Device sprawl, security gaps, and scattered tools haunt IT managers like you everyday. You’ve got an ITAM to log checkouts and an MDM to enforce policies, but without a bridge between them, every offboarding, lost laptop, and audit feels like starting from scratch.
You begin your mornings manually updating asset records and end your evenings chasing down missing devices or license leaks. The problem? Your stack isn’t talking. You have an MDM tool. You have an ITAM. But if they’re not connected, you’re missing half the picture and the only thing that helps you stay in control: complete, accurate visibility.
IDC research shows that the average enterprise manages over 10,000 endpoint devices and have at least 60% mobile devices. While a growing mobile stack means your business is expanding, it also hints at proliferating security threats. Hundreds of mobile devices roaming around freely are a potential compliance risk. You never know who’s using unauthorized apps and has them installed on your company network.
You can tackle this problem now with just a simple solution. Get your MDM working in sync with your ITAM to combat device sprawl and related security risks that go unaccounted for and are not flagged in your ITAM software.
What is MDM and how does it work with ITAM?
Mobile Device Management (MDM) is a practice to manage remote devices within an organization. It connects to all wireless devices and helps in provisioning, policy enforcement, troubleshooting and implementing other security controls. Think of MDMs as the real-time control dock for all mobile devices owned by your organization.
While MDM documents day-to-day device behaviour, ITAM tracks the entire lifecycle of IT devices. These two integrated together provide a holistic picture of the health of IT devices through:
- Unified lifecycle visibility
- Accurate user-device mapping
- Flagging of compliance threads and security alerts
- Updated inventory counts
Don’t let your MDM and ITAM run in silos.
Common use cases of the MDM-ITAM integration
Let’s walk you through the process of how MDM and ITAM integaration works for different industries:
1. Healthcare
Let’s take the example of the healthcare industry! Here’s a short snippet of how it works for them. The healthcare workers work with a lot of sensitive patient information on their IT devices such as smartphones, tablets, or mobile workstation on wheels (WOWs), etc. These devices frequently leave the secure premises and are often carried across wards. Let’s say a nurse loses her IT device while visiting a patient for a home visit. The healthcare unit can be fined under the HIPAA compliance in case the patient information is leaked.
MDM & ITAM integration can help the IT team to immediately trigger Lost Mode via the MDM. It can also help them carry out other actions, such as:
- Remote wipe for lost devices: Automatically flag devices assigned to departing staff and trigger MDM commands to lock or wipe sensitive patient data in case a device gets lost.
- Compliance monitoring: Ensure mobile devices used in hospitals meet HIPAA configuration baselines via MDM, while ITAM maintains audit logs.
- Device lifecycle tracking: Link procurement records from ITAM with real-time usage and health data from MDM to manage inventory and refresh cycles.
This helps ensure compliance, protect patient privacy, and give the IT team a complete audit trail.
2. Corporate IT (mid-market and enterprise)
The MDM-ITAM integration is useful for IT teams in corporate enterprises for the following:
- Unified onboarding/offboarding: Automatically assign or revoke device access during employee lifecycle changes using HR triggers connected to ITAM and enforced via MDM.
- Security and patching: Monitor patch compliance and OS versions via MDM while linking that to device ownership and status in ITAM.
- Shadow IT detection: Identify unmanaged or jailbroken devices from MDM, flag them in ITAM for remediation workflows.
3. Construction and field services
Integrating MDM solutions with ITAM software can also eliminate wasted spend and lost hours on the field via:
- Mobile fleet tracking: Track rugged tablets and mobile devices used by field engineers for inspections and reporting.
- Offline asset recovery: Combine ITAM asset custody logs with MDM GPS/last-known-location or last-logged in-user for lost/stolen device investigations.
- Compliance and insurance: Use data from MDM (e.g., encryption status, last use) as proof for insurance claims and OSHA tech compliance.
Evaluation criteria: What makes an MDM ideal for ITAM integration?
Choosing the right MDM can get confusing, especially with all the options and variations in the market.
Here’s what to look for in an ideal MDM for ITAM integration:
1. Real-time asset discovery + device health data
In modern, mobile-first workplaces, assets aren’t just desktops in cubicles, they’re tablets in field vans, phones in remote offices, and laptops in home offices.
Having an MDM integration with your ITAM solution means you can automatically pull up critical records such as serial numbers, OS, and MAC addresses into the system. This is ideal for organizations with a complex BYOD environment. All mobile devices are accounted for in the asset inventory and kept in close sight. This gives you a live, accurate asset inventory, especially critical in BYOD or hybrid work environments.
What this enables:
- Automated discovery of new or unmanaged devices
- Real-time updates on device health, battery status, compliance state
- Streamlined asset onboarding and warranty tracking
2. Strong identity linkage (user-to-device mapping)
You have noticed hundreds of mobile devices being used within your IT network. However, seeing a list of active devices isn’t helpful unless you know who’s using them. Not anymore. With the MDM integration, the system automatically creates a user-to-device mapping listing down who owns which device using login metadata, IP addresses, and directory syncs.
What it enables:
- Fast ownership lookups for lost/stolen devices
- Easier license allocations and audit tracking
- Tighter control over shadow IT and BYOD access
Example: An Android phone shows up in your system as non-compliant. With identity mapping, you instantly see that it’s assigned to a contractor and take action accordingly. No manual detective work needed.
3. API accessibility and webhook support
APIs and webhooks are the invisible hands behind automation. Without them, integrations are brittle or pretty much manual. A strong MDM should provide robust, well-documented APIs and webhook support for real-time sync and actions.
These two technical components are really important for retrieving granular asset information.
Additionally, a webhook system acts as a real-time alert that picks up on important updates. Whenever a device is enrolled, retired or non-compliant, the MDM sends a webhook for the status to be updated.
What this enables:
- Automatic sync of asset metadata (e.g., from Jamf, Intune, or Kandji)
- Trigger-based actions like wiping data during offboarding, locking devices after theft, flagging non-compliance of devices
- Real-time updates to asset states in ITAM via webhooks
Example: Using Jamf’s API, AssetSonar can pull OS versions, disk encryption status, and user details for Apple devices, and instantly update ITAM records when anything changes.

