What is shadow IT and why does it matter?
Shadow IT refers to any IT technology, including hardware, software, or cloud-based tools, that employees use for work without approval from the IT team.
This includes:
- Personal devices
- Messaging platforms
- File-sharing services
- Productivity apps that are not officially authorized.
- Unapproved SaaS subscriptions
- Free or trial apps installed by employees
- Devices bought by individual teams (BYOD or unmanaged endpoints)
- Browser-only tools that IT cannot track manually
Some common examples of shadow IT are listed below:
- Employees are creating their own accounts on third-party apps to complete tasks faster, rather than using the proper channels. This could mean using cloud storage like Google Drive or Dropbox, communication apps such as WhatsApp or Slack, or project tools like Trello or Asana, all without IT visibility.
- Shadow IT also happens when employees use personal laptops, phones, or tablets for work without following approved BYOD policies. In most cases, shadow IT emerges because employees feel the unofficial tools are quicker or more convenient than the ones provided.
Shadow IT: A growing risk for IT teams
Shadow IT is becoming one of the fastest-growing risks within modern IT environments. It often spreads quietly and soon becomes a serious risk. As more and more mid-market organizations depend on cloud apps, AI tools, and distributed workforces, unsanctioned applications and devices continue to infiltrate IT networks, often with good intentions but with dangerous consequences.
When decentralized purchasing increases and employees install tools on their systems without IT approval, the threat of shadow IT grows, and the attack surface widens dramatically. What was once a minor nuisance for the organizations is now a major audit, compliance, and security concern.
Startling statistics about Shadow IT
In today’s world, this problem has become so pervasive that:
- 41% of tech spend in mid-market companies now happens outside IT budgets. (Gartner)
- 59% of IT teams remain concerned about Shadow IT in 2025 (Better Cloud)
- The average company uses 130+ SaaS apps, but IT teams estimate that fewer than half of them are in use. (BetterCloud)
- 42% of company applications are driven by shadow IT. (Productiv)
- 85% of global businesses have experienced cyber incidents over the past two years, with 11% attributed to the use of unauthorized shadow IT. (Infosecurity Magazine)
This is precisely why automated discovery is emerging as a must-have capability in an IT Asset Management (ITAM) solution. Manual spreadsheets or periodic scans fail to keep up, especially when an audit is around the corner.
Eliminating Shadow IT is now a must for every IT manager. When teams use tools without approval, it puts your organization at risk, from data leaks to breaking new compliance rules. The only way to stay protected is to have real-time visibility of every device and application on your network, whether approved or not, so you can stay in control and keep your organization secure.
In this blog, we will discuss how leading ITAM solutions, including EZO AssetSonar, catch shadow IT before audits, and which automated discovery capabilities really matter. We’ll also compare how top ITAM platforms uncover hidden IT assets before audits uncover them for you.
Detect Shadow IT Before Audits
The hidden threat that shows up at audit time
As IT teams prepare for vendor true-ups, SOC 2 reviews, ISO audits, or internal compliance checks, the same old pattern emerges:
Shadow IT shows up at the worst possible time, i.e., during audits.
Unsanctioned cloud apps. Unknown endpoint software. Devices the IT team didn’t know existed. Missing software licenses. Installed-but-unlicensed software. And, worst of all: A mismatch between what the organization thinks it owns and what the auditor sees during audits.
Automated discovery tools are now the differentiating factor between IT teams that walk into audits confidently and those who spend weeks scrambling to reconcile unknown assets.
Why Shadow IT is a serious problem for ITAM
Shadow IT creates multiple layers of risk. Here’s why shadow IT is a growing problem for ITAM:
1. Audit non-compliance
Unapproved software isn’t included in license counts, which can lead to heavy penalties during vendor audits.
Consider this example: A marketing team installs paid video editing apps without IT approval. During an audit, the company is billed for 25 unlicensed users it didn’t know existed.
2. Security gaps
Shadow IT bypasses IT security controls, making it easier for unpatched or unsecured apps to be exploited.
Consider this example: An employee downloads a free note-taking app that isn’t monitored. A few days later, a vulnerability exposes internal meeting notes and project details.
3. Data privacy risks
When employees use tools not reviewed by legal or compliance teams, sensitive data may be stored in unsafe or non-compliant locations.
Consider this example: HR uploads employee IDs to a free cloud service that stores data outside approved regions, triggering privacy and regulatory concerns under GDPR or HIPAA.
