Introduction: Why asking every team doesn’t scale
You don’t hear about the new project management app when someone requests it. You hear about it when Finance flags a $20,000 auto-renewal you never even approved. No security check. No budget sign-off. No warning. And now it’s your problem.
This isn’t a rare scenario. It’s the everyday reality for IT managers in 2025. SaaS adoption is growing faster than approval workflows can keep pace. The average mid-market company now runs 100+ SaaS apps, but IT is typically aware of only a fraction. Nearly 40% of purchases happen outside IT’s budget oversight, and half of those licenses sit unused.
The old way of discovering apps—chasing departments for answers, sending surveys, updating spreadsheets—was always slow. In today’s hybrid workplace, it’s useless. By the time you’ve finished compiling responses, five new apps have already been onboarded.
To keep up, IT needs a new mindset. Instead of playing detective, you need to think like an “air-traffic control tower”. You must always be aware of what’s coming and going.
That’s the promise of this guide: a faster, automated path to full SaaS visibility. We’ll show you how to uncover every app in your environment including the ones flying under your IT team’s radar, without endless surveys or guesswork. By the end, you’ll know how to turn SaaS discovery into a repeatable system that delivers what every IT leader wants: control without chaos.
What’s hiding in your SaaS stack and why it’s a business risk
Even if you think you have a handle on your SaaS stack, odds are high that IT only sees part of the picture. Research shows that 42% of SaaS applications are adopted outside IT’s visibility. These blind spots create financial waste, compliance headaches, and security vulnerabilities.
The following might be lurking in your company’s tech stack:
1. Apps signed up with personal emails
Employees often register apps with Gmail or Yahoo accounts. Because these bypass SSO, they remain invisible to IT. The danger is that sensitive company data gets tied to accounts IT can’t monitor or revoke when employees leave.
2. Auto-renewing tools no one uses
Most SaaS vendors default to auto-renewal. The “subscription culture” is silently draining money out of people’s and organizations’ pockets. Without oversight, unused apps quietly drain budgets for another year. Gartner estimates that 25–30% of SaaS spend is wasted on unused licenses, often due to forgotten renewals.
3. Multiple tools for the same job
Departments frequently adopt overlapping platforms such as two file-sharing tools, three project trackers, or competing LLM tools for productivity. This redundancy creates duplicate spend, fragmented data silos, and inconsistent workflows.
4. SaaS purchases that bypass procurement
IDC reports that 70% of SaaS spend happens outside IT’s budget oversight. Tools purchased on credit cards or spread virally from free trials rarely go through security or compliance checks. The result? Unvetted vendors handling sensitive data under the radar.
5. Apps with weak compliance profiles
Shadow IT apps often lack enterprise-grade safeguards like SSO, MFA, or signed data protection agreements (DPAs). Productiv found that unsanctioned apps carry fewer compliance certifications than IT-managed tools. In regulated industries, that can trigger GDPR or HIPAA violations—and the fines that follow.
Think of your SaaS environment as an airport full of flights taking off and landing. Without a “SaaS visibility control tower”, no one knows what’s in the air, where it’s headed, or when it lands. SaaS discovery acts like radar, giving IT the visibility needed to prevent collisions.
It’s important to remember: shadow SaaS isn’t always malicious. Teams often adopt tools to move faster or bypass red tape. The real challenge for IT isn’t blocking it entirely, but turning shadow IT into supported IT by balancing agility with governance, security, and cost control.
Now, let’s dive into the different ways you can achieve SaaS visibility!
How SaaS discovery works: Strengths and blind spots
Not all SaaS discovery methods are created equal. To gain full visibility, IT teams need to understand the three core lenses of discovery.
- Financial lens: What’s being paid for.
- Identity lens: What’s officially provisioned via company-wide SSO.
- Usage lens: What’s actually happening in employee browsers.