4. Role-based policy enforcement (RBAC, conditional access)
Security and access aren’t one-size-fits-all. MDMs let you apply conditional access and policies based on user roles or risk levels, and ITAMs record those enforcement events for compliance.
According to role-based policy enforcement, you can control who sees what and for how long. MDMs usually apply security and compliance policies based on user role or device context, whereas ITAMs record which device belongs to which user. What it enables:
- Enforcement of least-privilege access
- Visibility into which assets triggered policy violations
- Compliance-ready audit trails
Example: An unmanaged device tries to access financial data. MDM blocks it instantly, and ITAM logs the event against both the asset and the user, ready for the next audit.
5. Cross-platform support (macOS, Windows, iOS, Android)
You must have experienced several incidents where it was challenging to track Mac vs Windows devices.
IT environments are rarely homogenous. In such cases, a good MDM should collect asset data across all major platforms and share it with ITAM to provide a unified, cross-OS view.
What it enables:
- Centralized dashboards for all OS types
- OS-specific policy enforcement (e.g., iOS encryption, Windows firewall)
- Reduced gaps in coverage for mobile-first or hybrid teams
Example: You can track encryption status on iPhones, antivirus health on Windows laptops, and patch levels on MacBooks—all from a single ITAM console, thanks to cross-platform MDM integration.
6. Lifecycle triggers (e.g., auto-deprovisioning, status sync)
Lifecycle events—like employee exits, device retirement, or upgrades—are some of the most vulnerable moments for data leakage. With integration, MDM and ITAM work together to automate actions based on assets changing their state across the lifecycle.
MDMs make it easier to take these actions and deploy them across various mobile devices.
What this enables:
- Auto-wiping and retirement of devices on offboarding
- Status syncs (e.g., enrolled, lost, non-compliant) between tools
- Reduction in orphaned devices and untracked endpoints
Example: An employee is marked for offboarding in your HR system → ITAM changes the device status to “Pending Deprovision” → MDM automatically locks and wipes the device → ITAM logs the handoff as complete.
To conclude, the best MDM for ITAM integration is the one that closes visibility gaps, automates lifecycle workflows, and gives IT managers full control—from assignment to retirement. Look for deep, not surface-level integration. That’s what sets scalable IT operations apart.
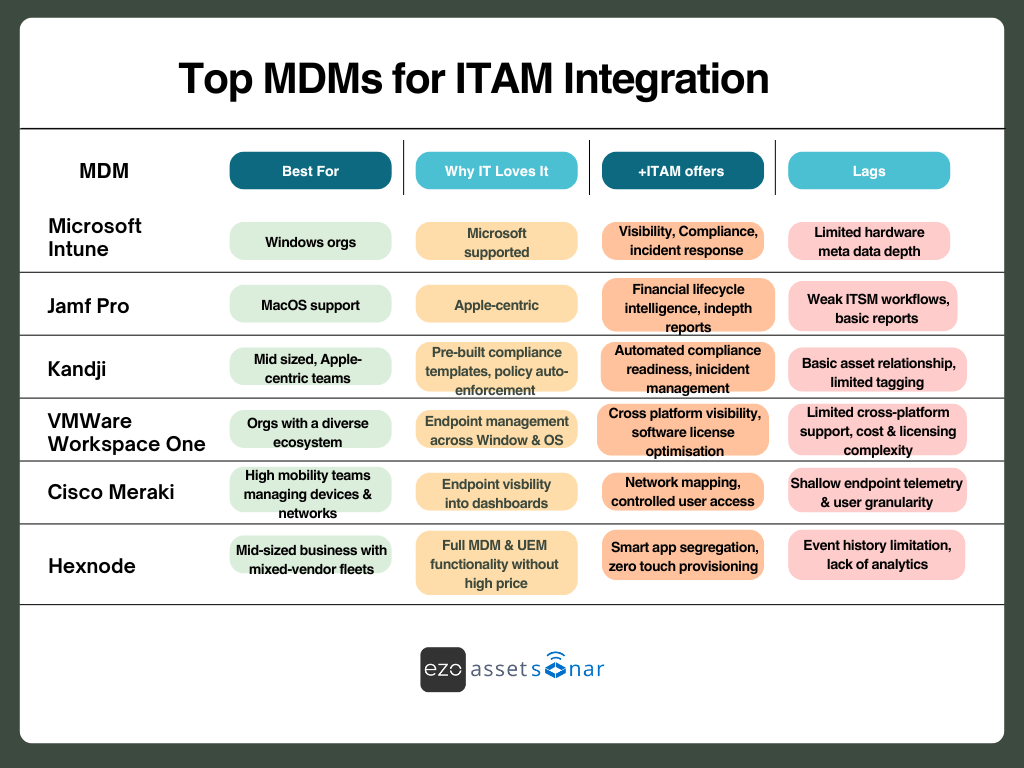
Top MDMs for ITAM integration in 2025 (Ranked by use case)
To help you choose a suitable MDM for your ITAM, we have compiled a list of the best options along with their prominent features and ideal use cases.
Let’s take a look at them:
1. Microsoft Intune: Best for Microsoft-centric enterprises
Why IT loves it
It’s built right into the Microsoft ecosystem and seamlessly integrates with Microsoft 365, Azure Active Directory, and Defender for Endpoint. If your org is already living in the Microsoft cloud, Intune becomes a natural extension of your environment, not another bolt-on tool.
Ideal for:
- Windows-first organizations (with 80%+ Microsoft OS fleet)
- Companies using hybrid identity models via Azure AD
- Highly regulated industries where audit-readiness is critical (e.g., finance, healthcare, legal)
80% of your IT devices are running on Microsoft but tracking device health, OS updates, and compliance across hundreds of endpoints is still fragmented. You want a system that works just for your cloud environment. Microsoft Intune simplifies endpoint management for IT managers and strengthens security by keeping compliance in check, resulting in overall lower costs and improved end-user productivity.