What is the role of automated discovery in ITAM
Manual spreadsheets. Quarterly audits. Occasional network scans.
All of these worked when IT environments were predictable and contained. However, today’s IT landscape includes remote devices, SaaS creep, hybrid cloud, personal laptops, shadow SaaS, and decentralized purchasing.
What’s the end result? Assets appear and disappear on a daily basis, far too quickly to be able to track them manually.
Modern IT teams need automated discovery: uninterrupted, continuous, and real-time detection of every asset in the environment, including the ones IT never knew existed.
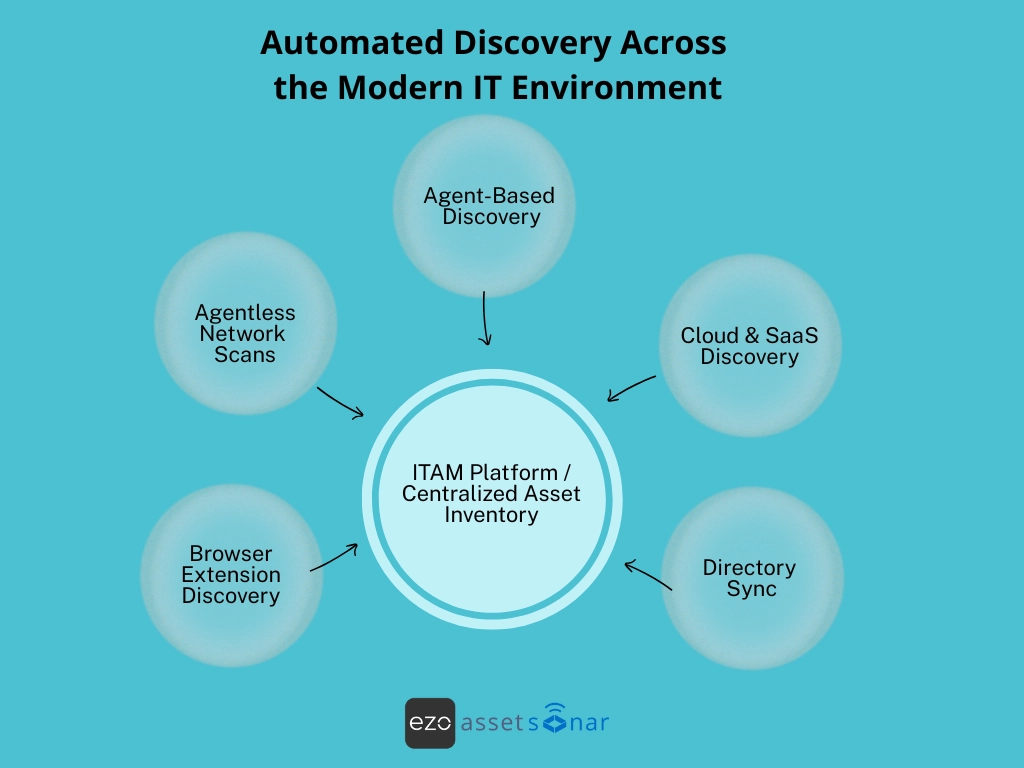
How automated discovery works
Most leading ITAM platforms combine multiple discovery mechanisms to provide complete visibility to the mid-market IT teams. Here’s how:
1. Agent-based discovery
Lightweight agents installed on endpoints detect:
- Installed software
- Hardware specs
- Usage activity
- Device health
Consider this example: An engineer installs a trial version of an unlicensed video editing tool on a company laptop. An agent flags the install immediately, preventing a surprise during a vendor audit.
2. Agentless network scans
Network probes detect:
- New devices connecting to the network
- Unregistered IPs
- Printers, switches, and other peripherals
Consider this example: A contractor brings a personal laptop to the office and connects it to the office Wi-Fi network. The system detects an unknown device instantly, alerting IT before sensitive access occurs.
3. Cloud & SaaS discovery via APIs or OAuth
The tool connects to cloud services to detect:
- All approved SaaS apps
- Hidden accounts created without IT
- OAuth-connected apps employees authorize through Google or Microsoft
Consider this example: The marketing team signs up for a design SaaS using Google SSO. The ITAM tool picks up the new OAuth connection, even though no one told IT about it.
