For all businesses using technology, software assets make up a crucial component of their IT infrastructure.
Operating systems, applications, and cloud-based and on-premise software make up the software IT inventory and they have a significant impact on a company’s daily operations. Managing the usage, procurement, and security of these assets—including optimizing SaaS spend—comes under the scope of ‘software asset management’.
What is Software asset management (SAM)?
In essence, software asset management (SAM) includes all the necessary processes to plan, control, and protect your investments in software assets throughout each phase of their lifecycle. Having a well-defined software asset management mechanism reduces licensing risks, minimizes overhead costs, and eliminates software hoarding while also acting as a valuable strategic asset for your company.
For example, an educational institution has multiple software applications such as learning management systems, statistical and research software, and other classroom-specific software. Managing different software has become difficult. To streamline software asset management, they want to implement a well-defined process through a solution that helps optimize software allocation, secure access and maintain compliance.
However, before you jump into implementing a software asset management process, it is important to understand software asset management risks – or more precisely, the risks of poor software asset management. For example, devising a process without clear goals and objectives and employee training may fail to serve its purpose – a topic we’ll cover in another blog.
First, let’s explore software asset management, why it’s pertinent, and the benefits it brings to your business.
Stop overspending on software you don’t use.
Why does your business need software asset management?
Continuous monitoring plays a crucial part in avoiding software asset management risks. Lack of real-time visibility increases the likelihood of over-licensing, data hoarding, or security breaches. Let’s discuss these in detail below:
1. Costs of over-licensing
Did you know companies were reported to waste $18 million on their software assets in 2023? The numbers show the same trend of IT wastage today as more businesses move towards cloud and SaaS subscriptions but tend to squander resources on unused software. However, now, more companies are trying to focus on curbing the costs of over-licensing.
Without an effective SAM solution, there is a higher probability that your financial resources are draining without your knowledge due to over-licensing.
2. Manual tracking
Manually tracking your software assets is labor-intensive and inefficient. When tracking them via spreadsheets, you don’t get real-time data on license states, their usage, and the custody of these assets. Spreadsheets cannot also monitor employees’ activity if they log in to a software.
Lack of a software asset management tool may result in unauthorized user access, unaccounted software, and using an expired license that can put your company at potential compliance and fiscal risks.
3. Software hoarding
Software hoarding is the accumulation of redundant data within an organizational system, a practice that leads to digital clutter. This happens due to inadequate data management strategies including insufficient data governance, lack of awareness about data relevance, and hesitancy in deleting seemingly inactive information.
Software hoarding isn’t an anomaly. According to Delphix’s article, over 90% of the data stored by companies is redundant. Besides incurring heavy expenses, this unused data leaves sensitive information vulnerable to cyber attacks, convoluting your IT landscape further.
4. Regulatory compliance
Without a proactive approach toward software asset management, you may end up with expired licenses, delayed renewals, and outdated software versions. IT regulators have now drawn up strict guidelines to counter the practice of using non-compliant software products.
By not adhering to proper regulatory guidelines, users unintentionally expose the organization to hefty penalties and reputational damages. On average, one non-compliance event alone results in a $4 million penalty!

5. Employee access
With the remote and hybrid culture on the rise, employees need access to different software from different networks. Manually granting access to every employee can be quite tedious and time-consuming, which may affect the timely completion of tasks.
It may also lead to misallocation of licenses which can result in a software’s overutilization or under-utilization. Some team members might lack access to important tools, which can eventually hinder their productivity.
3 steps to implement software asset management process
A well-defined SAM approach helps to minimize risks and maximize returns. To make the most of this process, it is important to focus on each risk and its impact to strategize on finding the right process fit for organizational needs.
1. Plan and streamline the license procurement process
IT managers are responsible for purchasing software and negotiating with vendors. Before initiating a purchase, they need to collaborate with different departments on technology requirements.
To streamline the process, they can plan and communicate a process document that states the steps to be followed by all departments. SAM software allows users to create requests and add requirements in the same workflow request. IT managers can review these requirements based on available versions and deploy existing software or proceed with procurement of a new one.
2. Update and maintain inventory
Maintaining a centralized software inventory database is crucial to finding updated software details. With the help of SAM software, IT teams can use automated discovery tools to maintain inventory in real-time and ensure the inventory database is always accurate.
Additionally, teams can leverage software normalization to standardize software versions as users download or upgrade different versions of the same software.
3. Analyze metrics and measure usage
Once the software database is centralized, it is important to monitor different applications, versions, and seats to avoid over and under-licensing. Software asset analyst works on analyzing which software applications are used, which versions are installed, and how many license seats are available.