Why Intune works for Microsoft-first IT teams
- Faster security enforcement with Defender and conditional access policies
- Policy-driven configuration aligned with your existing Group Policies
- Smoother audit prep with device + user + policy data consolidated
- One-click visibility into who owns what, what state it’s in, and what to do next
Top Intune integration features
- User management and device metadata: Ability to sync user details, device IDs, and membership records directly from Azure AD into ITAM. This allows IT teams to automatically map users to devices and eliminate blind spots, maintain accurate ownership logs and streamline hardware refresh cycles, and pull in attributes like user department, role, and status to support granular reporting and lifecycle automation.
- Compliance and security settings: It provides real-time updates about firewall status, antivirus and malware protection state, jailbreak or root detection, access violations, and device encryption. This data can then be used to trigger alerts or escalation workflows, log security exceptions for audit purposes, and quarantine non-compliant assets or revoke access. Stay ahead of risk with real-time compliance signals pulled from Intune into ITAM.
- App inventory lists: Retains a list of all installed apps for audit review and license updates. This allows Audit teams to verify software usage and identify unapproved tools (shadow IT), License Managers to track usage and reallocate software more efficiently, and Security teams to flag high-risk or outdated applications. You can build a complete software profile for every endpoint, without waiting for manual audits.
- Self-help kiosk: Empower users to perform basic tasks such as pre-approved app installations, password resets, re-enrollment of devices, and transfer without raising tickets or waiting for IT intervention. This can reduce your helpdesk load and improve user satisfaction, all while maintaining visibility and control through ITAM. You can give power to your users, without giving up control.
Where Intune lags for ITAM integration
While Microsoft Intune is powerful, especially for Microsoft-centric environments, it’s not without its limitations when used as part of an integrated IT Asset Management (ITAM) strategy.
Here’s a breakdown of where Intune tends to lag when paired with ITAM platforms:
- Limited visibility outside Microsoft ecosystem: Intune is optimized for Windows and Microsoft 365 environments. macOS, Linux, and Android/iOS support exists, but is often less robust. Most IT environments are heterogeneous. A modern ITAM platform should get full parity in telemetry from an MDM across OS types.
Intune + ITAM: Unlocking real-time asset intelligence
When paired with a modern ITAM platform, Microsoft Intune evolves from a device manager into a strategic asset intelligence layer.
Here’s how integration supercharges IT operations:
1. Unified asset visibility
Sync real-time data—device name, OS, serial number, compliance status, encryption state, and assigned user—into a single source of truth. Eliminate tool-hopping and guesswork with accurate, always-updated asset records.
2. Automated lifecycle actions
Trigger smart workflows based on live Intune signals. From onboarding to offboarding, or flagging non-compliant assets, your ITAM can initiate device locks, alerts, or retirement procedures—automatically, with audit logs to match.
3. Smarter license and app management
Combine Intune’s app inventory and device activity with ITAM insights to reclaim unused licenses, flag shadow IT, and right-size your software spend, without waiting for a quarterly audit.
4. Accelerated incident response
If a device is flagged “at-risk” or non-compliant in Intune, ITAM contextualizes it across users, departments, and policies, helping IT act faster and more precisely in securing endpoints.
5. Stronger security and compliance posture
Intune enforces policies; ITAM proves them. Together, they ensure enforcement and evidence reducing audit friction, strengthening controls, and supporting regulatory readiness across your fleet.
To conclude, if Microsoft 365 is your digital backbone, Intune isn’t just a good fit, it’s the smart one. And when paired with an ITAM, you finally get the 360° control over your mobile and desktop fleet that modern IT operations demand.
Running Microsoft-first but struggling with blind spots?
2. Jamf Pro: Best for Apple Device Management
Why IT loves it
Jamf Pro is exclusively built for Apple management, with deep iOS and macOS support that other MDMs can’t match. It’s a natural fit for your Apple environment as it automatically updates devices without catching up delays.
Ideal for
- Apple centric organizations
- Enterprise and regulated sectors with Apple fleets (healthcare, finance or education)
- Orgs seeking smooth Apple onboarding
Why Jamf matters for Apple-intensive orgs
- Meets high expectations and support needs to Apple-heavy environments
- Native Apple lifecycle management
- Holistic Apple security and compliance
Jamf Pro is your best pal to automate mobile device management to create a unified IT ecosystem. Make sure work never stops by getting the right devices assigned to the right users with lifecycle management. Practice automatic inventory collection by tracking which apps are being used, or rarely used, to cut costs.
Top Jamf Pro integration features
- Zero-touch deployment: Automatic deployment for Apple devices is extremely impressive. MacBooks and iPhones fully configuring themselves without extra effort is a dream come true.
- License alignment: Track app install/uninstall events to flag in ITAM to align software costs with asset assignments.
- Device sharing: Creates multiple profiles for the same device so that shared devices can be used by different users.
- Granular asset classification: Jamf Pro auto-classifies devices based on rules such as last check-in, OS version, or access location and syncs this data into ITAM for intelligent asset management.
Where Jamf Pro lags for ITAM integration
While Jamf Pro is an excellent choice for Apple-intensive orgs, there are some limitations to its functionality:
- Financial or procurement tracking: Jamf Pro lacks the ability to automate recording of purchase price, or depreciation for assets. However, warranty info can be retrieved for Apple hardware, especially with GSX integration but it is not always out of the box and may require setup. Whereas, custom fields can be used to store purchase-related data (manually or via API), so Jamf allows it but doesn’t automate it.
- Software or license entitlement management: Jamf Pro records inventory of installed software but does not track cloud software, license entitlements, usage rights or contract details. Basically there is lack of support for managing software licenses and tracking compliance. Due to this shortcoming, you cannot have an accurate number of software licenses owned at a time or know whether a device installation is properly licensed.
- Weak ITSM workflows: It doesn’t natively integrate with service desk or ITSM workflows, and requires connectors or APIs to connect data.
- Basic reporting: The reporting in Jamf Pro only provides basic information on device inventory and security. There is limited information on depreciation, total cost of ownership and year-on-year forecasting for IT assets.
However these limitations are fulfilled when Jamf Pro is integrated with an ITAM. The integration fills in all the blindspots providing access to CapEx, depreciation, license management and in-depth reporting.