4. Browser extension–based discovery
Captures SaaS tools that:
- Don’t require installation
- Run only in the browser
- Bypass traditional discovery methods
Consider this example: A team starts using a free AI transcription service. The browser extension logs usage, revealing shadow SaaS before it spreads.
5. Directory sync: Azure AD, Okta, Google Workspace
Identifies:
- Unmanaged users
- Orphaned accounts
- Accounts with excessive privileges
Consider this example: A former intern still has access to a paid SaaS product. Directory sync surfaces the stale account before renewal season.
Benefits of automated discovery
Let’s take a look at some of the benefits of automated discovery capabilities within an ITAM platform.
1. Real-time visibility of all assets: sanctioned and unsanctioned
With automated discovery within an ITAM tool, you can instantly see every device, app, license, and user, not just the ones IT already knows about.
Here’s an example: A retail company discovered 47 untracked Chromebooks, all active in stores but missing from their CMDB. Discovery corrected its entire hardware inventory before a PCI audit.
2. Early detection of unknown cloud apps and unauthorized installs
Automated discovery helps you catch shadow SaaS and unlicensed software before they trigger compliance penalties.
Here’s an example: A mid-market finance team detected 19 unapproved SaaS tools used by analysts, avoiding ~$96,000 in potential vendor audit penalties.
3. Accurate inventory for audits and license reconciliation
Audit failures often happen because the inventory in ITAM does not match what exists in reality. This is where automated discovery helps. It accurately detects inventory for audits and license reconciliation.
Here’s an example: A tech company performing a Microsoft True-Up found 72 devices with Office installed but without a license assigned. Automated discovery helped reconcile counts before the auditor did.
4. Improved security posture by identifying unmanaged endpoints
Unmanaged devices, personal laptops, tablets, or outdated hardware often bypass patching cycles, MFA, and security protocols, making them easy targets for attackers. Automated discovery scans every device in real time, helping IT teams detect unauthorized endpoints, enforce policies, and secure them before they become a risk.
Here’s an example: A healthcare provider located six unmanaged laptops used by remote clinicians, devices that had access to patient data but no encryption. Automated discovery helped secure them before the HIPAA inspection.
Automated discovery doesn’t just catch shadow IT; it prevents audit gaps, compliance failures, surprise true-ups, and the costly, last-minute scramble IT teams experience every year.
How leading ITAM platforms catch shadow IT before audits
Here’s a breakdown of leading ITAM platforms and how they detect unknown assets.
Strength: Hybrid discovery across SaaS, cloud, on-prem, endpoints, and identity systems
Some ITAM platforms offer comprehensive hybrid discovery across all asset types, including cloud apps and SaaS tools, as well as hardware endpoints and unmanaged devices. These solutions continuously uncover:
- Unapproved SaaS applications accessed through browser sessions or via OAuth and SSO logs, offering deep visibility into shadow IT at the SaaS layer.
- Installed software on unmanaged, off-network, or missing devices that are otherwise outside of the IT team’s visibility, reducing the risk of unknown asset usage.
- Assets not registered in identity systems like Azure AD or Okta, which ensures that even shadow hardware is tracked correctly.
- Cloud apps that employees connect to without any IT involvement, potentially causing licensing and compliance issues.
What sets these platforms apart is correlation; they automatically link users, devices, software, and licenses, providing IT teams with a forensic-level view of shadow assets and their rightful owners. This eliminates the audit scenario where IT knows an app or device exists but cannot identify who is using it or why it was installed.
Pros:
- Provides visibility across hybrid environments (SaaS, endpoints, cloud)
- Strong automated discovery for both hardware and software
- Deep SaaS detection through identity, OAuth, browser logs, and usage insights
- Clean, modern UI preferred by mid-market teams for simplicity and ease of use
- Fast onboarding and lower total cost of ownership compared to complex, enterprise-focused solutions
Cons:
- Requires integrations (Azure AD, Okta, Intune, GSuite, etc.) for maximum SaaS discovery depth.
Ideal For:
Mid-market IT teams need deep visibility across all asset types, especially those preparing for vendor audits, SOC2, ISO, or internal compliance checks.
Strength: AI-powered device and software discovery engine
Some ITAM platforms leverage AI and machine learning to detect rogue or unknown assets more efficiently. These platforms:
- Autonomously manage endpoint devices and software discovery across distributed teams, including mobile devices and endpoints.
- Help identify unauthorized software installations, prioritizing the greatest risks to compliance and security.
- Use AI-driven vulnerability correlation to ensure shadow IT risks (such as unmanaged software) are quickly addressed.