Companies that combine all three can uncover 2–3x more apps than those relying on just one. Here’s a breakdown of the most common discovery methods, their advantages, and their blind spots:
| Discovery method | What it shows (Strengths) | What it misses (Weaknesses) |
| Expense reports and finance data | Paid SaaS subscriptions leaving a financial trail, i.e. credit card charges, invoices, reimbursements. Good for catching shadow purchases. | Free/freemium apps and real-time usage. Data only appears after spend occurs; no visibility into who is using the tool. |
| SSO/Identity provider logs (Okta, Azure AD, Google Workspace) | Centrally sanctioned apps integrated with corporate login. Tracks access, roles, and supports automated offboarding. | Anything outside SSO. Only ~30–40% of apps are typically SSO-integrated. Shadow IT (personal logins, standalone accounts) remains invisible. Some vendors charge extra (“SSO tax”). |
| Device management and endpoint agents | Installed software on corporate laptops and mobile devices, including desktop apps and some extensions. Useful for license compliance. | Browser-only SaaS. Weak coverage for remote workers. Deployment overhead and privacy concerns may cause employee pushback. |
| Browser tracking extensions | Real-time SaaS activity: logins, domains, usage frequency. Strongest method for detecting shadow IT and actual adoption trends. | Coverage depends on rollout across all devices. Limited historical data. Requires clear privacy policies to avoid employee resistance. |
Pro tip: Layer your SaaS discovery methods
No single discovery method gives you the full picture. The IT teams with the best visibility don’t rely on one lens, they layer multiple approaches to cover each other’s blind spots.
- SSO logs confirm sanctioned apps.
- Browser data surfaces shadow IT.
- Finance scans highlight spend that slipped through.
- Device agents capture installed software.
Most modern SaaS management platforms now combine six to nine different discovery methods to achieve near-complete coverage.
The takeaway? True visibility requires redundancy. By layering methods, IT ensures that what one source misses, another catches. This gives you a reliable, 360° view of your SaaS environment.
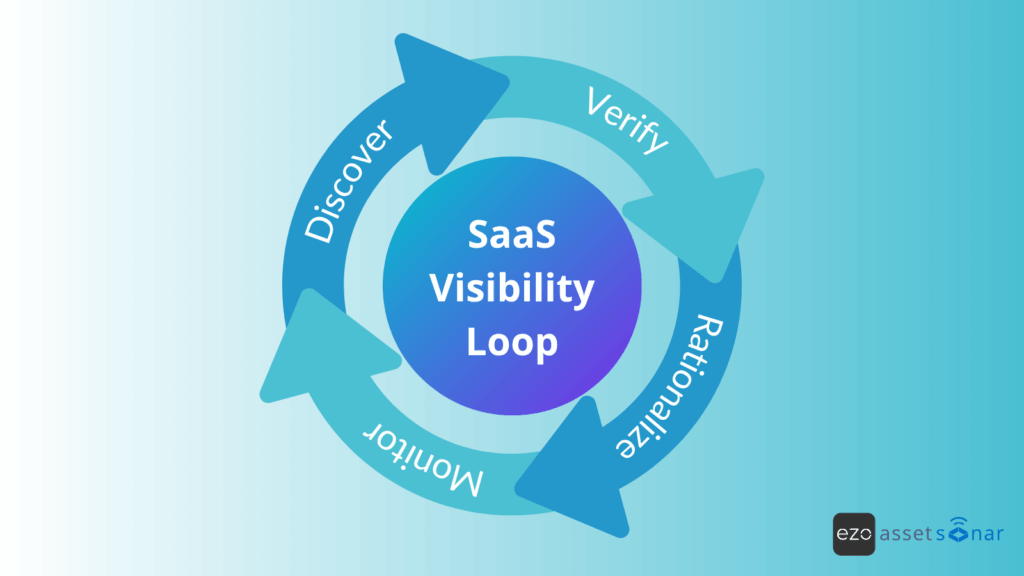
The SaaS visibility loop: A repeatable audit process
A SaaS audit isn’t a one-time clean-up, it’s a continuous system. That’s why we call it the SaaS visibility loop. It’s designed to run on repeat, giving IT consistent oversight instead of once-a-year surprises.