Jamf Pro + ITAM: Complete control over your Apple ecosystem
Jamf Pro excels at Apple device deployment and management. But when integrated with a dedicated ITAM platform, it becomes part of a more powerful ecosystem—bringing financial, compliance, and lifecycle visibility into your Apple fleet. Here’s what the integration unlocks:
1. Financial and lifecycle intelligence
Bridge the gap between device provisioning and asset accounting. Enrich each Apple asset record in your ITAM with:
- Purchase dates and cost centers
- Warranty status and end-of-life data
- Depreciation schedules and replacement timelines
This empowers IT and Finance to align on budgeting, refresh cycles, and long-term capital planning.
2. Deeper license and software management
Jamf’s app inventory becomes actionable in ITAM. You can map app installs to license entitlements, flag unused apps, and link usage data to contracts. Plus, it helps you cut waste, stay compliant, and forecast renewals with confidence, especially for high-cost Apple-compatible software suites.
3. Shared device governance
Manage pooled or shared iPads and Macs with user-level accountability. Jamf profiles + ITAM’s audit trails = a clear view of who used what, when, and how. Perfect for education, healthcare, and labs where it is a norm for devices to exchange hands frequently.
4. Proactive risk and compliance management
Combine Jamf’s telemetry—OS version, encryption state, location, jailbreak detection—with ITAM policy controls. Flag non-compliant devices, log violations, and automate remediation workflows like device lock, removal from inventory, or service desk ticket generation.
5. Rich, cross-system reporting
Go beyond Jamf’s basic dashboards. Pull enriched reports from your ITAM on Apple asset health, support tickets, license allocations, total cost of ownership, and forecasting. Ideal for quarterly reviews, audits, and CFO-level reporting.
3. Kandji: Best for Mid-Market Mac-Heavy Teams Needing Automation

Why IT loves it
Kandji is designed exclusively for Apple environments with a focus on powerful automations that sets it apart from other MDMs. It helps you save time by offering pre-built compliance templates and auto-enforcement of policies, saving tons of manual effort.
Ideal for
- Apple-centric environments
- Mid-sized IT teams
- Compliance-driven orgs
Kandji integrates with ITAMs to give you a single source of truth with unified lifecycle management. It also mimics Jamf Pro’s zero-touch deployment with excellent results.
Why this matters for Apple-centric orgs
- Complete visibility into security risks for Apple owners where information usually slips through the cracks
- Compiles all costs related to procurement, assignment, and decommissioning that aids in budgeting for the IT landscape
Top Kandji features
- Automated Device Enrollment (ADE): Seamlessly onboard Apple devices with zero-touch provisioning via Apple Business Manager. ITAM systems can auto-ingest device records, assign ownership, and track lifecycle stages from day one.
- Blueprint-based configuration: Use Kandji Blueprints to group and apply settings, apps, and restrictions based on department or location. Sync blueprint metadata to ITAM to improve asset classification and policy mapping (e.g., “Finance MacBook Air” vs. “Creative Team iMac”).
- Security compliance monitoring: Tracks FileVault encryption, firewall status, password policies, and OS patch levels. This telemetry feeds into ITAM to flag non-compliant assets, trigger alerts, or generate compliance audit reports.
- App and patch management: Automatically deploy and update Mac apps (both App Store and custom apps). Integrate with ITAM to track app inventory by device, detect software bloat or underused licenses, and align installed apps with entitlement records.
- Lost mode and remote lock/wipe: Trigger Lost Mode or remote wipe on compromised or lost devices. When tied to ITAM workflows, these actions can be logged, automated during offboarding, or triggered on policy violation.
- Device lifecycle visibility: Kandji surfaces hardware metadata like serial number, OS version, last check-in, and battery health. ITAM platforms can use this data to track age, usage, and refresh cycles—improving TCO analysis and procurement forecasting.
- Custom scripts and remediation: Deploy scripts for custom configurations or fixes (e.g., enforce VPN config or reset printers). ITAM can trigger these scripts via integrated workflows based on asset conditions (e.g., “Device flagged as non-compliant” → run remediation).
- User identity integration (Okta, Azure AD, Google Workspace): Sync user data and group assignments to ITAM. Enables accurate user-device mapping, role-based reporting, and access control audits.
Where Kandji lags for ITAM integration
- Limited asset tagging: Kandji only supports a single asset tag field for entering basic inventory codes. It does not support multiple complicated tags or customized labels. In case you have complex codes, you will need to enter them into your ITAM manually.
- Basic relationships: Kandji only logs assets as individual entities. It doesn’t document relationships like device → peripheral. For example, you can’t directly assign a Mac to a department or track a phone that’s part of the conference room kit within Kandji.
- License tracking: Kandji doesn’t keep an account of how many licenses have been deployed. It only tracks software installation. It will only indicate how many licenses or software are installed, not how they map to devices.
Overall, Kandji is a great tool for managing Apple devices for mid-IT level orgs with a focus on automation workflows that help save time and effort for IT teams. By syncing Kadji’s real-time device data into your ITAM you get enterprise-level visibility into your Apple ecosystem.
Kandji + ITAM: Automation meets Asset Intelligence
Kandji excels at automating Apple device management. But when paired with a robust IT Asset Management (ITAM) platform, it unlocks full lifecycle visibility, financial clarity, and governance across your Apple ecosystem. Here’s what the integration delivers:
1. End-to-end asset lifecycle management
From procurement to decommissioning, ITAM extends Kandji’s visibility by adding:
- Purchase dates, cost centers, and depreciation schedules
- Asset status tags like “Loaner”, “In Repair”, “Ready for Redeployment”
- Offboarding automations triggered by Kandji’s compliance or check-in signals
This lets IT teams manage Apple hardware as strategic business assets, not just endpoints.
2. Automated compliance and audit readiness
Kandji monitors encryption, firewall, and OS status. ITAM can translate this telemetry into:
- Real-time compliance dashboards
- Audit trails for every Apple device
- Alerts and remediation workflows for non-compliance (e.g., auto-lock or ticket creation)
Perfect for healthcare, finance, or education environments where audit fatigue is real.
3. Smarter software spend management
Kandji shows what’s installed, ITAM connects the dots. Together, they help:
- Identify unused or duplicate apps across devices
- Map software to license entitlements and departments
- Reclaim licenses tied to inactive users or decommissioned hardware
Result? Lower SaaS waste and easier license right-sizing.
