company data at serious risk. Negligence on the part of employees can compromise the integrity of the entire organization and also damage its reputation.
Reasons for organizations to educate employees: It creates a transparent system of requests, so employees do not rely on external apps for work; equips them with the proper knowledge to avoid professional mishaps; and helps IT teams prevent Shadow IT before it even occurs.

Overcoming rogue IT for enhanced IT governance
Deploying an ITAM solution helps users discover assets and use robust security controls for data protection. Websites and prohibited URLs can be blacklisted based on your organization’s IT/Infosec policies, so employees do not access them unnecessarily.
Tony summarized the broader challenge perfectly:
“I’d love to get to the point where if somebody tries to install software, they get an error. Right now, I can see it but only if I look.”
Popular ITAM solutions, like EZO AssetSonar, offer advanced security features to combat the problem of browser-based Shadow IT. IT teams can identify the browsers employees are using, the SaaS apps they access within their browsers, and the URLs they visit that may expose them to malware.
Your IT team can support a healthier IT environment by simply controlling what should and should not be accessed via browsers. Build a worry-free IT ecosystem with cautious browser tracking!
Frequently asked questions
What is Shadow IT in browser extensions?
Shadow IT in browsers refers to extensions or plugins users install without IT approval, often with elevated permissions or access to sensitive data.
What risks do browser extensions pose to security?
Extensions can introduce malware, leak data (history, cookies, form inputs), use over-broad permissions, or be compromised via supply chain attacks.
How do unapproved browser apps/extensions contribute to data breaches?
They often bypass standard security controls, can have weak privacy policies, and may transmit sensitive data without encryption or oversight.
Why are browser extensions often overlooked in Shadow IT audits?
Because they’re small, user-installed, and often not logged by traditional discovery tools; many orgs don’t monitor permissions or use.
What are examples of real incidents involving malicious browser extensions?
Cases like DataSpii (leaks via extensions), or extension compromised via Chrome store updates that exfiltrated session cookies.
How do permissions make browser extensions dangerous?
Extensions with permissions like “read/modify all sites” or “access cookies/auth tokens” can read sensitive data, hijack sessions, or inject malicious scripts.
What control methods help manage Shadow IT risks from browsers?
Use whitelisting/approval workflows, centralized policy enforcement, extension permission audits, blocking or disabling unsanctioned extensions.
How can IT detect which browser extensions are installed across devices?
By using enterprise monitoring tools, browser management policies, endpoint agents, or extension discovery tools.
Do browser extensions pose compliance or legal risks?
Yes—if they violate data privacy laws, expose customer data, or store info in non-approved third parties, firms can face fines or liability.
What are the signs that an extension is malicious or risky?
Sudden updates from unknown sources, excessive permission prompts, behavior like screenshotting or accessing active tabs or cookies unreasonably.
Can browser extensions be exploited in a supply chain attack?
Yes – legitimate extension accounts have been compromised, malicious updates pushed, or dev tools hijacked—turning trusted extensions into threat vectors.
How do shadow browser extensions affect performance or stability?
Too many or poorly made extensions slow browser startup, consume memory/CPU, cause conflicts or crashes, or degrade UX—leading to reduced productivity.
How do enterprises balance usefulness vs risk for browser extensions?
By defining safe categories, limiting permissions, using only trusted vendors, reviewing use cases, granting least-privilege, and regular audits.
When should an organization ban or remove browser extensions?
When the extension shows risk (data exfiltration, excessive permissions), when vendor can’t be verified, or when usage is non-essential and introduces attack surface.
How can AssetSonar / EZO help mitigate browser-based Shadow IT risks?
By tracking discovered extensions/apps, centralizing permissions and usage logs, alerting on unapproved browser tools, providing audit history, and enabling policy enforcement across endpoints.