They can use an automated solution to measure important metrics. Having complete visibility will help them reallocate available licenses to cover additional needs and save money on purchasing new licenses. Similarly, they can fetch software reports to stay updated on contract expiration, renewals, and payment deadlines.
Centralize license data, track usage in real time, and cut wasted spend
Benefits of a streamlined software asset management process
A streamlined software asset management process offers numerous financial, operational, and regulatory benefits.
Implementation & management of software tools
By implementing an IT asset management solution across the organization, you get a transparent view of the state of your software assets. Through it, you can effectively manage a range of software assets as well including operating systems, productivity tools like Google Workspace, software licenses, cloud software, and antivirus tools.
In addition, software asset management creates a smooth workflow that starts from a software request and concludes at its installation. This workflow is defined and automated, mitigating the risk of incorrect assignment. Most software asset management tools integrate with active directories, so you can easily fetch employees’ data and provision assigned devices against them.
Another key benefit is the maintenance of an updated software inventory. You can achieve this by continually tracking software assets in real-time including updates, installations, and cancellations. Beyond inventory management, software asset management lets you implement access control, which prevents unauthorized people from accessing your systems. Two-factor authentication, identity management integration, and software download permission are a few examples of this.
Compliance
Software asset management systems facilitate asset audits to verify that your software assets comply with licensing agreements, protecting you from compliance penalties and inadvertent piracy-related risks. The process begins with collecting data on software usage, including licenses, installations, and user access. This data is then compared with the terms outlined in the agreements. In case of any discrepancy, the IT teams will be notified automatically so that they can rectify any non-compliance issues.
Monitoring & usage tracking
With automatic agent-based scans, you may view how each software is being used on your company-owned devices. For instance, you can whitelist or blacklist certain applications or programs, ensuring only certain types of software are being used in your company. As an IT administrator, you can also enable download permissions for the users so they can only install authorized software.
With in-built license modules, you’re able to track the number of licenses issued, usage limits, and available software users. By implementing this, you can significantly reduce software misuse and prevent unauthorized users from accessing, mitigating security-related vulnerabilities.
Reallocation of software applications
By monitoring software usage patterns, you can easily identify underutilized licenses and therefore stop paying for surplus licenses. As you track software usage patterns, you can easily identify the number of underutilized licenses. This protects you from paying for surplus or unused licenses.
Apart from saving expenses, reallocating your software to the right resources optimizes budget allocation and software usage companywide. Once your software distribution aligns with your business’s actual needs, you’ll be able to make more accurate and cost-effective software investments.
Vendor relation management
It is very critical for companies to maintain a solid relationship with suppliers aka IT vendors. SAM systems contain a comprehensive and up-to-date record of all your software vendors. Having an accurate directory of all vendors allows you to streamline your software procurement with features like pre-built purchase orders.
Beyond record-keeping, most SAM tools offer centralized contract management that consolidates all contracts, payments, and renewal details in a single dashboard. The streamlined approach lets you track contract expiration dates, manage renewals, and make timely payments.
Ready to Explore EZO AssetSonar?
Software asset management best practices
1. Identify trends with custom reports

As a business owner, you need transparent insights into how your software assets are being used company-wide. With this visibility, you can decipher usage trends and make future decisions related to license purchases, asset allocation, and budget spending. For greater clarity in these trends, keep track of metrics such as peak usage periods, underutilization rates, software performance metrics, and renewal and extension rates.
By regularly analyzing these metrics, you’ll be able to stay proactive in software management and respond quickly to changing business needs. To support your procurement efforts further, you should assess how each software is being installed, configured, used, and accessed. Having a clear idea of the number of licenses your company needs will let you establish a standardized process for procuring licenses.
2. Utilize unused licenses
According to a report by Nexthink, more than 50% of software that companies pay for is going unused. With a software asset management process, you can first identify these dormant licenses. Once identified, you can strategically reallocate them to departments and teams experiencing higher demand.
By utilizing the existing software, you can ensure that the number of licenses you’ve purchased is being used to their full extent. This significantly reduces the expenses associated with unused or underused licenses.
3. Manage software expenditure
You should be particular about cost optimization and avoiding any unnecessary expenses. To manage your IT expenditure effectively, you need insights into software usage, with a detailed breakdown of how each software is used across different departments. Technology spend reports provide a comprehensive breakdown, detailing technology spend per employee, location, department, and year.
Once you have access to this clarity, you can implement different strategies to curtail spending. This includes negotiating contracts with vendors based on actual usage, switching to more cost-friendly alternative software, or eliminating redundant applications.
