The contemporary business environment often requires remote or hybrid work arrangements that involve geographically dispersed teams. In some situations, some of the team may be working remotely and others may be on-site — a hybrid arrangement.
These teams work together from different locations and rely on critical devices including computers, laptops, and tablets to communicate, collaborate, and complete operational tasks. As forecasted by Statista, the projected number of mobile workers is to increase to 93.4% in 2024.
The devices that all workers use are and will be developing into more sophisticated and powerful machines. Mobile devices are considered vital assets for any organization.
However, having limited to no access to business policies, apps, and data on mobile devices poses a problem and can reduce employee productivity, cause delays in job completion, and increase the financial cost to the firm. A unified endpoint management system like an MDM agent can provide, secure, and control corporate data so employees can work on managed devices without hassle.
In this article, we will explore what mobile device management entails and discuss its features and benefits, that help an organization manage its mobile devices easily.
What is mobile device management?
Mobile device management focuses on the administration of mobile endpoints within an organization — secures and manages the entire lifecycle of mobile devices without compromising end-user experience.
This process is implemented through MDM software, such as Workspace One, which automates the monitoring of operation systems, ensures device performance, and secures the safety of these devices.
Here are three ways it can help IT managers:
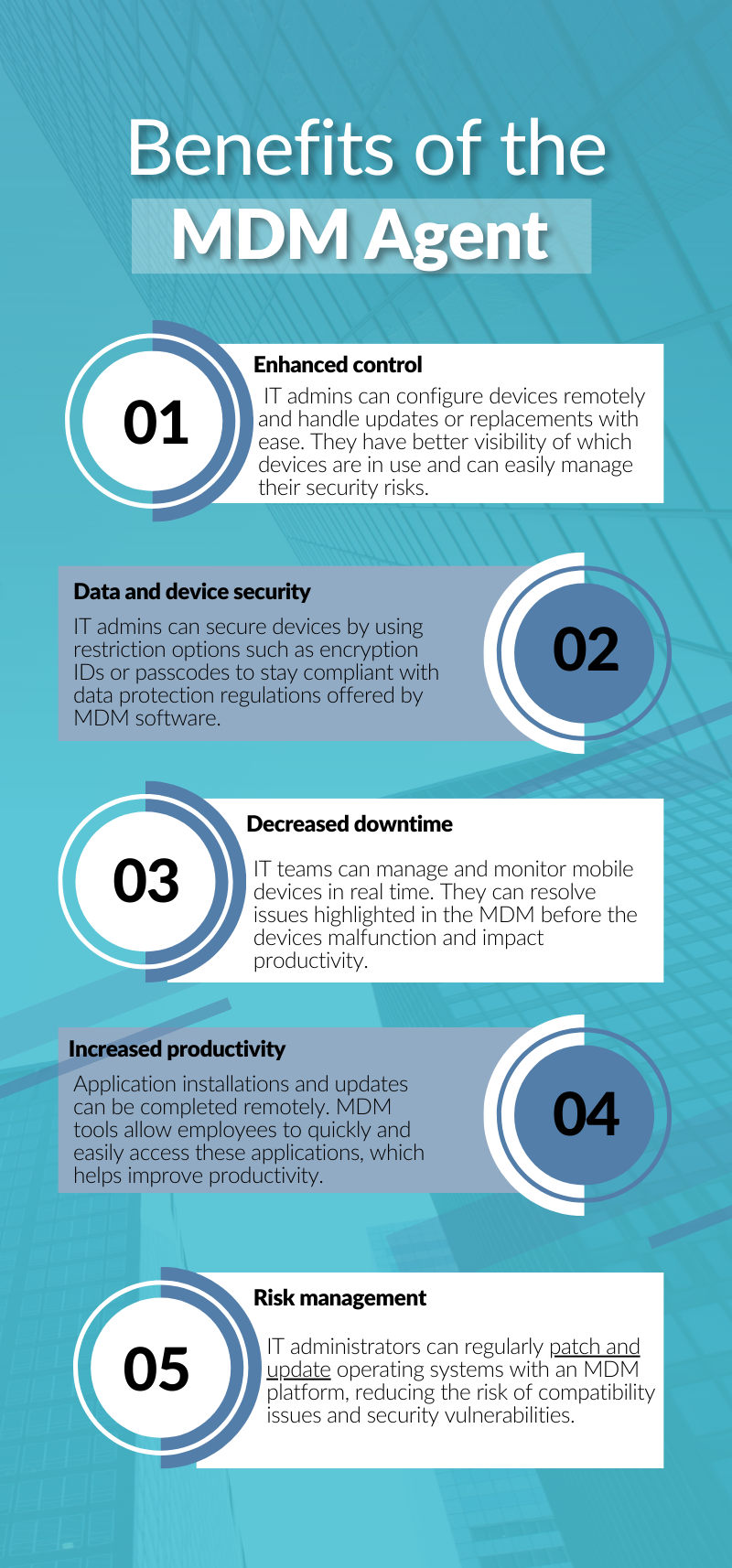
1. Data protection
IT managers need to ensure that crucial business data on mobile devices is protected from malicious access. The software sets encryption and passcodes to prevent unapproved access to data on user devices.