4. Stronger identity and access governance
Kandji syncs with identity providers (Okta, Azure AD, Google Workspace). ITAM then links:
- Users → Devices → Apps → Access levels
- Department-level ownership and chargebacks
- Role-based reporting to uncover usage patterns and anomalies
You get a clearer picture of who owns what, how it’s used, and who’s accountable.
5. Faster response, fewer tickets
Lost or compromised Macs? Kandji triggers Lost Mode. ITAM logs the event, updates status, and can initiate next steps like:
- Notifying the security team
- Flagging the asset for recovery or replacement
- Creating a helpdesk ticket with full device and user context
Automated workflows mean less back-and-forth, and more time for high-impact IT work.
4. VMware Workspace ONE: Best for cross-platform, enterprise-scale deployments
Why IT loves it
VMware Workspace One offers endpoint management across Windows, MacOS, iOS, and even Android, which saves you the hassle of switching between tools to manage your vast range of IT devices. Built-in tools such as Workspace One Intelligence and Trust Network offer granular monitoring, risk scoring, and automation.
Ideal for
- Orgs with a diverse ecosystem
- Global enterprises and regulated sectors
- Businesses invested in the VMware ecosystem already owning VMware Horizon, Carbon Black, or vSphere.
VMware Workspace is designed to help you manage both endpoint management and asset tracking. It provides complete visibility into company-owned devices that can be helpful to run in-depth reports.
Why this matters for hybrid environments
VMware is critical in hybrid environments because it normalizes operations across diverse infrastructures, allowing IT teams to deliver consistent services, enforce policies, and adapt rapidly — all without breaking existing workflows.
Top VMware Workspace ONE features
- Cross-platform device management: Unified endpoint management (UEM) for Windows, macOS, Linux, iOS, Android, and Chrome OS. When synced with ITAM, it enables comprehensive asset inventory across all device types, critical for environments with mixed OS fleets.
- Real-time device health and compliance monitoring: Tracks encryption, antivirus status, OS patch levels, jailbreak/root detection, and more. Feeds real-time compliance signals into ITAM for proactive risk management, automated quarantine workflows, and audit reporting.
- Software inventory and app management: Captures installed software details across platforms, including versioning and patch compliance. Supports ITAM in: mapping apps to licenses, identifying unauthorized software (Shadow IT), and aligning software usage with contracts and entitlements.
- Remote actions and device control: Offers remote wipe, lock, restart, and enterprise wipe for lost/stolen or decommissioned devices. ITAM can automate these actions during offboarding, policy violation, or device retirement workflows.
- User-device relationship mapping: Integrates with Active Directory and SSO platforms to associate users with their enrolled devices. Supports ITAM in maintaining accurate ownership logs, enforcing chargeback/showback policies, and simplifying audit trails.
- Lifecycle visibility: Pulls metadata like OS version, last check-in, battery health, storage usage, and device location. ITAM platforms can use this data to: predict refresh needs, track device age and utilization, and improve TCO forecasting and budgeting.
- Conditional access policies: Controls app access based on compliance state, device health, and user role. Paired with ITAM, this ensures only compliant owned devices access critical systems, reducing risk exposure.
- API-first extensibility: Rich APIs allow Workspace ONE data to sync into ITAM platforms with granular control. Enables custom workflows like syncing asset check-ins, creating tickets from compliance failures, or flagging underutilized assets.
Key limitations of VMWare Workspace ONE
- Limited detailed hardware metadata: Workspace ONE provides basic device information but often lacks deep hardware details like warranty status, battery health, or precise component specs, limiting full lifecycle management insights in ITAM systems.
- Complexity and steep learning curve: The platform’s breadth and flexibility can introduce complexity, making integrations and ongoing management challenging, especially for mid-market IT teams without specialized VMware expertise.
- Fragmented software license tracking: Workspace ONE tracks installed applications but doesn’t inherently map software licenses, usage rights, or entitlements. This creates gaps in license compliance and optimization when used alone.
- Inconsistent cross-platform support: While strong on Windows and some mobile OS, Workspace ONE’s telemetry and management capabilities are less comprehensive or mature on macOS, Linux, or certain IoT devices, reducing unified ITAM visibility in heterogeneous environments.
- Limited native ITSM integration: Workspace ONE lacks seamless, out-of-the-box integrations with many popular IT Service Management (ITSM) tools, requiring additional connectors or custom development to synchronize workflows, asset updates, and ticketing.
- Basic reporting and analytics for ITAM needs: Reporting focuses more on device security and compliance metrics than on financials, depreciation, or detailed asset lifecycle forecasting critical for ITAM-driven decision making.
- Cost and licensing complexity: The pricing model can be complex and potentially costly, especially when layering ITAM integrations and advanced management capabilities, making budgeting and ROI assessment more difficult.
VMware Workspace ONE + ITAM: Unified control for hybrid IT ecosystems
VMware Workspace ONE delivers robust cross-platform endpoint management, but when integrated with an IT Asset Management (ITAM) platform, it unlocks deeper insights, automation, and governance that transform how you manage your diverse IT landscape. Here’s what the integration enables:
1. Comprehensive, cross-platform asset visibility
Workspace ONE’s unified endpoint management data, spanning Windows, macOS, Linux, iOS, Android, and Chrome OS flows into ITAM to create a single source of truth. This consolidated inventory fuels smarter lifecycle decisions, budgeting, and refresh planning across heterogeneous device fleets.
2. Real-time compliance and risk mitigation
Workspace ONE’s telemetry on device health, encryption, patch levels, and compliance feeds directly into ITAM dashboards. This enables proactive risk detection, automated quarantine or remediation workflows, and audit-ready reporting that keep security aligned with enterprise policies.
3. Enhanced software license and usage optimization
While Workspace ONE captures installed apps, ITAM layers in license entitlements, contract terms, and usage data bridging gaps to:
- Identify unauthorized or underused software
- Optimize license allocation
- Ensure compliance with vendor agreements
This helps reduce software waste and control costs.
4. Automated device lifecycle actions
ITAM workflows leverage Workspace ONE’s remote control capabilities to automate key lifecycle steps such as device offboarding, lost/stolen device locking, or wiping during policy violations, streamlining asset disposition and reducing manual overhead.