This AI-powered approach helps IT teams reduce false positives, allowing them to focus on the shadow IT that poses the greatest threat to the organization’s security and compliance posture.
Pros:
- Ideal for large, distributed fleets needing continuous endpoint monitoring
- Strong vulnerability correlation tied to shadow software and unmanaged endpoints
- Best for organizations already using endpoint management and security systems for deeper integration
Cons:
- SaaS discovery is more limited compared to specialized ITAM platforms.
- Higher complexity and a heavier deployment footprint are required for large organizations.
- More suitable for enterprise-level teams with dedicated security operations.
Ideal For:
Organizations requiring deep endpoint intelligence, risk prioritization, and vulnerability mapping, but may not prioritize SaaS-first visibility.
Strength: Integration of ITAM, ITSM, and change management
For enterprises that integrate IT asset management with ITSM (IT Service Management) and change management processes, certain ITAM platforms offer strong data reconciliation:
- Shadow IT is detected by comparing incident history, change requests, and configuration management database (CMDB) relationships.
- Platforms track configuration items (CIs) and identify exceptions through IT workflows, providing visibility into unauthorized or unmanaged assets.
These platforms are highly effective for organizations where ITAM is tightly embedded into broader IT governance processes, ensuring all changes are logged and compliance is maintained. They integrate seamlessly with security operations and ITSM, making it easy to detect and manage shadow IT.
Pros:
- Excellent for enterprises that require strict CMDB alignment and strong integration with ITSM and change management
- Deep integration with ITSM workflows, enabling seamless shadow IT detection and management
- Highly configurable workflows for audit preparation and tracking asset changes
Cons:
- Discovery capabilities can be complex and require dedicated administration.
- SaaS discovery often needs additional add-ons or integrations.
- High cost of ownership for mid-market teams and overkill for organizations that only need basic visibility.
Ideal For:
Large enterprises with mature CMDB practices that need ITAM tightly embedded within ITSM governance.
Catch Shadow It with EZO AssetSonar
Key features to look for in ITAM tools that catch shadow IT
To proactively detect shadow IT before audits, an ITAM platform must provide these essential capabilities:
1. Real-time discovery
Shadow IT appears and evolves continuously: an employee installs a trial app, signs in to a new SaaS tool, or connects an unmanaged device. Real-time discovery ensures IT teams see these changes as they happen, not weeks later during an audit cleanup. Continuous detection allows teams to resolve issues before they become compliance risks.
Let’s consider this example. A finance analyst installs a free PDF editor that isn’t licensed for commercial use. Real-time discovery flags the installation immediately, allowing IT to remove it. This prevents a violation during the company’s upcoming vendor audit.
2. Cross-platform visibility
Shadow IT isn’t limited to one system; it spans endpoints, mobile devices, SaaS accounts, cloud services, and browser-only applications. An effective ITAM platform must track everything across the technology stack so nothing falls through the cracks. This holistic visibility ensures IT knows what exists, where it lives, and who uses it.
During pre-audit review, IT discovers 12 unmanaged Chromebooks used by contractors; detected via network scans and directory mismatches. Without cross-platform visibility, these devices would have remained invisible, exposing the company to SOC 2 audit findings.
3. Security integration
Shadow IT is not just an asset management problem; it’s essentially a security problem. Integrations with SIEM, identity providers (Azure AD, Okta), MDM, and EDR systems allow ITAM tools to assess whether a discovered asset is risky. When security signals merge with asset visibility, IT can quickly decide which findings require escalation.
A newly detected laptop missing from IT’s inventory also appears in the company’s EDR alerts for outdated antivirus software. The ITAM system correlates both signals, allowing IT to quarantine the device before auditors flag it as an unmanaged endpoint.
4. Custom alerts
Custom alerting ensures IT teams are notified instantly when shadow IT emerges, whether it’s a new SaaS app accessed, an unapproved installation, or a license count nearing its limit. These alerts prevent issues from accumulating quietly until audit time. They also help automate SaaS governance, reducing reliance on manual checks.
A custom alert notifies IT whenever an employee signs in to a new SaaS platform. One alert reveals that HR staff began using a document-signing tool without a security review, allowing IT to intervene before sensitive documents are processed through an unapproved system.