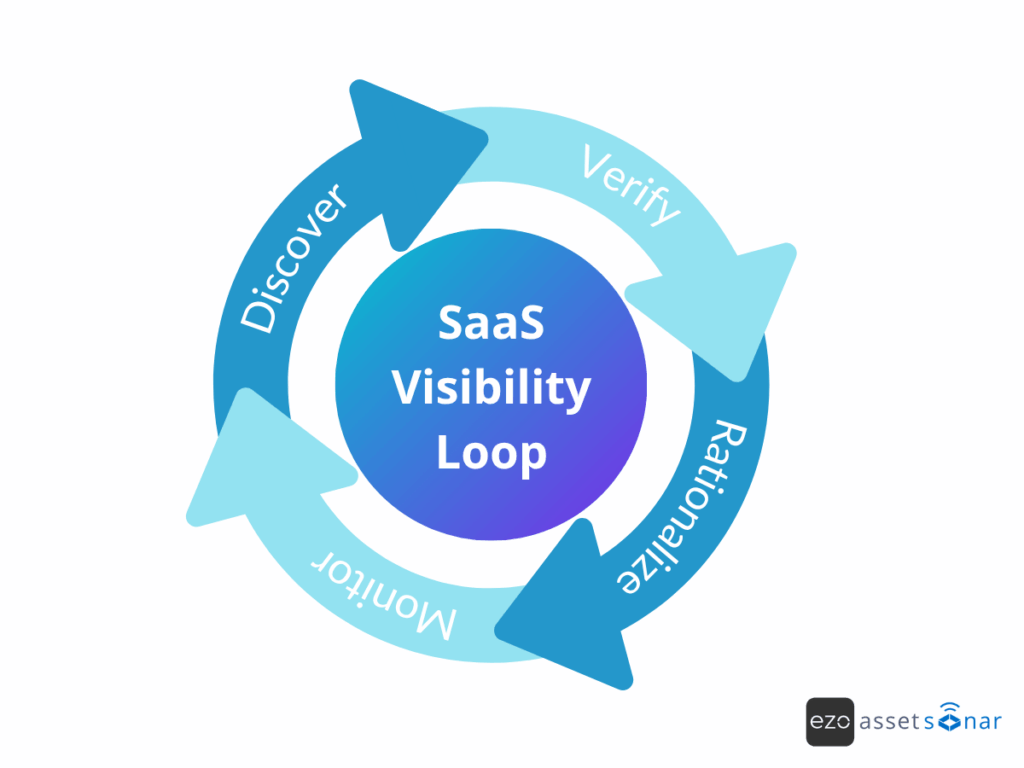
- Discover – Capture usage through browser tracking, SSO logs, and finance data.
- Verify – Confirm ownership, identify duplicates, and flag compliance risks.
- Rationalize – Eliminate waste, consolidate overlapping tools, and right-size licenses.
- Monitor – Keep discovery running in real time, not just during annual audits.
Organizations that follow this loop regularly gain a measurable edge: sharper visibility into their SaaS environment, significant cost savings, and a stronger security posture.
Next, let’s break down each step and show you how to put the loop into practice.
Step 1: Start with browser tracking for real-time discovery
Since most SaaS tools are accessed through the browser, this is the best place to begin your discovery process. Deploy a lightweight browser extension or agent across Chrome, Edge, or Firefox to capture SaaS activity in real time. Many SaaS management platforms include this capability, and IT can also enforce extensions through enterprise browser policies.
Once enabled, the tracker immediately surfaces domains, logins, and frequency of use. That’s when surprises appear. You might find, for example, that your design team logs into Figma.com daily, a tool IT had no record of. Discoveries like this highlight the gap between IT’s official inventory and the reality of team-level adoption.
How to use this data:
- Group results by domain, department, and frequency. This creates a clear picture of which teams are using what tools.
- Spot usage patterns. For instance, if Marketing relies heavily on one platform while another tool shows only a single login, you know which apps are strategic and which are outliers.
- Build a master SaaS inventory. This becomes the foundation for rationalization, license optimization, and compliance reviews in later steps.
👉 Pro tip: Transparency is key. Let employees know that browser monitoring is about safeguarding company data and eliminating waste; not spying on personal browsing. Framing it this way builds trust and accelerates adoption. (For more guidance, see our article on building effective Acceptable Use Policies for your employees.)