5. Accurate user-device mapping and chargeback enablement
Integration with directory services and SSO allows ITAM to maintain precise ownership records, enforce chargeback/showback models, and simplify audit trails, offering transparency into who uses what and enabling better budget accountability.
6. Predictive asset management and forecasting
Workspace ONE’s metadata (e.g., last check-in, battery health, OS version) enriches ITAM’s analytics capabilities, helping IT leaders forecast refresh cycles, assess total cost of ownership (TCO), and plan procurement with greater confidence.
7. Customizable, API-driven automation
Workspace ONE’s rich APIs allow ITAM to sync granular data and trigger automated workflows such as asset check-in/check-out, compliance ticket creation, or underutilized asset flagging, tailoring asset management to your organization’s unique needs.
5. Cisco Meraki Systems Manager: Best for Network-Integrated Asset Monitoring
Why IT loves it
Cisco Meraki brings endpoint visibility into the same dashboards that manage access points, switches and security appliances. This is a game-changer for teams managing distributed networks especially for remote work environments.
Ideal for
- IT teams managing networks and devices in tandem
- High mobility environments
- SMBs or mid sized businesses looking for cloud-native tools with quick deployment and low costs
Why this matters for distributed operations
In environments like schools, healthcare networks, or field-based enterprises where devices are constantly in motion and IT infrastructure is highly distributed, Cisco provides the visibility, control, and security needed to manage operations at scale.
In such distributed environments, you don’t have the luxury of centralized IT support or fixed device locations. Cisco helps bridge that gap by offering enterprise-grade network control, device insight, and security, all delivered remotely. This is perfect for schools and other asset-fluid ecosystems.
Top Cisco Meraki features
- Cloud-based centralized management: Meraki’s hallmark is its intuitive, web-based dashboard. IT teams can configure, monitor, and troubleshoot networks across multiple sites from anywhere; no physical access or complex command-line interfaces needed.
- Auto VPN & SD-WAN: You can easily deploy secure site-to-site VPNs with a few clicks. Combine this with Meraki SD-WAN to optimize traffic flow across WAN links, reducing latency and saving on bandwidth costs.
- Integrated security and firewall: Meraki appliances come with built-in firewall, IDS/IPS (powered by Snort), and content filtering. Admins can enforce security policies without needing separate appliances or add-ons.
- Layer 7 application visibility and control: See which apps and devices are consuming bandwidth (e.g., Netflix, Zoom, YouTube) and prioritize or throttle traffic based on business needs, right from the dashboard.
- Mobile Device Management (MDM) – Meraki Systems Manager: Manage laptops, smartphones, tablets, and other endpoints with integrated MDM. Push apps and updates, enforce security policies, track device location, and remotely wipe lost or stolen devices.
- Zero-touch provisioning: Meraki devices auto-configure on boot, pulling settings from the cloud. This enables fast deployments at scale, especially in distributed or remote offices.
- Wi-Fi with built-in analytics: Meraki wireless access points offer seamless roaming, guest Wi-Fi portals, location analytics (foot traffic, dwell time), and BLE beaconing for IoT.
- Intelligent alerts and real-time monitoring: You can receive proactive alerts on outages, unusual activity, or performance degradation. Live tools like packet capture, ping, and traceroute are built right into the dashboard.
- API-driven automation: Meraki offers robust APIs to automate configuration, provisioning, monitoring, and reporting. Useful for organizations managing large fleets or integrating with third-party systems.
- Seamless integration across product lines: Meraki switches, firewalls, cameras, and APs work cohesively within one dashboard. This gives IT teams end-to-end control over networking, security, and device management — no patchwork required.
All these features make Cisco Meraki especially valuable for multi-site organizations, educational institutions, retail chains, and hybrid workforces that need simplicity, scale, and security.
Cisco Meraki + ITAM: Where this integration lags
- Shallow endpoint telemetry: In comparison to other MDMs, Kandji does not capture device internals such as encryption status, patch level, CPU specs, or app inventory.
- Limited enforcement for non-Apple platforms: Policy depth is considered uneven in the Kadji+ITAM integration for Windows and Androids as compared to macOS and iOS.
- Lacks user granularity: Meraki can perform the base level user associations via log events or directory services but lacks identity-aware mappings found in other MDMs.
Meraki is focused on location-based asset tracking capabilities that make it a suitable choice for enterprises where items need to be closely monitored within a specified geo-boundary. While it doesn’t offer the deepest endpoint control, its cloud-native model makes it a smart integration to provide accurate accountability records.
Cisco Meraki + ITAM: What the integration unlocks
The Cisco Meraki integration with an ITAM helps you track real-time device presence plus its usage and network compliance. It’s especially useful for organizations that value location-based asset tracking.
1. Real-time network mapping
Meraki tracks which Wi-Fi a device is connected to, alongside its last known location. This information gets passed on to the ITAM, making it a breeze to pinpoint the last used location for IT devices in case of misplacements or site-specific audits.
2. Policy enforcement
Any devices found to be breaking a policy (such as missing passcode, app blacklist) are flagged instantly. This status gets synced into the ITAM which makes crisis resolution quicker and more efficient.
3. Controlled user access
Meraki lets you authenticate user access and set visibility according to the device compliance status, permissions, policies, and restrictions. By linking access to device compliance, Meraki ensures that only approved, secure, and managed devices can connect to the network. This minimizes the risk of shadow IT and helps maintain asset accountability via ITAM.
4. Device-network hardware mapping
Meraki can list a device to certain switch ports, VLANs, and access points. With this information in your ITAM, you always know who is using the device and whenever it connects to your network.
5. Location-based asset tracking
Meraki can accurately pinpoint where a device is located, down to the shelf based on Wifi triangulation. This location data when synced with ITAM enables smarter recovery, and incident resolution.
6. Smart geofencing
In case a device leaves a defined geo-defined boundary, Meraki can log a violation and flag the incident initiating instant recovery. Smart geofencing makes ITAM location-aware, risk-sensitive, and automated. It helps organizations protect valuable devices, respond faster to threats, and maintain tighter control over distributed IT assets — all while feeding live insights into ITAM systems.