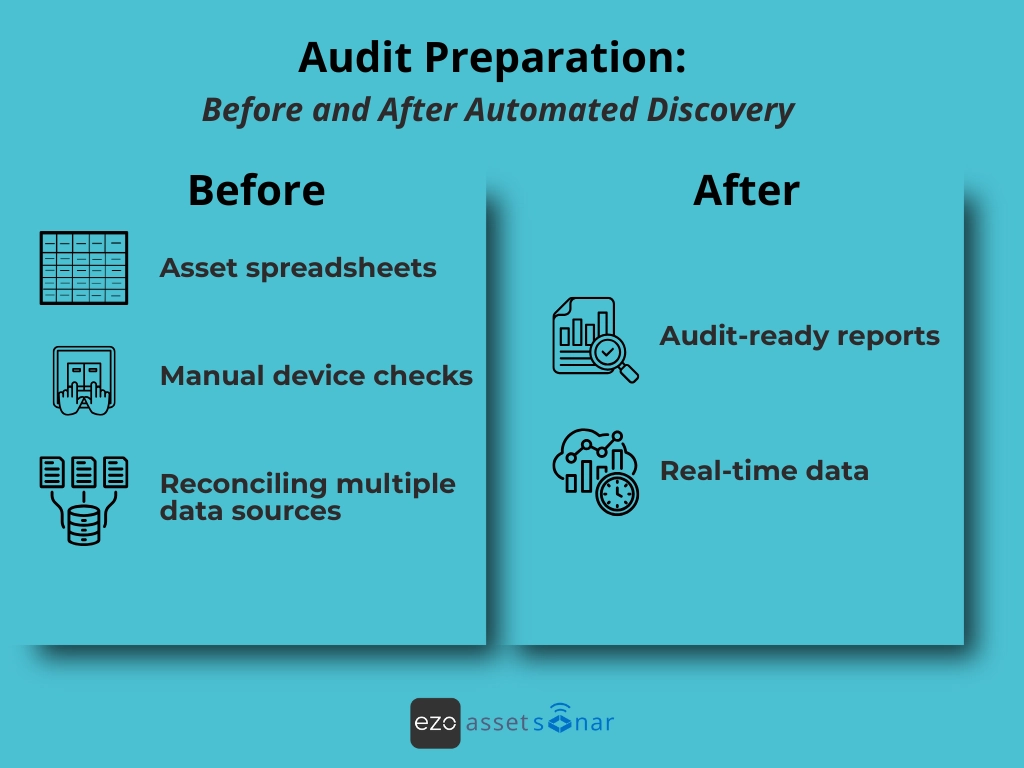
5. Audit-ready reporting
Audits require clean, structured, defensible data. ITAM tools that generate exportable, time-stamped, audit-ready reports eliminate the scramble of pulling data from multiple systems. These reports show auditors exactly what assets exist, how they’re licensed, and how shadow IT risks were mitigated.
Before a Microsoft True-Up, the IT team exports a software inventory report showing all active installs, license assignments, and compliance status. Because automated discovery captured unauthorized installs earlier, the final audit report shows zero discrepancies, avoiding penalties.
How automated discovery streamlines audit preparation
Automated discovery transforms audits from a frantic, last-minute scramble into a predictable, data-driven process. Instead of digging through outdated spreadsheets or guessing which assets are still in use, IT teams walk into audits with clear, verifiable evidence.
Audit-ready reports
Automated discovery tools generate accurate, up-to-date reports that auditors expect to see, including:
- Installed software lists
- License assignments and usage
- SaaS access logs
- Hardware inventory across locations
- Change history and configuration trails
Because all of this data is timestamped and system-generated, auditors trust it far more than manually compiled documents.
Consider this example: Before a Microsoft True-Up, an IT team exports an automated report showing exactly which users have Office installed and how many licenses are active. Since discovery had already flagged unlicensed installs earlier, the audit closes with zero compliance fees.
Reduced manual inventory work
Without automated discovery, teams spend weeks reconciling spreadsheets, walking through offices to check serial numbers, and pulling data from multiple systems. Automated discovery eliminates this operational burden by providing a single source of truth.
Consider this example: A mid-sized healthcare organization cut its audit prep time from 6 weeks to 2 days after automated scans replaced physical device checks and manual software lists. What once required cross-checking five different spreadsheets now happens with a single click.
With continuous discovery feeding real-time data into ITAM, audits shift from reactive firefighting to a routine validation step. The process becomes predictable, far less stressful, and grounded in live system data—not human memory, departmental spreadsheets, or last-minute guesswork.