Step 2: Cross-reference SSO logs with browser data
Browser tracking reveals what employees are really using, but your Single Sign-On (SSO) or Identity Provider (Okta, Azure AD, Google Workspace) shows what IT has formally provisioned. Comparing the two exposes the gap between official IT records and actual SaaS activity. This gap is often much larger than leaders expect.
How to do it:
- Export a list of apps and users from your SSO or IdP.
- Compare it directly with the browser activity from Step 1.
What you’ll uncover:
- Shadow IT hiding in plain sight. If a domain shows up in browser logs but not in your SSO catalog, it’s almost certainly unsanctioned. For example, if Notion.com appears in usage data but isn’t listed in your SSO directory, that signals a rogue workspace operating outside IT’s oversight. These apps need investigation: Who’s using them? What data is stored? Do they need to be brought under IT governance?
- Shelfware and underused sanctioned apps. The reverse is just as important. SSO may show licensed apps with little to no browser activity, meaning you’re paying for tools that employees aren’t using. This can be a low-hanging fruit for cost savings. Downsizing, renegotiating, or consolidating these apps can deliver quick wins.
This is the step where the illusion of control often falls apart. Many IT leaders discover that the number of SaaS apps in use is three times higher than the number officially sanctioned. Turning that hidden sprawl into hard evidence not only strengthens IT’s case for oversight but also unlocks budget conversations and drives rationalization.
Step 3: Scan expense reports and procurement data
To add another layer of visibility, bring Finance into the process. Analyze corporate card statements, employee reimbursements, and procurement records from the past 6–12 months. The goal is simple: uncover SaaS purchases that slipped past IT oversight.
Why this matters:
- Money leaves a trail. Recurring charges from “XYZ Software Inc.” that IT doesn’t recognize usually point to a department head or manager buying tools directly.
- Catches low-visibility spend. Financial data often reveals niche or one-off tools that never show up in SSO or usage logs. A yearly renewal fee might appear on the company card even if the app is barely used.
- Validates hidden spend. Without this step, shadow purchases remain invisible, leaving IT blind to both cost and risk.
How to do it:
- Filter transactions for known SaaS vendors.
- Flag any charges that don’t match IT’s approved inventory.
- Investigate whether they represent shadow IT, niche usage, or redundant contracts.
Keep in mind that expense data lags. You only see it after the purchase and it won’t catch free or freemium tools. But as a safety net, it’s invaluable. Many IT teams discover apps through finance records that never surfaced in browser tracking or SSO logs.
Pro tip: If you’re using a SaaS spend management tool or an ITAM platform with finance integration, much of this process can be automated. If not, even a simple Excel export filtered by vendor names can surface meaningful insights into the companies your employees are buying software from.
Step 4: Identify risk levels and usage patterns
Once you’ve built your complete list of applications from Steps 1–3, the next step is to analyze and prioritize them. Not every app carries the same weight. Some represent serious compliance and security risks, while others quietly drain budget through redundancy or low utilization.
A structured analysis ensures your team invests effort where it delivers the most impact.
1. Flag high-risk apps
The first priority is security. Any application that touches sensitive data but lacks enterprise-grade safeguards should be treated as high risk. Missing features such as single sign-on, multi-factor authentication (MFA), or signed Data Processing Agreements (DPAs) are red flags. Unknown vendors or apps handling customer information without oversight fall into the same category.
Assigning a simple risk score—high, medium, or low—helps you focus attention on the riskiest tools first.
As the saying goes, “You can’t secure what you don’t know exists.” This step ties SaaS discovery directly into your security posture rather than treating it as an exercise in inventory management.
2. Find redundant or duplicate apps
Next, examine redundancy. Shadow IT often introduces multiple tools performing the same job across departments, such as two project management platforms or three competing file-sharing systems.
These overlaps inflate costs and complicate workflows. Consolidating duplicate apps into single, vetted platforms reduces both spend and complexity. In fact, more than half of organizations reported consolidating redundant apps in 2024 to simplify operations and cut costs.
3. Spot low utilization and license waste
License waste is another area where analysis pays off quickly. Comparing provisioned seats against actual usage often reveals immediate savings opportunities. For example, a company may have purchased 50 licenses but only 20 users logged in during the past ninety days.