6. Hexnode UEM: Best for budget-conscious organizations needing full UEM
Why IT loves it
Hexnode provides the full MDM and UEM functionality without the enterprise price tag or complexity. It’s a great choice for teams that want to track Windows and OS in a single system without siloed systems. Plus, it offers a simple and clean UI with low learning curve, strong customer support, and is lightweight yet powerful for SMB to mid-enterprise use cases.
Ideal for
- Mid-sized businesses scaling device fleets
- MPS and multi-client environments
- Orgs with cross-platform and mixed vendor fleets
Why Hexnode matters for fast growing teams
- Provides control over a hybrid environment without a high-ticket price tag
- Ensures compliance regardless of the OS system
Top Hexnode features
- Cross-platform device management: Hexnode supports centralized management of iOS, Android, Windows, macOS, tvOS, and even Fire OS devices. Admins can configure, monitor, and secure all endpoints from a single console.
- Zero-touch enrollment and automated provisioning: With integrations like Apple Business Manager (ABM), Android Zero-Touch, and Windows Autopilot, Hexnode enables IT to provision devices without manual setup, saving time and reducing errors.
- Geofencing and location tracking: Set geofences to enforce location-based policies. You can track lost or misplaced devices, trigger alerts when a device leaves a boundary, and even lock or wipe devices remotely.
- Kiosk mode and app management: Hexnode allows devices to run in single-app or multi-app kiosk mode—ideal for education, retail, and field services. It also supports: app whitelisting/blacklisting, silent app installation/removal, and app version control.
- Policy enforcement and compliance: Apply security policies to enforce password rules, encryption, VPN, Wi-Fi settings, OS version compliance, and restrict hardware features like cameras, Bluetooth, or USB ports. Helps with HIPAA, GDPR, SOC 2 compliance, etc.
- Real-time reporting and dashboards: Hexnode offers live dashboards and custom reports for device status and compliance, app usage and inventory, policy enforcement, and network and data usage analytics.
- Remote actions and device control: Execute key actions remotely. Lock, unlock, wipe, or restart devices. Plus, you can push updates or restrict access and view screens or take remote control (for certain platforms).
- BYOD and COPE support: Hexnode supports Bring Your Own Device (BYOD) and Corporate-Owned, Personally Enabled (COPE) setups. This helps with work/personal data separation, selective wipe, and containerization on Android and iOS.
- Seamless integration ecosystem: Hexnode integrates with popular IT systems e.g. Azure AD, Okta, Google Workspace for identity and SSO; Jira, Zendesk, ServiceNow for ticketing etc.
- Content and email management: Push corporate documents securely, manage access permissions, and configure native or third-party email clients with encryption and DLP controls.
Where does Hexnod lag?
- Event history limitations: Hexnode logs track events such as policy changes, and user assignments but they don’t align the requirements in an ITAM. For example, in Hexnode there is no stage to record ‘In Maintenance’, ‘On Loan’, or ‘In Repair’.
- Lack of deep analytics: Hexnode relies on an ITAM for in-depth reporting. It cannot provide reports on TCO, asset aging, or financial ROI and is mainly focused on security and usage.
Hexnode+ITAM: What the integration unlocks
Hexnode is a modern MDM providing support for a hybrid IT environment. Along with the ITAM integration it provides, it enables real-time asset control, and structured governance for growing teams.
1. Smart app segregation
Hexnode makes it possible to tag assets according to groups and departments. For example you can tag ‘Site Devices’ or ‘Marketing Macbooks’ to the relevant devices. You can then sync organized, tagged data into your ITAM, making it easier to control usage and access.
2. Zero-touch device provisioning feed
It’s time to eliminate manual device tracking. A step up for zero-touch deployment, Hexnode keeps a record of enrollment status, assigned policies, and OEM details. All this data flows into your ITAM, ensuring all data records are accurate with zero manual effort required.
3. Remote asset lockdown
Hexnode can immediately activate Lost Mode when a device is lost, and even lock it remotely to prevent unauthorized access. All these actions are synced into the ITAM for clarity during audits and procurement decisions.
4. Security protocols
Hexnode pushes compliance, encryption, passcodes, and OS versions into ITAM making sure all data is updated, providing tight security.
What people think of these MDMs
| Marketplace | Microsoft Intune | Jamf Pro | Kandji | Cisco Meraki | VMware Workspace ONE | Hexnode UEM |
| Capterra | ★★★★☆ (4.4) | ★★★★★ (4.7) | ★★★★★ (4.8) | ★★★★☆ (4.5) | ★★★★☆ (4.6) | ★★★★☆ (4.7) |
| G2 | ★★★★☆ (4.5) | ★★★★★ (5) | ★★★★☆ (4.5) | ★★★★☆ (4.5) | ★★★★☆ (4.0) | ★★★★☆ (4.6) |
What to consider when choosing an MDM for ITAM use cases
MDM x ITAM integration solves the problem of poor visibility and eliminates security blind spots for you. To get accurate results, make sure you select the right MDM for your business. Here are a few aspects to consider:
1. System compatibility
Ask: Is our IT team centralized, hybrid, or distributed?
You know your stack. Does it have Windows or OS devices? Unless you plan to stick strictly to a single platform, consider MDMs that offer hybrid support for a variety of systems. Making the right choice of MDM while setting up your workflows saves you multiple app switches and data syncs.
2. Integration ecosystem fit
Ask: Does this MDM plug cleanly into our existing stack (identity, ITAM, ticketing, security)?
At same time, the right MDM should be able to bi-directionally integrate with your ITAM tool, identity providers and ticketing systems. For example, Microsoft Intune is the obvious choice for Microsoft-first orgs. Make a list of all critical things about your stack to make a fully-informed decision.
3. Growth trajectory and scalability
Ask: Will our device count double in the next 12–24 months?
MDMs form the foundation of the IT structure at your business. It should have the ability to grow alongside your business. In case your business expands within the next few years, you shouldn’t have to uproot your MDM to facilitate a growing fleet of assets, functionalities, and security requirements. Startups may end up overpaying for enterprise-level MDM tools, while large orgs have a higher chance of outgrowing entry-level tools like Hexnode.
4. Easy onboarding
Ask: Can my team realistically manage and customize this tool?