Check out this before vs. after visual to make the transformation even clearer.
Challenges of automated discovery and how tools overcome them
Even the most advanced discovery engines face limitations, especially in hybrid environments where assets move fluidly across networks, browsers, and cloud services. Here are the most common challenges and how leading ITAM platforms are addressing them.
Challenge 1: Detecting cloud-only SaaS tools
Cloud tools that require no installation and run entirely in the browser are the hardest to detect. Employees can purchase SaaS apps with personal credit cards, use free trials, or log in using their work email, all without IT involvement. These tools never appear in traditional network scans or local software inventories.
How tools overcome it: Modern ITAM platforms use browser-level discovery, OAuth monitoring, and SSO integrations with providers like Azure AD or Okta to capture these “invisible” applications. This approach surfaces shadow SaaS usage early, allowing IT to assess risk and enforce governance before audits flag a violation.
Challenge 2: False positives in large or complex networks
In high-volume environments, network discovery can generate redundant or misleading records, duplicate IP addresses, misidentified devices, stale entries, or software signatures that appear similar. Without intelligent filtering, these false positives create noise and slow down compliance processes.
How tools overcome it: Platforms like Ivanti use AI-assisted filtering to analyze patterns and suppress redundant findings, while solutions like AssetSonar combine discovery data with identity correlation (user → device → software). This makes results more accurate and reduces the manual cleanup IT teams typically face before audits.
Challenge 3: Unmanaged or BYOD endpoints
Remote work, contractors, and BYOD policies introduce devices that are not enrolled in MDM, not domain-joined, and not consistently visible to network scans. These endpoints often fall outside IT policies, creating blind spots that auditors can quickly exploit.
How tools overcome it: Modern ITAM solutions bridge the visibility gap through directory sync, MDM integrations (e.g., Intune, Jamf, Kandji), and EDR visibility. By correlating discovery data with identity management and endpoint security platforms, IT teams can identify unmanaged devices and enforce compliance before they become an audit liability.
In short, AI, identity mapping, browser-level visibility, and deeper cloud integrations are closing the historical gaps in automated discovery. As these capabilities evolve, ITAM platforms can detect more shadow IT earlier, reducing surprises, compliance risks, and last-minute audit remediation work.
Case Study: Real-world shadow IT detection
How Stellar eliminated shadow IT blind spots with a leading ITAM solution
Stellar, a fast-growing design-build construction firm, struggled to keep up with a rapidly expanding IT estate. Excel spreadsheets couldn’t capture real-time changes, leading to missing devices, untracked software, inconsistent records, and siloed inventories; all major risks before internal audits.
Implementing EZO AssetSonar, one of the leading ITAM solutions, gave Stellar instant, unified visibility across its entire hardware and software footprint. Automated discovery immediately exposed assets that spreadsheets had missed, surfaced software installs the IT team didn’t know existed, and revealed devices assigned to users who had already offboarded.
How an ITAM helped Stellar get audit-ready:
- Automated discovery uncovered missing and duplicate devices, allowing IT to recover items previously “lost” in Excel.
- Unified visibility broke down siloed asset lists, consolidating two separate IT groups into a single source of truth.
- Integrations with Zendesk, Intune, Okta, and Azure revealed unmanaged devices and software, tightening compliance gaps.
- Audit-ready reports cut inventory verification time from 1.5 days to 20 minutes, reducing manual labor and human error.
- Proactive license and renewal alerts prevented compliance issues, ensuring no contract slipped through unnoticed.
With an ITAM solution, Stellar increased IT productivity from 25% to 100%, eliminated shadow IT blind spots, and gained the visibility needed to pass audits with confidence.
Conclusion: Why automated discovery is now essential for catching shadow IT
As already mentioned, Shadow IT is no longer a fringe problem; it’s a systemic risk that affects audits, security posture, licensing costs, and operational compliance.
Automated discovery is the only scalable way to:
- Identify unknown software
- Track unmanaged devices
- Detect unapproved SaaS apps
- Prepare for audits
- Reduce financial liability
Mid-market and enterprise IT teams need tools that can see everything, not just what IT already knows about.
If you want to uncover hidden assets, eliminate licensing surprises, and prepare confidently for audits, now is the time to explore automated discovery platforms like EZO AssetSonar, which brings together hybrid discovery, identity correlation, SaaS visibility, and compliance reporting into one unified system.