Those 30 unused licenses represent pure budget leakage. CloudZero estimates that nearly half of all SaaS licenses go unused in the average organization. Prioritizing these mismatches allows IT to right-size contracts, renegotiate vendor terms, or retire tools that no longer justify their cost.
4. Monitor usage trends
Finally, look at usage trends over time. Applications rarely remain static in adoption.
Declining logins may signal a tool falling out of favor or one that was only useful for a temporary project. These are prime candidates for retirement.
On the other hand, a steady rise in usage of a previously small tool could indicate a grassroots favorite spreading across the business. In those cases, IT should review the tool and decide whether to formally support it or replace it with a sanctioned alternative.
By the end of this step, each application in your inventory should be tagged with meaningful attributes such as its risk level, redundancy status, utilization rate, and overall business importance. This structured view turns raw discovery data into actionable intelligence, giving IT the insights needed to cut costs, strengthen governance, and reduce risk as you move forward in the SaaS visibility loop.
Step 5: Build a central SaaS inventory and keep it updated
Finally, consolidate everything you’ve learned into a single source of truth: a SaaS application inventory. This inventory (think of it as your SaaS system-of-record) should capture key info for every app in use. At minimum, include:
- App Name and Description: e.g. “Dropbox – Cloud storage/collaboration.” If helpful, note the category (Collaboration, CRM, Finance, Marketing, etc.).
- Department/Owner: Which team is the primary user, and who is the point of contact or “owner” of the app? (If you discovered an app with no obvious owner, you might assign one or at least a business unit to follow up with.)
- User login method: Does it use SSO/SAML with your corporate identity, or are people logging in with individual accounts/passwords? This indicates how tightly controlled it is.
- License count and usage: How many licenses or subscriptions are you paying for (if known), and how many active users did you observe (e.g. via SSO logins or browser hits per month). This is crucial for tracking waste.
- Spend and renewal info: If available, record the cost (monthly/annual) and next renewal date. This ensures you won’t be caught off guard by auto-renewals. You can proactively review each app before it renews.
- Risk/Compliance score: Based on Step 4’s assessment, mark if the app has any compliance concerns or requires a security review. For instance, a note like “No MFA; GDPR sensitive data – review needed” or “IT-approved, low risk.”
- Integration/IT Support status: Note if it’s officially sanctioned or not. If you plan to integrate it with SSO or other systems, mark that intention. Essentially, is this app now under IT management or still external?
Before you move on, double-check that your inventory reflects every app identified in Steps 1–4. By the time you’ve completed this step, you’ll have essentially audited your SaaS environment and translated the results into hard data.
Most IT leaders are surprised by what they find. It’s common to uncover 20–30 percent more apps than expected, or to realize that entire departments have been paying for overlapping tools without anyone’s knowledge.
That’s why this inventory matters. It’s not just a list, it’s your control tower. With it, IT can finally see the whole picture, make smarter decisions on spend, and keep security and compliance in check. Without it, you’re flying blind.
What to do with the discovery data
Discovery is only half the battle. The real impact comes when you turn raw data into decisions that cut costs, reduce risk, and streamline operations. Otherwise, your inventory becomes just another spreadsheet gathering dust.