4. Automate IT processes
Implementing software asset management practices or solutions reduces manual workflows and your dependency on IT personnel for routine tasks. Spreadsheets are likely to miss out on license information when tracking assets manually as they’re not tangible. In addition, manually entering contract information, vendor details, and license renewal dates for every software being used organization-wide can be quite tedious.
Even one inadvertent omission or incorrectly mentioned detail can cause compliance complications and compromise the accuracy of your software data. To avoid these hassles, implement workflows such as automated software discovery, asset tracking, license tracking, contract management, and compliance monitoring.
5. Automate billing and keep track of renewals, expiries, extensions
You need to keep a close eye on software renewals, expiry dates, and extensions to continue using these applications without facing non-compliance. Manually performing these tasks is likely to cause human oversight when tracking multiple licenses, delayed response to renewals, and overlooking critical updates. Failure to upgrade to the latest versions or using expired software unknowingly exposes your company to license breach penalties.
To avoid these hurdles, you must implement best licensing practices that can save approximately 30% of your software budget and maintain compliance with industry regulations. One such practice is automated notification alerts well in advance of license renewal dates, payments, and expiries so that you don’t have to memorize them. Besides licensing, you can improve contract management with notifications for contract approvals, expiry, and activation.
These alerts can also be configured for a range of other events including check-in/check-out, reservations, service event, asset tracking and purchase orders. You can achieve even greater timeliness and efficacy by integrating an automatic billing method to vendors, which will generate invoices based on actual software usage.
6. Role-based access control
Cyberattacks are one of the leading risks for companies, estimated to cause annual losses worth $10.3 trillion by 2023. You need robust measures to counter cyberattacks such as data theft, hacking, and embezzlement. One way is by implementing Role-Based Access Control (RBAC). RBAC makes sure that employees have access to information and functionalities that are relevant to their roles. This prevents unauthorized people from accessing sensitive company data and eliminates the misuse of your software tools.
To implement RBAC, you can define user roles and associated permissions based on job responsibilities. SAM systems usually provide administrative controls that let you configure access rights for different users. This control ensures that only authorized persons can make changes to software configurations, view license information, and grant user permissions.
Important features of software asset management solutions
1. License management
License management is an important component of the software asset management lifecycle and usually contains the following features:
- Compliance monitoring: It uses algorithms to compare how existing software is being used with relation to the terms and conditions specified in the license agreement. In case of any deviations, you will be notified to avoid any compliance risk.
- Automated alerts: Alert notifications keep you well-informed in advance about license expiry dates. These alerts are directed to the relevant stakeholders such as IT staff or procurement teams so that they can make timely renewals.
- Audit trail: An audit trail logs all changes and activities related to software licenses. This increases transparency and lets you trace every action taken
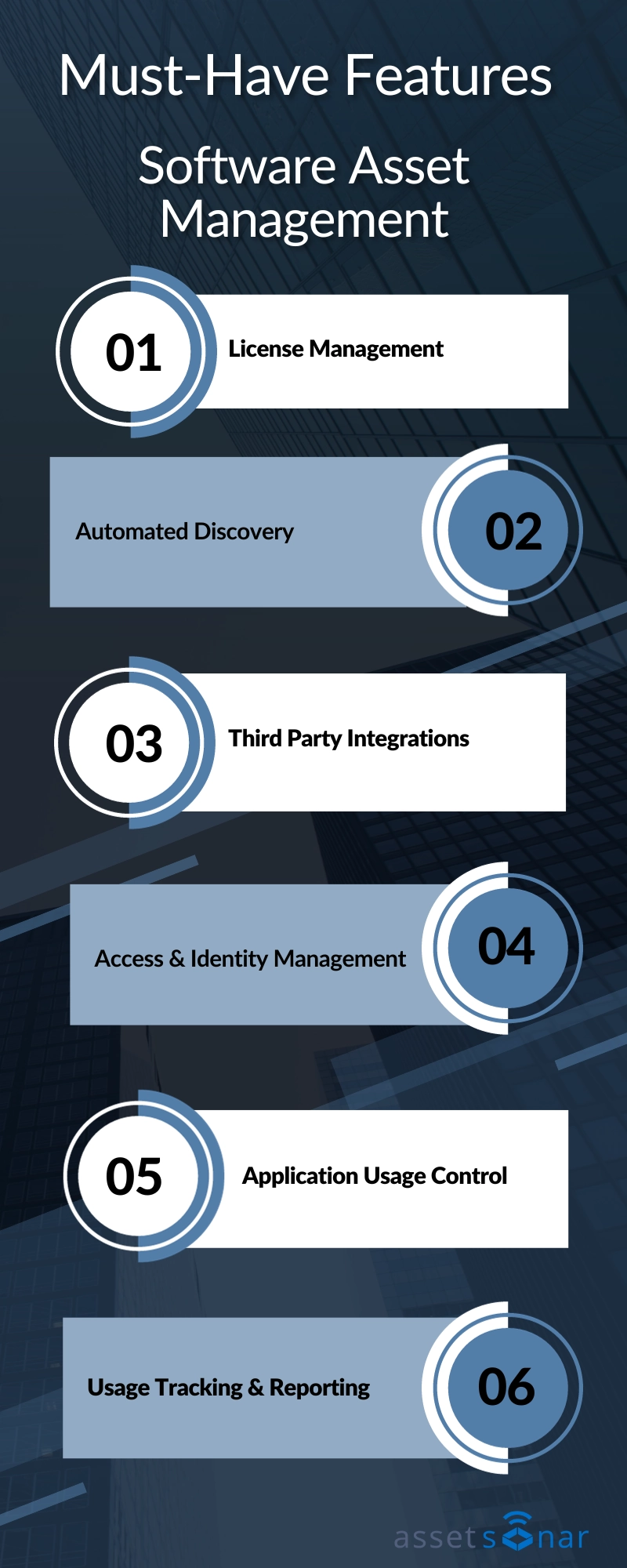
2. Automated discovery
Built-in agent-based scans continually monitor your organization’s network to give you real-time visibility into your software inventory:
- Continuous scanning: This automated process constantly monitors changes in your software landscape including new installations, removals, and updates, and keeps your inventory up-to-date.