Policies can also be provisioned in the software to disallow any unauthorized applications accessing confidential company information.
2. Device protection
All mobile devices must be protected from viruses that can adversely impact the company network and compromise data. The software allows IT managers to enable jailbreaking detection, where any user who tries to download or install apps that are not approved by the IT admin will not be able to proceed.
It also provides managers with a set of security commands to lock, reset, or geo-locate devices. In the case of a device lost or stolen, the IT manager can enable lock mode to prevent any data losses.
3. Protection of mobile connections
The network connection between the company resources and the mobile devices ensures safe communication. The software helps mitigate the risk of insecure transmission by enabling VPN connections and blocking third-party integrations. This provides secure data access to users of the devices.
MDM agent and ITAM in an IT ecosystem
Mobile devices are treated as assets in any organization. These devices need to be monitored, managed, and maintained throughout their lifecycle. That’s why, MDM can be considered a part of IT asset management (ITAM) in an IT ecosystem.
ITAM focuses on managing assets and optimizing their lifecycles. The information stored in an ITAM solution helps MDM agents take action on mobile devices. For example, if a mobile device needs repairing, the ITAM solution will highlight repair services to the MDM agent which will then start repair on the mobile device.
Here’s how it works:
Onboarding and offboarding
As new employees are hired by the organization, ITAM provides user details to an MDM agent which then ensures devices are configured and provisioned for new users. The devices are properly set up with applications as per the needs of different departments. This provides employees uninterrupted access to workplace resources and starts their training and onboarding process without any delays.
Similarly, when employees leave the organization, the MDM agent ensures all devices no longer in use are completely de-provisioned. These devices are removed, reassigned, or retired from the organization and their network access is revoked. This process is based on the lifecycle management details provided by the ITAM solution. For example, if a mobile device has reached its retirement age, the ITAM solution provides visibility into replacing this device and the MDM agent takes action on removing the old device from the system.
Automated bulk provisioning
When employees are hired in groups or teams, it means a large number of devices are immediately required. The ITAM solution automatically assigns devices to users in bulk.
The MDM agent also enrolls corporate devices in bulk. With the help of MDM tools, the IT team can install applications and content required, secure devices with policies, and make them work-ready from first use.
Accurate inventory database
The MDM agent helps organizations keep track of different devices. This means that you must be aware of how many devices are registered in your MDM system, their types and models, who owns them, and where they are located.

Nowadays, employees have the choice to work on any device they like. They can either work on their own devices or use company-provided IT assets. The MDM agent classifies these devices into bring-your-own devices (BYOD) and company-owned devices.
This helps to maintain inventory differently. For BYOD, the database only keeps track of work data and network connections. On the other hand, company-owned devices are maintained for work data, device protection, and securing network connections.
The MDM agent can view ownership information, installed applications and configurations, warranty status, and location for each device. This helps organizations accurately manage mobile device inventory and remotely troubleshoot issues.
Conclusion
With increasing reliance on mobile devices in the modern business environment, having a robust MDM system in place is crucial. It provides organizations with the ability to remotely monitor, configure, and secure devices such as smartphones, tablets, and laptops. This not only helps streamline operations but also ensures that sensitive data remains protected.
Frequently asked questions
- Can MDM devices be tracked?
Yes, most MDM solutions can track the location and lead to the recovery of a stolen device through one of many software features.
2. What data can MDM see?
MDM software collects various hardware and software information on devices, which helps companies monitor and track company-owned and BYOD devices.
3. When should I use MDM?
The most important reason to set an MDM up is to ensure your network security isn’t breached via a mobile device.
About AssetSonar
AssetSonar is a powerful ITAM solution used by tech organizations and businesses all over the globe. Sign up today for a free 15-day trial.
For more assistance, drop us an email at support@ezo.io.