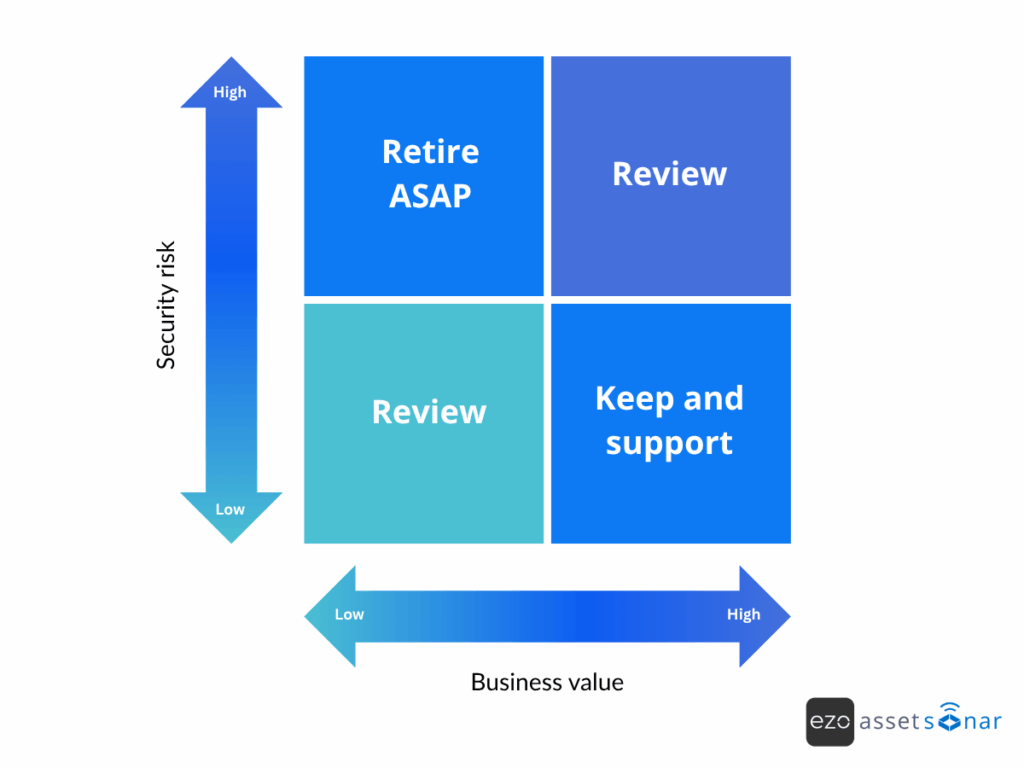
A simple way to start is by rating each app along two axes: Business value and risk level.
- High-value, low-risk apps are worth keeping and supporting.
- Low-value, high-risk apps should be retired as soon as possible.
- Everything else falls somewhere in between; a watchlist for further review.
This framework transforms your audit from a one-time cleanup into a repeatable playbook.
Here are some common insights from a SaaS discovery audit and the recommended actions for each:
Insight 1: Low-usage or unused tools (license bloat)
One of the most common findings from a SaaS audit is license bloat. This includes dozens of apps with very few active users, or overlapping tools where one is clearly more popular than the others. This isn’t just clutter; it’s wasted budget.
Action 1: Cut the waste
The fix is straightforward: cut the waste. Reclaim unused licenses, retire low-value tools, and consolidate overlapping functions. For example, if two teams are split between different project management apps but only one is widely adopted, migrate everyone onto the primary platform and cancel the redundant subscription.
The payoff is immediate. By eliminating that waste, IT can redirect savings into tools that genuinely move the business forward. This is license optimization in action and it sits at the heart of cost control.
Insight 2: Duplicate apps
Another pattern that surfaces in almost every SaaS audit is redundancy i.e. multiple apps doing the same job. You might discover three different note-taking platforms or several business intelligence tools scattered across departments. Each one adds cost, support overhead, and compliance complexity without adding real value.
Action 2: Rationalize the stack
The remedy is rationalization. Evaluate which application is the best fit by weighing cost, features, and security, then standardize on it. The others should be retired or prevented from renewal.
This not only cuts spend but also simplifies vendor management and reduces data silos. Gartner has called 2023–2025 the era of “The Great SaaS Rationalization,” as organizations have been working to trim bloated portfolios.
With your discovery data in hand, you can approach that process with evidence instead of guesswork.
Insight 3: Unsanctioned apps (shadow IT)
Almost every audit uncovers unsanctioned tools that employees rely on; the popular apps that slipped past IT’s radar. A design team might have adopted a new platform because it fits their workflow better than the official tool, or a sales group may be using an independent CRM to move faster.
These aren’t always bad decisions; in fact, research shows shadow IT apps often see higher engagement than sanctioned ones because employees choose them themselves.
Action 3: Assess and onboard or eliminate
The right response isn’t to shut these tools down blindly, it’s to evaluate them. If an app provides real value and has strong adoption, IT should consider formalizing it. That means negotiating an enterprise contract, integrating it with SSO, and applying the necessary security and compliance controls.
If, on the other hand, the tool is redundant or introduces risk, IT should guide teams toward an approved alternative and phase it out.