Given the complexity of your IT fleet, choose an MDM that is easy to use and understand by your team. You don’t want anything too complicated that’s harder to implement across the organization. Jamf Pro is a great tool, but it has a steep learning curve suited for Apple-savvy orgs. On the other hand, Kandji offers automation for lean teams without the extra help.
5. Vendor support
Ask: Is this MDM provider well-supported, frequently updated, and enterprise-grade?
For the MDM to be able to function through the long-run it is important to have excellent vendor support. Your job is to minimize downtime so that IT workflows don’t get disrupted. Lookout for tools that have a yearly roadmap plan, SLA backed uptime and a strong existing user base.
6. Total cost of ownership
Ask: Are there hidden costs — training, API usage, support tiers, per-device pricing?
Don’t just consider the price when making a cost evaluation plan to buy an MDM. Also, keep in mind the hidden costs that may be involved. A low upfront cost may come with premium features at an extra charge. Actively consider long-term costs, rather than just the license price.
| Criteria | Microsoft Intune | Jamf Pro | Cisco Meraki | VMware Workspace ONE | Kandji | Hexnode |
| System Compatibility | High | Medium | Medium | High | Medium | High |
| Integration Ecosystem Fit | High | High | Medium | Medium | Medium | Medium |
| Growth Trajectory & Scalability | High | High | Medium | High | High | Medium |
| Ease of Onboarding | High | Medium | High | Medium | High | High |
| Vendor Support | High | High | High | High | High | Medium |
| Total Cost of Ownership (TCO) | High | Medium | High | Low | High | High |
How EZO AssetSonar enhances MDM integration
With the help of an ITAM such as AssetSonar integrated with an MDM, you can take control of your stack through its lifecycle. Real-time syncs with tools such as Jamf Pro and Workspace One provide you with device identity, asset details, and usage data all in one place– centralizing IT management. Stay in the loop as soon as an asset is provisioned, a new policy is enforced or reassigned, and eventually offboarded and retired.
With all the relevant data synced in AssetSonar, you can now take informed procurement decisions on the number of license seats required based on user assignments and even predict future trends.
Updated compliance data received through the MDMs in AssetSonar helps you plan tension-free audits. Any red flags can be easily highlighted, and a remedial course of events initiated to ensure timely maintenance of all IT devices. Granular IT transparency with lifecycle visibility helps cut down costs and improve device security and productivity throughout the organization.
Conclusion: Pick the right MDM, power up your ITAM
Every MDM tool offers a different level of security and access control, and visibility into your IT devices– select the one that fits your needs. Do your research on what works for your stack? If you own a majority of Apple devices then Jamf Pro or VMware Workspace may work for you. If you require advanced features such as geofencing and remote device lock, then Hexnode or Cisco Meraki are good options.
Using MDMs and ITAMs in isolation is only going to result in fragmented asset data leaving your team to retrieve bits and pieces from different devices. The integration of both tools is a powerful action that gives you complete control over IT asset lifecycle management.
“Want to see how AssetSonar unifies identity, MDM, and asset governance? Sign in for a free trial .”
Disclaimer: References to non-EZO products, logos, and brands in this blog are for informational and comparison purposes only. All trademarks and brand names remain the sole and exclusive property of their respective owners. Inclusion of such trademarks and/or brand names in this blog do not imply any affiliation, endorsement, or sponsorship with EZO or the EZO product line.
Frequently Asked Questions
What is MDM-ITAM integration?
MDM-ITAM integration is linking mobile device management data (device state, OS version, compliance, users) with IT asset management systems to give full lifecycle visibility and better control.
Why should a company integrate MDM with its ITAM tool?
It reduces data silos, automates device tracking, improves compliance, speeds up onboarding/offboarding, and prevents duplicate purchases or unmanaged devices.
What device info is usually pulled from MDM into ITAM?
Common fields: device serial, OS/version, user assignment, status (active/inactive), compliance status, last check-in, security posture, location.
Can MDM handle software licenses as well as hardware in ITAM?
MDM handles some software/app installs; for full license tracking you need ITAM to map entitlements, version usage, expiration, and reconcile usage vs license count.
What are key challenges when implementing MDM-ITAM integration?
Challenges include inconsistent data schemas, mismatched identifiers, syncing frequency, handling inactive devices, data cleanup, and permissions/security concerns.
How automatic is this integration typically?
Most solutions allow automated data flow on triggers or scheduled syncs. Devices enrolled in MDM can auto-populate into ITAM. Some manual review or exceptions may remain.
How do integrations help in offboarding or retiring devices?
When a device is removed from MDM or decommissioned, ITAM can trigger workflows to retire it, reclaim licenses, wipe data, and update records automatically.
What metrics improve with MDM-ITAM integration?
Metrics like device utilization, compliance percentage, idle devices, license usage vs purchase, total cost of ownership, and mean time to provision improve.
How often should data sync between MDM and ITAM occur?
Best practice is frequent syncs — daily or more for compliance/security metrics; less often may suffice for financial/lifecycle updates.
Which MDM platforms are commonly used with ITAM tools?
Common ones include Microsoft Intune, Jamf Pro, VMware Workspace ONE, Cisco Meraki, Hexnode, Kandji. These give strong data and API access.
How do I ensure data consistency between MDM and ITAM?
Use matching identifiers (serial, device ID), enforce standard naming/tagging, handle inactive or orphaned devices, regularly audit records and resolve discrepancies.
What security advantages come from MDM-ITAM integration?
Integration helps detect uncompliant devices, enforce security policies, remote wipe, patch management, ensure only approved devices access sensitive data.
Can AssetSonar work with MDM tools to streamline IT-asset lifecycle?
Yes — by syncing device data, reflecting compliance and user info, feeding into lifecycle workflows (procurement → retirement), helping maintain audit trails.
How does integration affect costs and ROI?
It reduces manual tracking costs, cuts down on redundant purchases, improves maintenance planning, increases compliance (avoiding penalties), so ROI often seen within months.
What features should I look for when choosing an ITAM tool that integrates well with MDM?
Key features: strong API/connectors, reliable field-mapping (IDs, owners), ability to sync status/compliance, regular sync schedule, flexible reporting and workflows.