- Device recognition: The discovery agent recognizes all devices connected within your organization’s network. These include company-owned computers, servers, remote devices, and Bring Your Own Devices (BYOD). This lets you create a standardized catalog of all software installed on recognized devices.
- Hardware Inventory: Automated Discovery extends beyond software recognition and identifies all physical devices connected to the network. It even includes detailed information such as device specifications, configurations, and geographical location. With hardware inventory visibility, your overall IT asset management process becomes more streamlined.
3. Third-party integrations
Modern IT infrastructures are interconnected and integrate seamlessly with each other to ensure optimized IT processes. A good software asset management software must integrate with the existing IT service management tools to simplify the jobs of IT personnel and to help enhance customer and employee experience. Examples include integrations with Zendesk and Jira. When an ITAM or SAM tool is acting as a single source of information and actions, IT teams can perform these actions on the tickets without having to constantly switch between tabs and tally information.
Other must-have integrations are with Google Workspace and Okta Directory. With the former, you can track the usage of all software associated with Google Workspace. Okta, which is a leading identity and access management solution, lets you put user access and role-based access control (RBAC) in place.
Other important integrations are with mobile device management solutions like Workspace One and network asset management integrations. The former enhances security and control across your network. Network asset integrations allow you to properly manage assets like routers, switches, servers, firewalls, and printers. With a controlled network infrastructure, you’re able to protect your system from network disruptions and operational halts.
4. Access and identity management

Access and identity management gives secure access to critical company resources such as emails, databases, software, data, and applications to verified individuals. You can enhance your security protocols by having password-protected systems and requiring sign-ins from company emails only.
To add an extra layer of security, set up multi-factor authentication as a prerequisite to access the network. For swift access, software asset management systems should support integration with Single Sign On (SSO) solutions so that teams can access multiple applications with the same credentials.
5. Application usage control
To strengthen your network security and compliance initiatives, a robust software asset management solution gives you the freedom to define the types of software permitted. This can be done by blacklisting or whitelisting certain applications.
Blacklisting restricts the usage of unauthorized or potentially risky software. For example, you might want to blacklist peer-to-peer file-sharing tools and outdated and insecure software versions. Your teams can then not download or access these tools.
Whitelisting, on the other hand, means that your employees can access only pre-approved and authorized software. These may include Microsoft Office Suite, project management workflows like Zendesk, Jira, and proprietary company applications. Having a whitelisting mechanism in place ensures that only applications that are compliant with regulations, company policies, and security standards are being used company-wide.
6. Usage tracking and reporting capabilities
You’re likely spending thousands of dollars every month for a software license but the real question remains – are they being used to their full capacity? To understand this better, software asset management solutions incorporate different metrics that demonstrate usage patterns.
These are activity per user or device, usage per processor, peak usage periods, percentage of inactive licenses and department-specific usage. This level of specificity, combined with customizable report generation, lets you make informed and data-driven business decisions.