The key is engagement. Users need to know that IT isn’t trying to ban their favorite apps arbitrarily, but to ensure they’re safe, compliant, and efficient for the entire company.
Shadow IT usually appears to fill a gap. If IT can address that gap—either by officially supporting the same app or by offering a better alternative—everyone wins.
Alongside this, strengthen policy and education so employees understand the risks of unapproved tools and are more likely to involve IT before the next adoption.
Insight 4: High-cost apps with unclear ROI
Big-ticket SaaS platforms often surface during an audit—CRMs, ERPs, or other enterprise software with hefty price tags. When usage is low, that’s a red flag.
It usually signals one of two problems: either adoption never took hold because users weren’t properly trained, or the tool simply doesn’t fit the way teams actually work.
Action 4: Evaluate value versus cost
These cases demand scrutiny. Work with the business owners of those tools to decide whether the platform is worth investing in or whether it’s time to scale back. If the tool is strategic, a re-launch or focused training may drive the adoption it needs.
But if usage remains stagnant, downsizing the contract is the smarter move. Even trimming 10% of unused seats on a high-cost app can save significant money.
It’s also worth looking across departments for duplication at the enterprise level. If two teams are paying for different premium tools that solve similar problems, standardizing on one platform and negotiating an enterprise deal can deliver major savings and simplify support.
High-cost apps aren’t just another line item, they’re a lever for either wasted spend or strategic efficiency, depending on how you manage them.
Insight 5: Team-specific tools
Audits often reveal team-specific tools tucked away in silos—an HR department running its own niche HR-tech platform or a small engineering group paying for a specialized dev tool. On their own, these apps may not look like major risks. But left unmanaged, they create mini SaaS islands that fragment data, duplicate spend, and escape oversight.
Action 5: Bring them into the fold
The solution isn’t always elimination. Sometimes the right move is to bring these tools into the fold. That might mean integrating the HR app into your broader IT environment, ensuring it has proper data backups and security reviews.
In other cases, IT may already have an approved alternative that the team simply wasn’t aware of. Even cataloging the tool in your central inventory and assigning it an owner can be enough to reduce risk because now it’s visible and accountable.
Critical niche apps should always have a clear business owner and an IT review for security. Non-critical ones, on the other hand, may be candidates for phasing out or consolidating into larger, sanctioned platforms.
The point isn’t to strip teams of the tools they need, but to prevent every department from building its own isolated ecosystem. By folding these tools into a managed framework, IT ensures agility for teams without sacrificing governance and efficiency.
The real value of discovery comes when you take the data back to the business. Share your SaaS inventory with department heads, show them where licenses are sitting idle, where spend can be reduced, and where risk is hiding in plain sight. Then align on next steps—whether that’s cutting redundant tools, consolidating overlapping platforms, or investing in apps that clearly deliver value.
This is where visibility turns into leverage.
Instead of being the IT manager chasing down mystery charges on the company card, you become the strategist who brings solutions to the table. Be the guy that points leadership in the right direction by saying:
“We identified a tool no one is using… Eliminating it will save $50,000,”
OR
“We found the design team using an unsanctioned app. Let’s bring it under governance so they can keep working productively and securely.”
Armed with data, IT can shift from being a reactive gatekeeper to a proactive partner. They can drive cost control and improve security, all while enabling the business to move faster with confidence. Plus, you get to be the star employee in the leadership’s books because you’re solving their real challenges.
Bonus: Tools that automate SaaS visibility
Building and maintaining a SaaS inventory isn’t a one-time project, it’s an ongoing responsibility. SaaS sprawl never stops, and visibility fades fast if you’re relying on static spreadsheets. Manual updates can work for a while, but they demand constant discipline and quickly fall behind reality.
That’s why many mid-market IT teams turn to SaaS Management Platforms (SMPs) or IT Asset Management (ITAM) tools with SaaS discovery features. These platforms automate the heavy lifting—pulling in new apps, identifying usage patterns, and automating SaaS renewals in real time—so IT isn’t chasing shadows.
The impact of using a SaaS management tool can be significant.