The future outlook for ITAM and SAM
Organizations, small or large, require a robust solution to manage their IT assets, categorized into HAM and SAM – two main parts of ITAM. Initially, organizations relied on on-prem solutions and adapted on-prem HAM and SAM solutions to manage hardware and software assets.
With evolving technology, more organizations are using SaaS applications and switching to hybrid models. This makes it difficult for existing tools to discover and manage the entire IT infrastructure on the cloud.
SaaS management tool provides a combined ITAM and SAM solution to cater to changing IT environments. It offers integration with various discovery tools to manage on-prem, cloud-based, and even hybrid models, all at once. This helps organizations with complex IT environments to minimize costs and transform their business processes with ease.
IT assets, whether they are hardware or software, require significant investment and form the backbone of your business. If not managed properly, these assets can quickly turn into a liability and pour your investment down the drain. Software assets require even greater vigilance as they’re not tangible and can go unnoticed.
To address these hurdles, implementing a software asset management process is a strategic choice and a smart investment. With compliance monitoring, usage tracking, and license management, you’ll not only protect your systems from data breaches and penalties but also utilize the full potential of your software assets.
Frequently asked questions
What is Software Asset Management (SAM), and why is it important?
SAM is the practice of managing and optimizing software assets to ensure compliance, reduce costs, and improve efficiency.
How does SAM differ from IT Asset Management (ITAM)?
While ITAM encompasses the management of all IT assets (hardware and software), SAM specifically focuses on software assets and their lifecycle.
What are the key stages in the software asset lifecycle?
The lifecycle includes procurement, deployment, usage monitoring, maintenance, and retirement of software assets.
What tools are commonly used for effective SAM?
Tools like AssetSonar, ServiceNow, and Flexera are popular for automating and streamlining SAM processes.
What are the key business challenges that software asset management addresses?
Some common challenges it solves are software overspending, unused licenses, and compliance penalties.
How does software asset management contribute to increased security and compliance?
Software Asset Management identifies patches for software vulnerabilities and checks whether your assets are adhering to licensing agreements. This, coupled with role-based user access, prevents unauthorized people from accessing your systems and maintains compliance standards.
How can software asset management help me reduce business costs?
Software Asset Management curtails over-licensing. This ensures that you’re not spending money on software that is not needed by your company. It also highlights underutilized software that can be reallocated to other departments and teams. Instead of purchasing new licenses, you can use the existing ones, thereby reducing procurement costs.
What integrations does software asset management support?
Common Software Asset Management solutions can be integrated with project management workflows like Zendesk and Jira. You can also integrate them with Google Workspace, access management tools like Okta Directory, and network management tools like Open-AudIT.
How does SAM contribute to cybersecurity?
By ensuring only authorized software is used and keeping software up-to-date, SAM reduces vulnerabilities and enhances security.
Is SAM applicable to cloud-based and SaaS applications?
Absolutely. Modern SAM practices encompass cloud and SaaS applications, ensuring efficient and compliant use.
What are the typical steps or process of implementing Software Asset Management?
A common SAM process involves:
- Assessment: Identifying all software assets and current usage.
- Standardization: Documenting and streamlining procurement processes.
- Auditing: Regularly auditing software licenses and subscriptions.
- Cleanup and Optimization: Reconciling discovered software with entitlements, reclaiming unused licenses, and optimizing deployments.
- Implementation: Setting up ongoing monitoring, reporting, and lifecycle management.
What are the best practices for effective Software Asset Management?
Key best practices include clearly defining a SAM policy, selecting appropriate SAM tools, centralizing all software asset data, categorizing licenses and analyzing usage, implementing robust procurement policies, forecasting software budgets, and performing regular software audits.
What features should a good SAM solution or tool have?
An effective SAM solution typically includes license management, automated software discovery, third-party integrations, access and identity management, application usage control, and comprehensive usage tracking and reporting capabilities.
How does SAM address challenges like shadow IT and SaaS sprawl?
SAM solutions, especially modern Software Asset Management Platforms (SMPs), help track and manage all software, including SaaS applications, providing visibility into unauthorized or unmanaged software (shadow IT) and helping control the proliferation of SaaS subscriptions (SaaS sprawl).
What is software hoarding, and how can SAM prevent it?
Software hoarding refers to purchasing or holding more software licenses than needed, often due to a lack of visibility or control. SAM prevents this by providing accurate data on software usage and license allocation, enabling organizations to avoid unnecessary purchases and reclaim unused licenses.
How does role-based access control (RBAC) work in software asset management?
RBAC in SAM restricts software access based on user roles, ensuring only authorized users can install or use licensed software. This helps maintain compliance, reduce security risks, and control software distribution within the organization.