If the steps outlined above feel daunting to maintain manually, the good news is that the right tools make “visibility without effort” possible.
Here are some of the capabilities to look for when evaluating platforms:
- Browser activity tracking: Real-time monitoring of SaaS logins and domains through lightweight browser extensions. This is how you surface shadow IT as it happens, without relying on surveys or guesswork.
- API and SSO integrations: Connections to systems like Okta, Azure AD, Google Workspace, or Office 365 pull in sanctioned apps and OAuth-connected tools automatically. Agentless discovery means you don’t need to deploy SaaS management software on every endpoint.
- Finance system integration: Direct links to expense or accounting systems highlight when new vendors start getting paid, catching shadow purchases that slip past IT.
- Central SaaS inventory dashboard: A live, always-up-to-date view of every app, with usage metrics, costs, and risk indicators. Instead of spreadsheets, you get a system you can filter by department, spend, or compliance risk.
- Risk scoring and compliance checks: Automated assessments that flag which apps lack MFA, fail GDPR requirements, or have a history of breaches so you know where to focus first.
- Alerts and automation: Notifications when a new app appears, when usage spikes, or when access should be revoked. Advanced tools even trigger workflows such as alerting a department head when their team adopts an unapproved tool or disabling access when an employee leaves.
With these capabilities in place, IT moves from reactive cleanup to proactive control. Instead of chasing down what’s already slipped through, you’re watching SaaS adoption in real time. You’re ready to cut waste, reduce risk, and support the apps that truly add value.
Several players now compete in the SaaS Management Platform (SMP) space, each with its own strengths.They have carved out niches—some lean heavily toward security, others toward spend optimization or workflow automation.
At the same time, traditional IT Asset Management suites are expanding into SaaS. AssetSonar, for example, combines hardware and software asset tracking with SaaS discovery, integrating with systems like Google Workspace and Okta to keep your inventory current. The result is a single pane of glass where IT can monitor licenses, usage, compliance, and costs across the entire technology landscape.
The real advantage of these platforms is effort reduction. They operationalize the steps we’ve just walked through—continuous discovery, automated inventory, and even remediation workflows such as alerts when usage dips or when a new shadow app appears.
For mid-sized organizations with 500 or more employees and a growing SaaS footprint, the payoff is often immediate. The savings from cutting waste and the risk reduction from catching shadow IT early can more than cover the cost of the platform. With the right platform in place, IT shifts from chasing surprises to running a proactive, data-driven SaaS strategy.
Want to see complete SaaS visibility loop in action?
Final thoughts: SaaS visibility equals leverage
2025 isn’t the year of one-off SaaS audits. It’s the year of continuous discovery. Think of it this way: an annual audit is like snapping a photo of an airport terminal, it tells you what’s happening in that instant but an hour later it’s already out of date. Continuous discovery is live radar. It lets IT see every flight taking off and landing in real time. With that radar in place, you don’t just spot shadow IT—you gain leverage to spend smarter, secure faster, and support your teams better.
In today’s cloud-first world, visibility isn’t optional. You can’t optimize, secure, or govern what you can’t see. Complete SaaS visibility transforms IT from playing whack-a-mole with surprise renewals and rogue apps into proactively steering the stack. Costs come down, risks shrink, and waste gets eliminated. The difference is night and day.
And here’s the good news: you don’t need a huge IT department to get there. A lean team with the right tools and real-time visibility can outperform larger teams still flying blind.
When you’re not chasing down invoices or begging teams for app lists, you can focus on higher-value work by negotiating smarter contracts, improving adoption of critical platforms, locking down security controls, and enabling employees with the right tools.
In short, visibility gives you leverage: the power to say yes to innovation without losing control.
In a time of tight budgets and heightened security expectations, achieving control without complexity isn’t just possible. It’s becoming the new baseline.
And automation makes this sustainable.
By investing in continuous discovery—whether through SaaS management platforms or integrated IT systems—you can create a radar that pays for itself many times over in avoided surprises and reclaimed spend.
The path forward is clear: Set up your radar, keep discovery continuous, and use visibility as your lever for cost control, security, and agility.
With the steps in this guide, you’re ready to shine a light on your SaaS stack and turn that visibility into real business impact.